Hey there! Let's talk about guest Wi-Fi. Let's be honest, offering it isn't just a nice perk anymore; it’s pretty much a non-negotiable part of doing business today. But knowing how to set up guest Wi-Fi the right way goes far beyond just taping a password to the counter. It's about crafting a secure, branded, and completely seamless experience for your visitors, whether they're in a busy Retail shop, a sprawling Education campus, or a corporate office that fully embraces a BYOD policy.
Why a Professional Guest Wi-Fi Matters

That simple act of providing an internet connection has evolved into a crucial touchpoint between your organization and your visitors. A basic, password-protected network just doesn't cut it in today's world. It's often insecure, a headache to manage, and offers zero opportunity to engage with your guests or reflect your brand's commitment to quality.
A professional setup, however, flips the script, turning a simple utility into a powerful strategic asset. Think of your guest network as a digital welcome mat—it’s often the very first impression visitors will have of your tech-savviness and attention to detail. This is where high-performance systems from vendors like Cisco Meraki really come into their own, giving you the tools to deliver much more than just a connection.
From Basic Access to Strategic Advantage
In a bustling Retail environment, a thoughtfully designed guest network is a marketing workhorse. By using an engaging Captive Portal, a store can flash special offers, gather valuable marketing opt-ins, or guide shoppers to its e-commerce site, directly influencing sales. The entire goal is to transform a casual browser into a repeat customer.
Meanwhile, in the Education sector, managing thousands of student and guest devices is a daily tightrope walk. A single password simply can't provide the control or security needed. Here, professional Authentication Solutions are vital for separating access between students, faculty, and temporary visitors, creating a secure BYOD environment where personal devices pose no threat to the core school network.
The difference boils down to control and experience. A professional guest network gives you fine-grained control over who accesses your network and what they can do, all while presenting a polished, branded interface.
Security is the top priority in a BYOD Corporate setting. When vendors, clients, or contractors need to connect, you must provide reliable internet without ever exposing sensitive internal resources. This is where advanced solutions like IPSK (Identity Pre-Shared Key) or EasyPSK offer a much safer alternative to a single, shared password. Each user or device gets its own unique key, which makes granting and revoking access incredibly simple and secure.
The growing emphasis on these platforms is clearly reflected in market trends. The global guest Wi-Fi platform market was valued at roughly USD 1.7 billion in 2023 and is expected to surge to USD 4.1 billion by 2032. As you can see from market research reports, businesses are taking this very seriously. It's no longer just about providing internet; it's about building a secure, managed, and valuable touchpoint for every single person who walks through your doors.
Guest WiFi Impact Across Different Sectors
A well-executed guest Wi-Fi strategy isn't a one-size-fits-all solution. The goals and benefits vary significantly depending on the industry.
|
Sector |
Primary Goal |
Key Benefit |
|---|---|---|
|
Retail & Hospitality |
Enhance Customer Experience & Drive Sales |
Collect marketing data, push promotions, and build brand loyalty through a branded portal. |
|
Education |
Secure Network Access & Management |
Safely manage thousands of BYOD devices for students and staff while keeping guests isolated. |
|
Corporate Offices |
Secure Visitor & Contractor Access |
Provide seamless internet for guests without exposing the internal corporate network. |
|
Healthcare |
Improve Patient & Visitor Experience |
Offer simple, reliable access for patients and their families while maintaining HIPAA compliance. |
Ultimately, tailoring your guest Wi-Fi to your sector's specific needs is what turns a basic utility into a real competitive advantage.
Planning Your Guest Wi-Fi with Cisco Meraki
Before you even log into the Cisco Meraki dashboard, it's worth taking a step back. A truly effective guest Wi-Fi network is more than just a signal; it's a carefully planned experience that should directly support your business goals. Getting the strategy right upfront makes the technical setup a breeze.
Think of it like laying the foundation for a house. You need to answer a few critical questions that will guide every decision you make down the line. This is true whether you're a coffee shop trying to boost customer loyalty, a school managing a complex BYOD environment, or an enterprise office that needs to welcome visitors securely.
Start with Your Core Objectives
First things first: why are you offering guest Wi-Fi in the first place? Is it just a basic courtesy, or do you have a bigger vision?
-
Retail & Hospitality: Your goal might be to capture marketing insights with an interactive Captive Portal. Maybe you want to display daily specials or understand foot traffic.
