When your guest Wi-Fi goes down, it’s more than just a technical glitch—it’s a direct hit to your user experience. Hey, we've all been there! These persistent wifi connectivity issues can derail a lesson plan in an Education setting, kill a sale in a Retail shop, or grind productivity to a halt in a corporate office that relies on a Bring-Your-Own-Device (BYOD) policy. My goal here is to help you move past the quick fixes and get to the heart of what’s really causing these Wi-Fi headaches, especially if you’re running a Cisco Meraki network.
Why Guest Wi-Fi Is So Much More Than an IT Problem
Let’s be real: unreliable Wi-Fi is maddening. For a student, a dropped connection means a lecture stops cold. For a shopper, it’s a reason to abandon their cart and maybe even leave a bad review. For an employee in a BYOD Corporate environment, it’s a direct obstacle to getting their work done.
Fixing these connection problems is all about creating a smooth, invisible experience for every user. The goal is for anyone to connect without a second thought.
The real challenge is that the root cause often isn’t just a weak signal. More often than not, the problem lies in how users are authenticated and granted access to the network, particularly through Captive Portals. This is where you need to get strategic about your network's front door and the Authentication Solutions working behind the scenes, like IPSK or EasyPSK.
The Real-World Impact of Spotty Connectivity
Think for a moment about all the places where guest Wi-Fi has gone from a nice-to-have to a core expectation:
- Education: Students and staff depend on a solid connection for everything from online research to digital collaboration. A dropped signal during a virtual lecture or an online exam is a massive disruption.
- Retail: Shoppers are constantly on their phones, comparing prices, reading reviews, or using loyalty apps. A bad Wi-Fi experience can directly impact sales and what they think of your brand.
- BYOD Corporate: In today’s offices, employees, contractors, and guests all bring their own devices. A secure and seamless onboarding process is absolutely essential for both productivity and security.
This isn't just a local issue; it's a global one. Even with all our technological advances, as of early 2025, over 2.5 billion people worldwide still don't have internet access. This highlights a huge digital divide. On the flip side, we know how powerful good connectivity can be. Improving internet access in schools by just 10% can boost a country's GDP per capita by about 1.1%. If you're interested, you can discover more insights about the global connectivity gap and its economic impact.
Moving Beyond the Basic Fixes
A truly robust solution requires looking at the entire guest access journey. That means digging into everything from your Cisco hardware and Meraki dashboard settings to the user-facing Captive Portal they first interact with. The ultimate aim is to build a system that is both iron-clad secure and incredibly simple to use.
This image shows the Cisco Meraki cloud-managed dashboard, which is your command center for diagnosing and managing network performance.
The dashboard gives you a powerful, at-a-glance view of your network's health, client traffic, and application usage. This is always the first place to start when you’re troubleshooting connectivity problems.
A well-designed guest network should never feel like a hurdle. The best systems are the ones people don’t even notice—they just work, every single time.
To get to that point, we need to explore smarter Authentication Solutions. Modern methods like Identity Pre-Shared Keys (IPSK) and simplified systems like EasyPSK offer a fantastic way to give users secure, individual access without the headaches of traditional enterprise setups. By focusing on these core components, you can turn a problematic guest network into a reliable, valuable asset for any organization.
How to Diagnose Your Connection Problems
When users complain that the Wi-Fi is down, it’s easy to jump to conclusions about a weak signal. In my experience, though, the real culprit is often hiding somewhere else entirely. Before you can fix the problem, you need to put on your detective hat. The breakdown could be happening at the user's device, deep within your network infrastructure, or right at the authentication handshake via your Captive Portal.
Let's walk through a methodical way to troubleshoot these issues on your Cisco Meraki network. We'll start with the most common suspect—the user's device—and work our way back to the core settings. This approach helps you isolate the issue quickly without getting bogged down.
Starting With the User's Device
More often than not, the problem starts and ends with the device trying to connect. Think about a busy school or a corporate BYOD environment; you're dealing with a huge variety of hardware, from a student's Chromebook to a C-level executive's new laptop, each with its own quirks.
