SplashAccess and Cisco now fully supports the Easy PSK feature Cisco Catalyst WLAN devices that provides a simple and easy way to implement security mechanism for large-scale deployments.
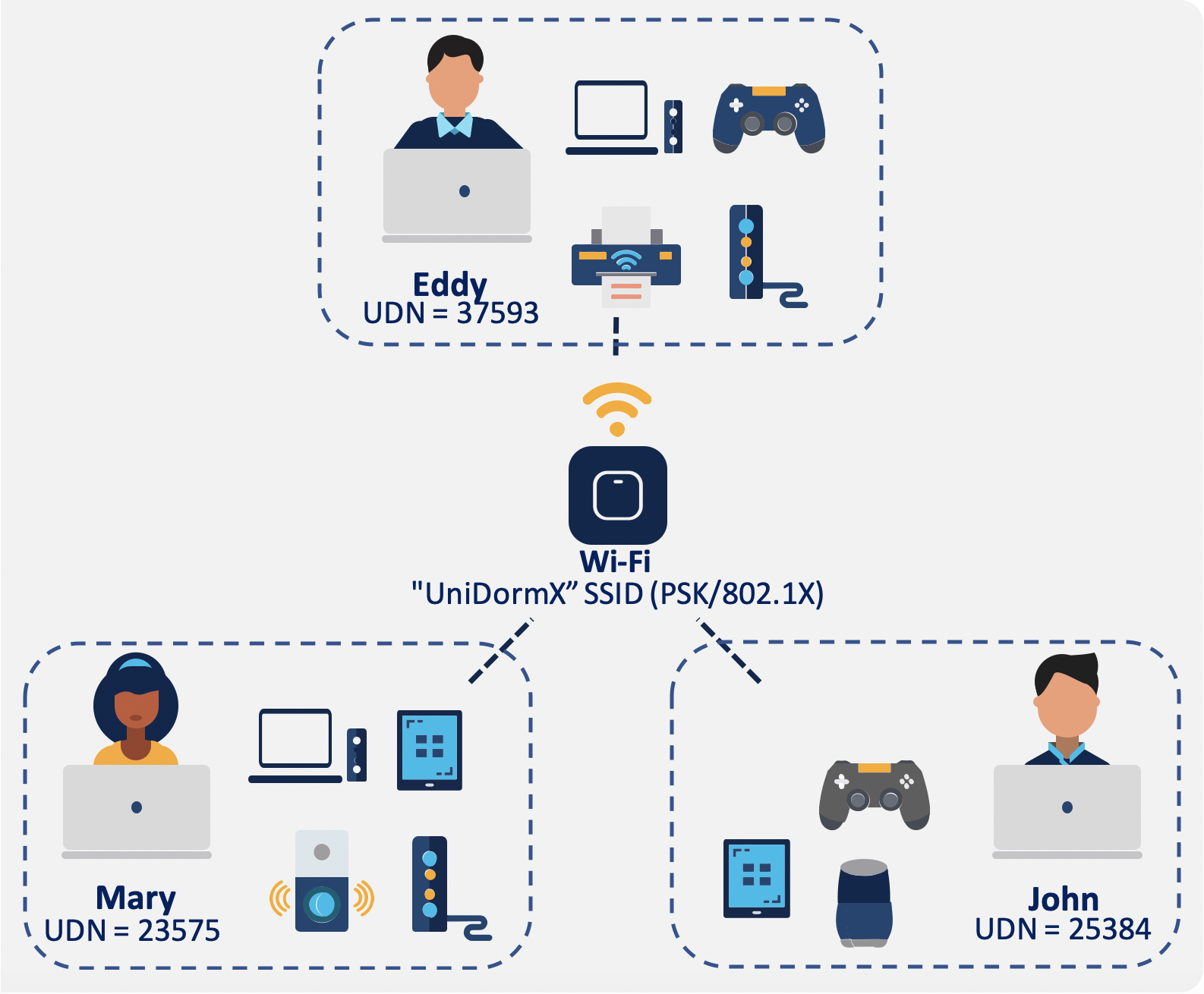
How? Cisco User Defined Network provides each end-user with their own network partition. Via the SplashAccess Portal , end-users can securely and easily register their devices so that they’re ready to go as soon as they step foot on campus.
With Identity EASYPSK , unique pre-shared keys are created for individuals or a group of users on the same SSID with the help of a RADIUS server. This kind of setup is extremely useful in networks where end-client devices do not support dot1x authentication, but a more secure and granular authentication scheme is needed. From a client perspective, this WLAN looks identical to the traditional PSK network. In the event of one of the PSKs is compromised, only the affected individual or group need to have their PSK updated. The rest of the devices connected to the WLAN are unaffected.
Also the Cisco User Defined Network portal provides end-users oversight to their network partition where they can provide and deny network access with a touch of a button.
EASYPSK identity PSK (IPSK) with User Device Names (UDN) can offer a convenient and secure alternative to traditional username and password-based wireless authentication. While WPA2-Enterprise using usernames and passwords is typically viewed as highly secure, it often creates inconvenience for users and presents compatibility issues with certain devices incapable of supporting it. Such limitations contribute to increased wireless overhead and potentially weaken overall network security. IPSK addresses these challenges by providing simplified yet robust authentication tailored for diverse device environments
Cisco Catalyst 9800 Series wireless controllers
SplashAccess EASYPSK – UDN Account
Cisco Catalyst Wi-Fi 6/6E or Aironet 802.11ac Wave 2 access points
UDN stand for User Defined Network , it allows each resident to onboard MAC Mac Addresses with a single WiFi KEY devices such as smartphones, computers, consoles, smart TV’s, Chromecast, printers, connected watches, connected speakers, etc that can then can seamlessly connect to a private bubble within the WiFi network and communicate with each other.
The surge of mobile gear and IoT endpoints—surveillance cameras, point-of-sale terminals that smooth the retail checkout, sensors and medical devices that streamline hospital operations—forces network teams in healthcare, education, government, and beyond to rethink onboarding strategies.
Identity-based segmentation lets every user or device live in its own private “bubble,” communicating only with its own assets. That sharply narrows the attack surface while preserving the freedom to connect anything that needs to be connected.
iPSK makes this level of straightforward, scalable security for IoT both practical and painless.
.