-
Education: Here, the priority is almost always managing thousands of devices safely. You'll need powerful Authentication Solutions to segment student, staff, and visitor access and protect your core network.
-
Corporate Offices: Security is paramount. The mission is to give guests internet access while keeping them completely isolated from internal resources, which makes solutions like IPSK a top contender.
The answers you come up with here will shape everything from the look of your splash page to the security protocols you put in place.
A great guest network is a two-way street. It should offer a seamless connection for your visitors while also delivering real, measurable value back to your organization.
Sizing Up Your Network Needs
Once you've nailed down the "why," it's time to figure out the "how much." Accurately estimating your usage is the key to avoiding a sluggish, frustrating experience for your guests. Think about your peak times—how many people do you expect on your busiest day? The needs of a small cafe are worlds apart from a university campus during exam season.
This initial planning helps you configure the fundamentals in the Cisco Meraki dashboard, like naming your SSID and setting up traffic shaping rules. For instance, you can set a bandwidth limit for each user. It’s a simple but effective way to ensure one person streaming 4K video doesn’t grind the network to a halt for everyone else who just wants to check their email.
You can also use these rules to protect your own operations. Prioritizing your business-critical applications means guest activity will never slow down your point-of-sale systems or other essential tools. This separation is fundamental.
Finally, consider your security from the very beginning. Is a simple click-through agreement enough, or do you require something more robust? For most corporate or Education environments, a shared password just doesn't cut it anymore. Looking into stronger Authentication Solutions like EasyPSK early on ensures you build a network that's as secure as it is welcoming right from the start.
Designing an Engaging Captive Portal
Think of your captive portal, or splash page, as your digital handshake. It’s the very first interaction a guest has with your network and, by extension, your brand. This is your chance to make a great first impression, so let's move beyond the generic login screen. We'll design a portal within Cisco Meraki that feels both welcoming and works hard for your business.
This isn't just about making things look pretty; it's a strategic touchpoint. A well-designed portal should instantly reflect your brand's identity—your logo, colors, and messaging should be front and center. It also needs to clearly present your terms of service and offer a few simple ways for people to get online without a headache.
More and more businesses are seeing guest Wi-Fi as a real asset, which is why the market is projected to grow at a steady CAGR of 5.7% from 2025 to 2033. They're realizing it’s not just about providing internet access anymore. It’s a powerful tool for enhancing the customer experience and gathering valuable insights.
Tailoring the Portal to Your Audience
A one-size-fits-all splash page simply doesn't work. To be effective, your design and messaging have to be tailored to your specific environment and the people using it. Different industries have completely different goals.
-
Retail: A clothing boutique could use its captive portal to show off a new collection with a bold hero image. Maybe it features a countdown to a special event or a QR code for an instant 10% discount. Suddenly, the login process becomes a marketing win.
-
Education: A university can use its portal to push out timely updates. Think campus event schedules, links to important student resources, or a welcome message for new arrivals during orientation week. The focus shifts to communication and building a sense of community.
-
Corporate BYOD: In an office setting, professionalism and clarity are everything. The splash page should offer a polished, branded welcome that reassures visitors. It’s the perfect spot to reinforce security policies and walk guests through a simple, sponsored login.
Your captive portal is a blank canvas, not just a login button. Use that space to give your guests something valuable while also hitting your own business goals.
Essential Authentication Solutions
Once you’ve nailed the visual design, it's time to choose the right Authentication Solutions. This is where you balance security with a smooth user experience. A simple click-through page is incredibly easy for users, but it offers almost no real security.
In more controlled environments, like a Corporate office or an Education campus, you'll need something more robust. This is where integrating secure yet user-friendly options becomes critical for building effective guest captive portals.
Technologies like IPSK or EasyPSK are fantastic for this. Instead of a single, shared password that everyone knows (and is a huge security risk), they provide unique credentials for each user. This dramatically boosts your network's security. By pairing a great design with the right authentication method, you create an experience that’s seamless for your guests and secure for your organization.
Choosing the Right Guest Authentication Method
How your guests actually log into your Wi-Fi is where the rubber meets the road. This is the critical moment where user experience shakes hands with network security, and finding the right balance is everything. We’ll explore some of the most common Authentication Solutions to help you figure out what’s best for your specific crowd and environment.