Here’s a quick checklist to run through with the user:
- Forget and Reconnect: The first thing I always suggest is to have the user "forget" the Wi-Fi network and then try connecting again. You'd be surprised how often this clears up old, cached credentials or wonky configuration files.
- Clear the Cache: Ask the user to clear their browser cache or, even better, try connecting in a private or incognito window. A stubborn browser cache can easily prevent a Captive Portal from loading correctly.
- The Classic Reboot: It's a cliché for a reason. A full "turn it off and on again" reboot can solve a host of temporary glitches that mess with network connectivity.
If you have multiple people on different devices all reporting the same problem, it’s a pretty safe bet that the issue isn't with a single device. That's your cue to shift the investigation over to the network itself.
Diving Into the Meraki Dashboard
Your Meraki dashboard is your command center for this operation. It's packed with real-time data that can turn vague complaints into concrete leads. Instead of just guessing, you can pull up a client's connection history and see exactly what's happening behind the scenes.
Let's say a customer in your Retail store says they can't get past the splash page. A quick look at the event log for their device might show they authenticated successfully but then failed to get an IP address. Suddenly, you know you’re dealing with a DHCP scope issue, not a broken Captive Portal.
The most effective troubleshooting starts with gathering evidence. The Meraki dashboard's event logs are your primary source, turning vague complaints like "the Wi-Fi is broken" into actionable data points.
Look for patterns in those logs. Are all the failed connections happening on a single access point? Are they all getting stuck at the authentication stage? These clues are gold. They help you zero in on the root cause. It's also a good time to investigate potential signal overlap or channel conflicts, which can create all sorts of frustrating interference with Wi-Fi.
Analyzing Authentication Failures
This is often the final and most complex piece of the puzzle. Authentication is where your Captive Portals and backend Authentication Solutions do their work. A single misconfiguration here can trap users in an endless loop—they see the login page, but they can never actually get online.
This is particularly common in setups using advanced security like IPSK or integrations from services such as EasyPSK. For instance, if your walled garden rules in Meraki are too restrictive, you might be accidentally blocking the user's device from reaching the very authentication server it needs to talk to.
Think of it like a security checkpoint where the guard's radio is dead. They can't get verification, so the line just stops moving. In these situations, your authentication platform’s own logs become invaluable. They can show you failed login attempts, the reason for the failure (like an expired key), and whether the connection request from the Meraki AP ever even made it to the server. By cross-referencing the Meraki logs with your authentication provider's logs, you can find and fix that communication breakdown fast.
Choosing the Right Authentication for Guest Access
When it comes to guest Wi-Fi, the login process is often where a smooth experience grinds to a halt. In my experience, this is the single biggest source of Wi-Fi connectivity issues, turning what should be a simple connection into a major headache for users. The real challenge is striking that perfect balance between robust security and an effortless user journey.
Let's dig into some modern Authentication Solutions that can eliminate these common frustrations. Frankly, traditional methods—like a single shared password scribbled on a whiteboard or a clunky splash page—just don't cut it anymore, especially in demanding environments like Education campuses or corporate BYOD offices.
Beyond the Shared Password
A single password for everyone might seem easy, but it's a security nightmare and an operational mess. Think about it: when one person leaves, you have to change the password for everyone, creating chaos. This approach also gives you zero visibility into who is on your network, making it impossible to manage access or troubleshoot problems effectively for your Cisco or Meraki infrastructure.
Simple splash pages, or Captive Portals, aren't much better if they're not done right. They can be buggy, fail to load properly on certain devices, and often create a frustrating barrier between your guest and the internet. In a busy Retail environment, a customer struggling with a login page is a customer who might just give up and walk away.
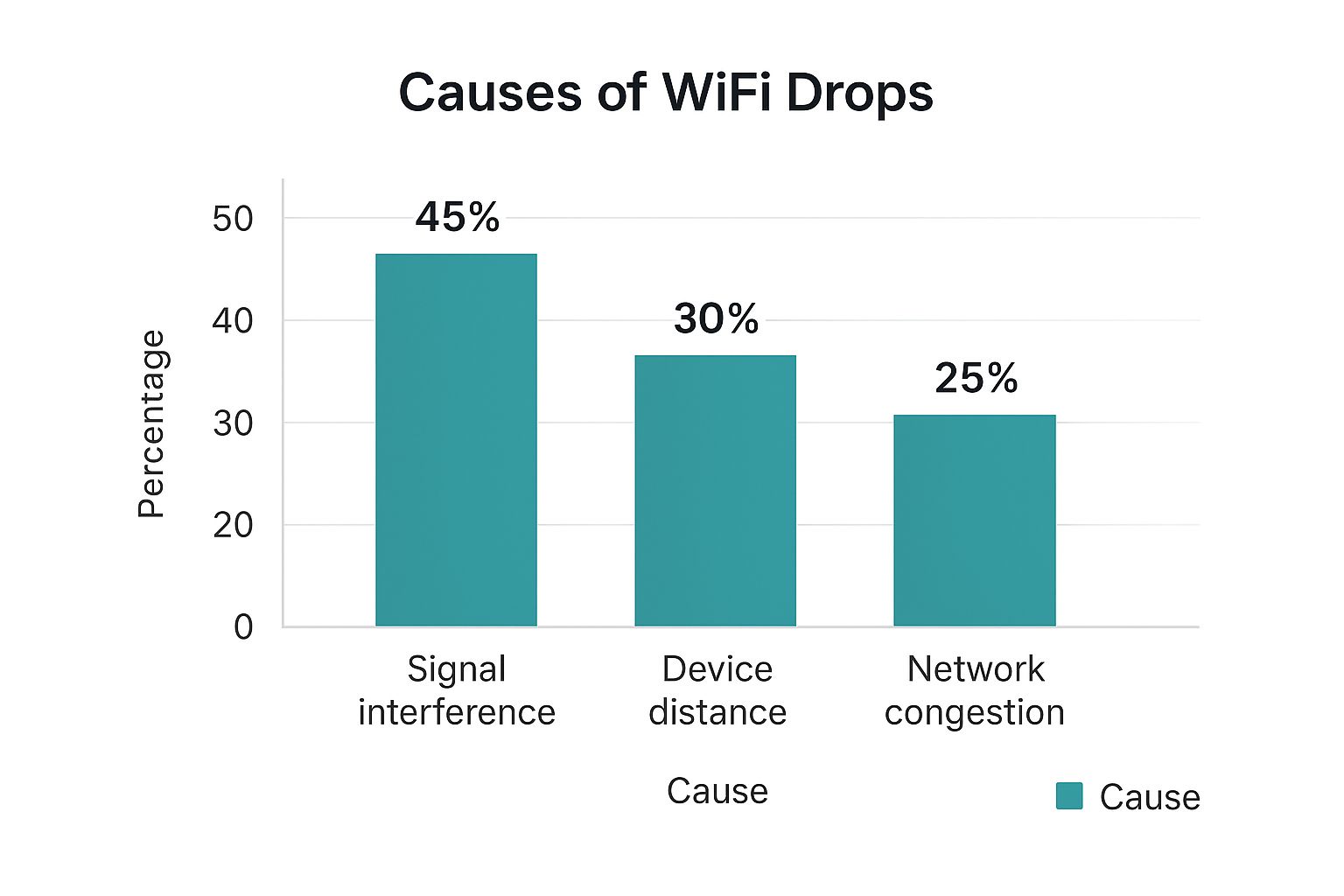
This chart really drives home how many different things can go wrong with a Wi-Fi connection, many of which get worse with a bad authentication process.
As you can see, while physical factors like signal interference are significant, a complicated or failing login system feels just as disruptive to the person trying to get online.
A Smarter Approach with IPSK
This is where smarter authentication methods like Identity Pre-Shared Keys (IPSK) come into play. Instead of one password for everyone, IPSK gives each user or device its own unique, personal key to access the network. It’s like giving everyone their own key to the building instead of leaving the front door unlocked.
This technology is a real game-changer in a few key sectors:
- Education: A school can issue each student a unique Wi-Fi key that lasts for the entire semester. If a student's device is compromised or they leave the school, their individual access can be revoked instantly without affecting anyone else.