The options can be as simple as a click-through on a Captive Portal or more involved, like using social media logins or even a sponsored access system for corporate visitors. Each method has its place, but for organizations that are serious about security and control, the conversation quickly turns to more robust solutions. This is especially true in Education and corporate BYOD (Bring Your Own Device) settings.
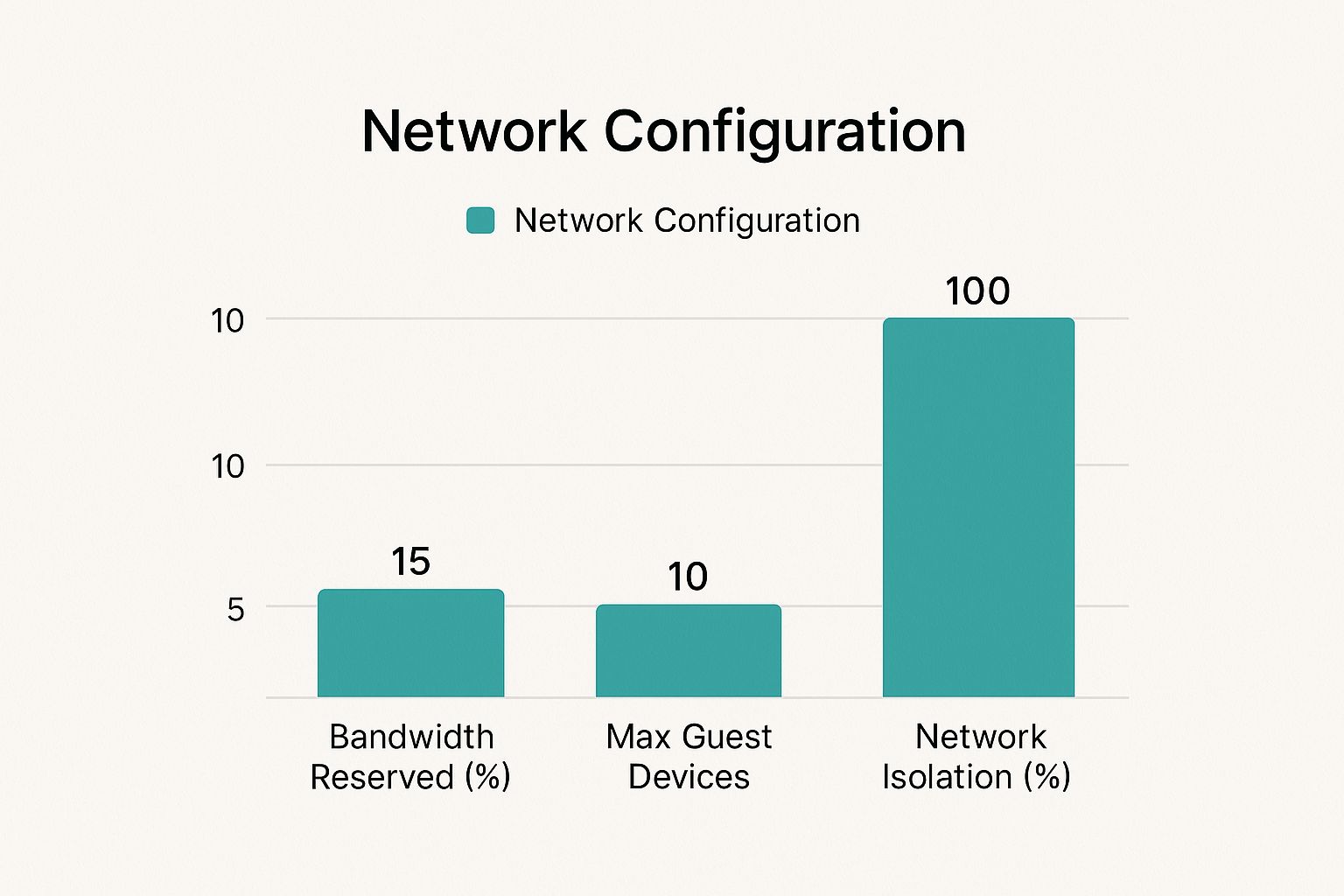
This diagram shows a few typical configurations for a guest network, illustrating how resources can be properly managed.
The most important thing to notice here is the 100% network isolation. Frankly, this is a non-negotiable security measure for any professional guest setup.