- BYOD Corporate: Onboarding new employees and their personal devices becomes incredibly simple. Each person gets their own key, ensuring secure access to company resources while keeping personal traffic separate and secure.
- Retail: Loyalty program members could receive a personal key that grants them premium, high-speed access, creating a fantastic perk and encouraging sign-ups.
Solutions like EasyPSK make this advanced security accessible without the complexity of traditional enterprise-level systems. You get the benefit of individual, secure connections managed through a simple interface.
The Power of Captive Portals Done Right
While IPSK offers incredible security for regular users, Captive Portals still have a crucial role, especially for short-term guests. A well-designed captive portal is the digital welcome mat for your network. It shouldn't be a roadblock but an opportunity.
The best authentication system is one that users don't even have to think about. It should feel invisible, secure, and instant, whether it’s for a student on campus or a shopper in a store.
Instead of a clunky form, a modern captive portal can offer simple login options like a one-click social media connection or a quick QR code scan. This streamlines the process, drastically reducing the chances of connection failure. For those looking to get this right from the start, our guide on how to set up guest Wi-Fi offers practical steps for creating that seamless experience.
Comparing Guest Wi-Fi Authentication Methods
Choosing the right method depends entirely on your environment and what you want to achieve. What works for a coffee shop is completely different from the needs of a university campus. Here's a quick breakdown to help you compare the most common options.
| Authentication Method | Best For | Security Level | User Experience |
|---|---|---|---|
| Open Network | Quick, temporary public access (e.g., small events) | Low | Easiest (no login) |
| Shared Password | Small offices, private gatherings | Low | Simple, but insecure and hard to manage |
| Captive Portal | Retail, Hospitality, Airports | Medium | Good, if designed well (can offer social login, ads) |
| IPSK/EasyPSK | Education, Corporate BYOD, Long-term guests | High | Excellent (connect once and you're set) |
| 802.1X/RADIUS | Large enterprises, Government | Very High | Secure but complex for guests and administrators |
Ultimately, picking the right tool for the job is what matters.
By combining the right tools—whether it's the personalized security of IPSK for your long-term users or a beautifully simple captive portal for transient guests—you can eliminate the authentication bottleneck for good. This directly resolves many of the most common Wi-Fi connectivity issues and transforms your guest network from a source of frustration into a reliable, high-performing asset.
Fine-Tuning Your Meraki Captive Portal
Think of your Captive Portal as the digital front door to your guest Wi-Fi. When it works well, it's a seamless welcome that gets people online in seconds. But when it's poorly configured, it becomes a major roadblock, leading to a frustrating flood of wifi connectivity issues that leave your guests stuck.
I've seen this exact problem pop up in countless deployments, from sprawling Education campuses to busy Retail stores. The good news is that most of these headaches can be solved with a few strategic tweaks in your Cisco Meraki dashboard. It's all about smoothing out the login journey and making it as intuitive as possible for the end-user.
Walled Garden Woes
One of the most common culprits I run into is a misconfigured "walled garden." In theory, this feature is great—it lets users access specific websites before they authenticate, like your company’s homepage or a payment processor. But if it’s not set up correctly, it can accidentally block the very servers needed for the login process to even work.
Imagine a guest tries to log in with their social media account, but your walled garden is blocking the domains for that social platform. They click the login button, and… nothing. It's an incredibly common reason for failed connections, especially if you’re using third-party Authentication Solutions.
To get ahead of this, you have to make sure your walled garden rules explicitly allow access to all the domains required for your chosen login methods. This usually includes:
- Social Login Providers: Whitelist the domains for Facebook, Google, or any other social login you offer.
- Payment Gateways: If you charge for Wi-Fi access, the gateway's domains are a must.
- External Authentication Servers: This is critical if you're using IPSK or other cloud-based authentication platforms.
The User Experience Can't Be an Afterthought
A clean, mobile-friendly design isn't just for looks; it’s fundamental to usability. A cluttered or confusing portal will just make people give up. In a Retail environment, a shopper won’t spend five minutes wrestling with a complex login form. In a corporate BYOD setting, a confusing page is a guaranteed way to generate more helpdesk tickets.