Beyond the Single Shared Password
Let's be blunt: handing out a single password for everyone to use is a security nightmare waiting to happen. It gets shared around, it’s a pain to change, and you have zero real control over who is on your network at any given time. This old-school approach is precisely why technologies like Identity Pre-Shared Keys (IPSK) were developed.
Instead of one password for all, IPSK gives each user or device its own unique key. Think of it like a hotel key card versus a single, ancient key for the entire building. This approach, which is fully supported by platforms like Cisco Meraki and made incredibly simple through services like EasyPSK, completely changes the game.
For a school campus, this means you can issue unique keys to students, faculty, and temporary guests, each with different access levels and expiration dates. When a student leaves, you just revoke their key without disrupting anyone else. The same logic applies to a corporate office managing a constant flow of contractors and clients in a busy BYOD setting.
The real power of IPSK and EasyPSK is that they deliver the granular control of enterprise-grade security (like 802.1X) without all the complexity. It’s the perfect middle ground for most organizations.
Matching Authentication to Your Environment
Choosing the right method comes down to your priorities. Are you a Retail store focused on marketing, or an Education institution focused on security? Answering that question will point you directly toward the best fit.
To make this choice clearer, let's compare the most common authentication methods. Each one serves a different purpose, balancing ease of use with the level of security you need.
Comparing Guest WiFi Authentication Methods
This table gives you a quick overview of common authentication methods to help you choose the best fit for your security and user experience needs.
|
Method |
Best For |
Security Level |
User Experience |
|---|---|---|---|
|
Click-Through |
Cafes, public venues, quick access |
Low |
Effortless, fastest connection |
|
Social Login |
Retail, hospitality, marketing |
Medium |
Simple, uses existing accounts |
|
Sponsored Access |
Corporate offices, managed environments |
High |
Secure, requires employee approval |
|
IPSK/EasyPSK |
Education, healthcare, BYOD-heavy offices |
Very High |
Secure & simple, device-specific |
As you can see, what works for a coffee shop is very different from what a school or corporate headquarters requires. It's all about matching the tool to the job.
Here’s a closer look at those scenarios:
-
Click-Through Access: This is the lowest-friction option. It’s perfect for cafes or public spaces where the main goal is to get people online fast after they accept your terms and conditions. Security is minimal, but the user experience is as easy as it gets.
-
Social Media Login: A fantastic choice for Retail and hospitality. It allows guests to log in using their existing social accounts. This not only simplifies the process for them but can also provide you with valuable, aggregated demographic data to better understand your customer base.
-
Sponsored Access: Ideal for corporate offices. A visitor requests access, and an internal employee—their sponsor—approves it. This approval often generates a unique, time-limited credential, adding a crucial layer of accountability.
-
IPSK/EasyPSK: The gold standard for Education, healthcare, and any BYOD Corporate environment. It offers the best blend of high-end security and real-world usability, letting you easily manage access for hundreds or thousands of individual users and devices.
Understanding these different approaches is a core part of building an effective guest Wi-Fi system. To explore these concepts in more detail, check out this excellent overview of various user authentication techniques that can be implemented with Splash Access. Choosing wisely ensures your network is both welcoming to guests and a fortress for your private data.
Securing Your Network and Your Guests
Alright, you've picked the perfect way for guests to log in. Now for the most important part: security. Getting guest Wi-Fi security wrong isn't a small mistake; it's a gaping hole that can put your entire business at risk. The real goal here is to build a fortress around your internal network while giving guests their own safe, sandboxed space to get online.
This is especially critical in any modern BYOD Corporate environment where dozens, if not hundreds, of personal devices are connecting every day. The first, and frankly non-negotiable, step is network isolation. Think of your internal and guest networks as two separate buildings. They might share a parking lot, but there are absolutely no doors connecting them. This is usually done with VLANs (Virtual Local Area Networks), and it's the bedrock of a secure setup.
Building Your Digital Fortress
Inside your Cisco Meraki dashboard, you have a powerful toolkit to enforce this separation and control exactly what your guests can and can't do. One of the first things I always recommend is setting up content filtering. You can easily block malicious websites, adult content, or those bandwidth-hungry streaming sites. This is a must-have for places like Education campuses or family-focused Retail stores.
Doing this creates a safer browsing experience for everyone and, just as importantly, reduces your liability. You're not just handing out an internet connection; you're providing a clean, protected one that reflects well on your organization. It's simply good network stewardship.
The core mission of guest Wi-Fi security is simple: protect your private data at all costs. Guest traffic should never have a pathway to your internal servers, POS systems, or confidential employee information.
Beyond just filtering content, you can get granular with firewall rules. These rules act like a digital bouncer, directing traffic flow. For instance, a smart move is to prevent guest devices from talking to each other, a feature often called client isolation. This one setting can stop a guest’s infected laptop from spreading malware to other visitors on your network.
This level of control is more crucial than ever. The Wi-Fi market is exploding, projected to nearly double from USD 22.06 billion in 2024 to USD 45.12 billion by 2029. As we all move toward faster standards like Wi-Fi 6 and 7, the need for rock-solid security to handle all those new devices and speeds becomes paramount.
Managing Access and Revocation
Good security doesn't stop once a guest has logged in. Even with solid Authentication Solutions like IPSK or EasyPSK, you need a way to manage device access over the long term. What happens when an employee loses a phone that still has valid credentials to access the network?
This is where a platform like Splash Access really shines. It gives you the visibility and control to see every single device connected with a unique EasyPSK key. If a device is lost, stolen, or just shouldn't have access anymore, you can revoke its key instantly. This capability goes far beyond the initial Captive Portal login.
By combining robust firewall rules, strict network isolation, and dynamic access controls, you create a guest network that’s both welcoming for your visitors and incredibly secure for your organization.
Common Guest Wi-Fi Questions Answered
When you're figuring out how to set up guest Wi-Fi, it's natural for questions to pop up. We get them all the time. Let's walk through some of the most common ones and give you the straight answers you need to get your guest network running perfectly.
What Is the Difference Between Guest and Regular Wi-Fi?
The single biggest difference is security through isolation. Think of a guest Wi-Fi network as a completely separate, walled-off internet connection built just for your visitors. It should always use a Captive Portal to manage who gets on and be firewalled from your primary internal network. This is non-negotiable for protecting your sensitive business data.
Your regular Wi-Fi, on the other hand, is the trusted network for employees. It's the direct line to internal company resources like servers and private files. Letting guests onto this network is a massive security blind spot that you absolutely have to avoid.
Can I Use My Home Router for Business Guest Wi-Fi?
Technically, you can, but you really shouldn't. While most home routers offer a "guest network" feature, it's a world away from what a business needs. They just don't have the robust security, detailed control, or branding capabilities required for professional settings like Retail, Education, or corporate offices.
Professional Authentication Solutions that work with platforms like Cisco Meraki are built for this. They deliver critical tools like traffic shaping, custom-branded captive portals, secure access methods like IPSK, and the kind of analytics a home router can only dream of.
The crucial takeaway is this: A professional guest network isn't just about providing internet; it's about doing so securely, with full control, and in a way that reflects your brand's quality and attention to detail.
What Is a Captive Portal and Why Do I Need One?
A captive portal is that welcome page—often called a splash page—that users see right after they select your Wi-Fi network and before they get online. It’s an essential tool for any business for a few key reasons:
-
Branding: It’s your digital handshake. This is your first chance to greet visitors with your logo, brand colors, and message.
-
Legal Compliance: It’s where you require users to accept your terms of service before connecting, which can be a legal lifesaver.
-
Authentication: It serves as the gateway for all your login methods, whether it's a simple one-click connection or a more secure, credential-based login.
Simply put, a captive portal turns a generic connection into a professional, controlled, and branded experience.
Is Using One Password for All Guests a Security Risk?
Absolutely. Handing out the same password to every guest is a major security risk. Once that password is out there, it can be shared with anyone, making it impossible to track who is on your network. If you need to kick someone off, your only option is to change the password and disrupt access for every single legitimate guest. It creates a total lack of accountability.
This is where modern Authentication Solutions like IPSK and EasyPSK shine. Instead of one password for everyone, each user or device gets its own unique, manageable key. For any security-focused BYOD Corporate or Education environment, this method is the only way to go. It gives you the granular control to grant and revoke access one user at a time.
Ready to build a guest Wi-Fi experience that's as secure as it is seamless? Splash Access integrates directly with Cisco Meraki to give you powerful, easy-to-use tools for custom captive portals, advanced authentication like EasyPSK, and deep visitor analytics. Learn more and get started with Splash Access.
Article created using Outrank