Your portal needs to be simple, with clear instructions. Use large, tappable buttons, keep text to a minimum, and offer straightforward login options like a one-click social login or a form asking only for an email. This simple approach drastically cuts down on user errors and frustration.
The best captive portal is one the user barely notices. The goal is to get them online so quickly and easily that they forget the login process ever happened. That’s the key to a great first impression on your network.
Making the portal responsive is non-negotiable today. The overwhelming majority of your guests are connecting from a smartphone, and a page that forces them to pinch and zoom is an immediate failure. Always test your portal on different screen sizes to ensure it works flawlessly for everyone. For some great examples of modern, user-friendly designs, you can explore the options for a Wi-Fi captive portal.
More Than Just an On-Ramp to the Internet
A well-designed portal on your Cisco network can do more than just grant internet access. It’s a prime opportunity for branding and engagement. You can display welcome messages, promote in-store offers, or share important campus announcements.
It's also important to remember that sometimes, connectivity problems are bigger than your own network. Internet outages are on the rise globally, with a startling 32% increase in events recorded in just the first quarter of 2025. These disruptions often stem from complex issues within core service provider systems. As network infrastructure becomes more intricate, even minor configuration changes can have a ripple effect, impacting the reliability of the Wi-Fi experience for end-users.
By pairing a streamlined, user-friendly portal with robust Authentication Solutions like IPSK or EasyPSK, you create a guest network that is both secure and incredibly easy to use. This powerful combination doesn't just solve common wifi connectivity issues—it turns your network into a valuable asset for your entire organization.
Proactive Strategies to Prevent Future Wi-Fi Issues
Fixing Wi-Fi problems as they pop up is one thing, but getting ahead of them is the real game-changer. When you shift from a reactive to a proactive mindset, you can transform a guest network from a constant source of support tickets into a reliable, invisible asset. It all comes down to using the tools you already have to spot trouble before your users do.
For those of us managing Cisco Meraki networks, the dashboard is our crystal ball. Setting up intelligent monitoring and alerts is the best first line of defense against recurring wifi connectivity issues. Think about it: getting an alert that an access point has gone offline or that DHCP lease failures are spiking lets you jump on the problem long before a student in a lecture hall or a customer in your Retail store even notices something's wrong.
This kind of proactive approach is absolutely essential for keeping a network healthy in dynamic environments like Education campuses, retail spaces, and corporate offices with heavy BYOD traffic.
Regular Network Health Checks
Don't wait for the complaint emails to start pouring in. Make it a routine to dive into the user connection data in your Meraki dashboard. You need to look for trends. Are connection failures always happening in one specific area? Are certain device types struggling more than others? This data-driven habit helps you spot emerging patterns before they become full-blown crises.
A proactive network administrator doesn't just solve today's problems; they use today's data to prevent tomorrow's outages. Consistent monitoring turns troubleshooting from a frantic scramble into a predictable routine.
For example, I've seen cases where an Education facility noticed a spike in latency in the same lecture hall every Tuesday at 10 AM. A quick investigation revealed a capacity issue, which they could then address before it started disrupting lectures. That’s the difference between intelligently planning for growth and just reacting to failures.
Strengthening Your Security Posture
Proactive management isn't just about performance; security is a huge piece of the puzzle. Your authentication methods are critical here. Using modern Authentication Solutions like IPSK or EasyPSK gives you incredibly granular control over who can access your network and how. It’s a massive step up from a single, shared password that can be easily compromised.
A simple but powerful security practice is to regularly audit your access policies. Make it a habit to revoke credentials for users who no longer need them. Just as important is staying informed about new threats. For a deeper dive, check out our guide on protecting your network from the latest WPA1/WPA2 PSK vulnerability.
Planning for the Unpredictable
Sometimes, the root cause of wifi connectivity issues is completely out of your hands. We've seen major infrastructure disruptions and even government-directed internet shutdowns take networks down.
For instance, during the second quarter of 2025, countries like Libya and Iran experienced multiple state-mandated internet shutdowns tied to political events. These actions caused traffic to plummet by over 50% in some regions, with certain providers facing complete blackouts for hours.
It's not just political, either. Large power outages in Spain and Portugal and fiber optic cable cuts in Haiti and Malawi are stark reminders of how fragile internet infrastructure can be. These events lead to widespread Wi-Fi disruptions for everyone. You can read the full research about these internet disruptions to get a better sense of how global events can impact local connectivity.
While you can’t stop these large-scale events, you can prepare for them. Having a clear support and communication plan for your users is crucial. Let them know what's happening and provide alternative solutions if possible. That kind of transparency builds trust and manages expectations, turning a potentially chaotic situation into a manageable one. By combining vigilant monitoring, robust security, and a solid support plan, you can build a resilient guest Wi-Fi network that stands the test of time.
Frequently Asked Questions
Guest Wi-Fi can be a real headache, especially when you're wrestling with persistent Wi-Fi connectivity issues. Having worked with countless network administrators in Education, Retail, and corporate BYOD environments running Cisco and Meraki gear, I've heard it all. Here are some of the most common questions that come up and my straight-to-the-point answers.
Why Do Some Devices Struggle to Connect to Our Captive Portal?
This is the classic "it's connected but not working" problem. More often than not, it's a conflict between the device's operating system or browser and how the Captive Portal tries to redirect the user. Older devices, or sometimes just devices with really aggressive security settings, just don't want to play ball and fail to automatically pop up the login page.
The result? The user is stuck. They see the Wi-Fi bars, but they can't get online.
A smart Captive Portal design anticipates this. I always recommend including simple, clear instructions on the landing page telling users to open a browser and try navigating to a non-HTTPS site if the login screen doesn't appear. Also, double-check your walled garden rules in the Meraki dashboard. If you've accidentally blocked the domains needed for authentication, it's game over before it even starts.
A key takeaway here is that a great user experience comes from planning for these small but incredibly common device quirks. A single line of text on your portal can be the difference between a happy user and another support ticket.
Can We Use IPSK for Both Students and Staff?
Absolutely, and you should. This is hands-down one of the most powerful applications for Identity Pre-Shared Keys (IPSK) in any Education setting. You can easily create distinct groups for students, faculty, and administrative staff, and then assign a unique set of network policies to each.
For instance, a student’s IPSK could give them access to a filtered list of educational resources and block streaming sites during school hours. At the same time, a teacher’s key could grant them wide-open, unrestricted access. All of this granular control is managed through your Authentication Solutions provider, making it simple to revoke access for one specific user without having to change the password for the entire network.
What Is EasyPSK and How Is It Different?
Think of EasyPSK as the user-friendly version of IPSK. While traditional enterprise authentication methods can get pretty complex, EasyPSK is built to give the security of individual Wi-Fi keys to organizations that don't have a huge IT department to manage it all.
You get the same core benefit—a unique key for every user or device—but with a management interface that's far more intuitive. This makes it perfect for a Retail chain that wants to give premium Wi-Fi access to loyalty members, or a corporate office looking for a secure way to onboard employee devices in a BYOD environment. It cuts through the technical jargon and delivers a massive upgrade in security and user management.
Sometimes, what looks like a connectivity problem is really an authentication failure. If you're seeing repeated login issues, you might want to learn more about how to handle an error in authentication to get to the bottom of it.
How Does a Captive Portal Improve Network Security?
A Captive Portal is much more than just a login screen; it’s a crucial security and accountability checkpoint. When you require users to agree to your terms of service or sign in with a form, you create an access record. Suddenly, network activity is no longer anonymous, which is vital for compliance and for tracking down any misuse.
It also acts as a gatekeeper, stopping unauthorized devices from getting a free pass to your internal network resources. When you pair this with a powerful backend like Meraki, you gain incredible visibility into who is connecting, when they're connecting, and from where. Your guest Wi-Fi goes from being an unknown risk to a fully managed service.
Ready to eliminate your Wi-Fi connectivity issues for good? Splash Access provides a powerful platform for Cisco Meraki that delivers secure, seamless, and intelligent guest Wi-Fi. https://www.splashaccess.com