Hey there! Ever tried to connect to a new Wi-Fi network and seen "WPA2-PSK" in the security settings? It might look like a bit of technical jargon, but it's actually something you use every single day. Think of it as the friendly but firm bouncer for your wireless network.
WPA2-PSK stands for Wi-Fi Protected Access 2 – Pre-Shared Key. That "key" is just the Wi-Fi password that everyone uses to get online. It's the standard for most home and small business networks for a good reason—it’s simple and it just works.
To make things crystal clear, let's break down exactly what each part of that term means.
WPA2 PSK Quick Answer
| Component | What It Means |
|---|---|
| WPA2 | The security protocol, or the set of rules, that protects your wireless network. It’s been the industry standard for over a decade. |
| PSK | Stands for "Pre-Shared Key." This is the single, shared password you give to friends, family, or customers to let them on your network. |
Essentially, when you connect a device using WPA2-PSK, you're using one password to prove you're allowed access. It's as simple as that!
How Your Wi-Fi Password Keeps You Safe
At its heart, WPA2-PSK is all about encryption. Once your device uses the Pre-Shared Key to join the network, that key scrambles all the information flying between your laptop and the router. This makes your online activity completely unreadable to anyone trying to eavesdrop.
It’s a straightforward and effective way to lock down a network without needing a degree in IT. This simplicity is why it became the go-to security method for millions of networks worldwide.
Where You'll Typically Find WPA2-PSK
Because it's so easy to manage, WPA2-PSK is the security backbone in all sorts of places. You've probably connected to one in:
- A local coffee shop or Retail store offering guest Wi-Fi.
- Education settings like schools or libraries where managing individual accounts might seem like overkill at first.
- Any Corporate environment managing simple guest access or a basic BYOD (Bring Your Own Device) policy.
For businesses running on powerful hardware like Cisco Meraki, WPA2-PSK often serves as the first layer of security. It’s a solid foundation, but it’s just the beginning. From here, you can add more advanced Authentication Solutions like Captive Portals for guest registration or even IPSK (like EasyPSK), which gives each user their own unique key.
While WPA2-PSK is great for many situations, it's important to understand the difference between WPA2 Personal vs Enterprise as your security needs become more complex. The single shared password model has its limits, which is where more robust, individual-based authentication methods come into play.
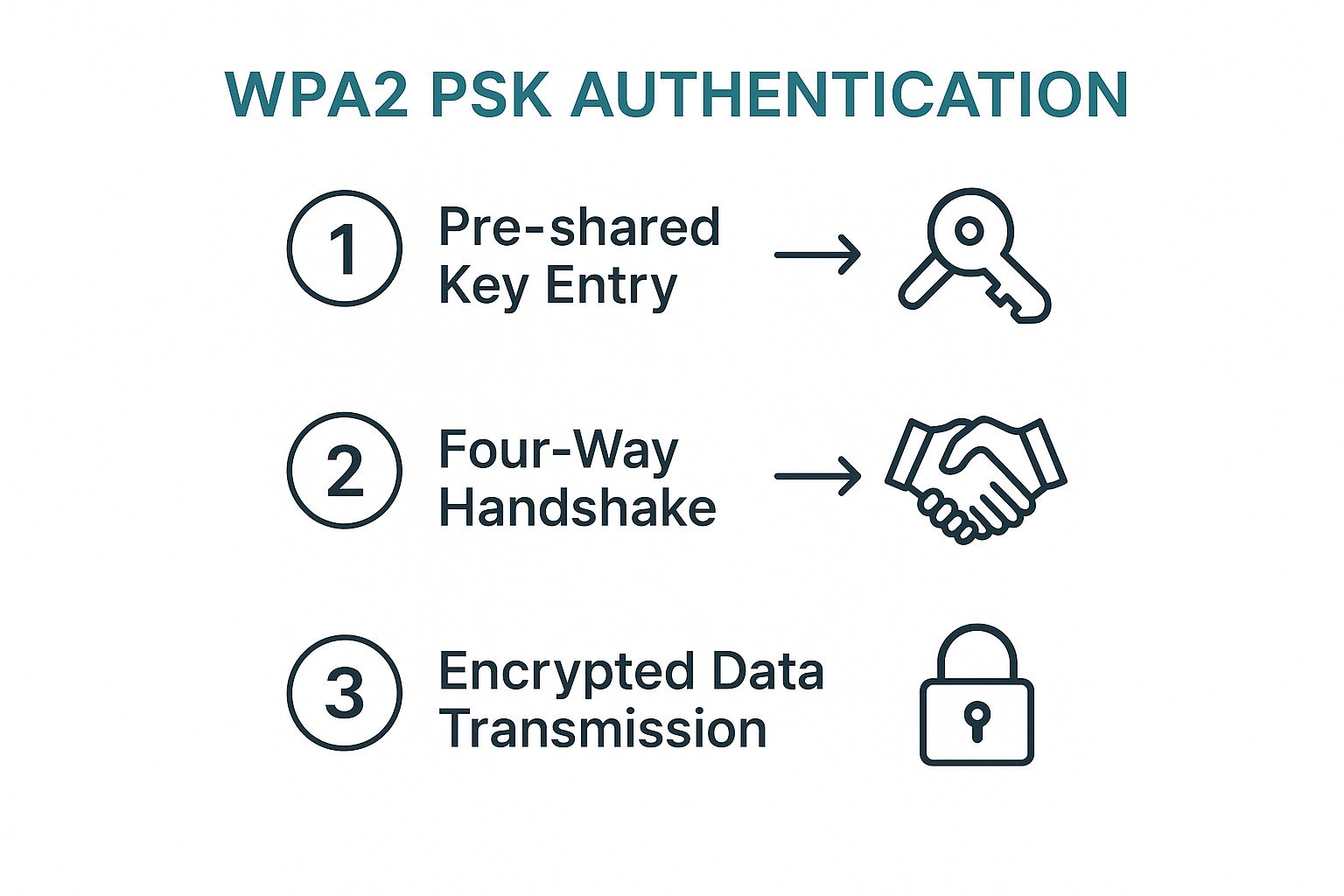
How WPA2-PSK Actually Secures Your Wi-Fi
So, how does that simple password keep your data safe? The genius of WPA2-PSK is that it never actually sends your password over the air where someone could intercept it. Instead, it uses a much smarter, more private method to verify your connection.
It all comes down to a process called the four-way handshake. Think of it as your laptop and the router having a quick, private chat to confirm they both know the secret passphrase (the Pre-Shared Key) without ever saying it out loud. Once they've confirmed they're on the same page, the real security kicks in.
This handshake is the critical first step. After it's complete, every piece of data you send or receive gets scrambled.
The Lock and Key: AES Encryption
Once the handshake is complete, WPA2-PSK starts using the Advanced Encryption Standard (AES) to protect your traffic. This isn't just some basic code; it’s the same powerful encryption algorithm trusted by governments and banks to secure highly sensitive information.
AES effectively wraps all your data—from emails to website visits—in a complex digital cipher, turning it into unreadable gibberish for anyone snooping on the network.
This one-two punch of a secure handshake and rock-solid encryption is why WPA2 has been the gold standard for so long. Certified way back in 2004, it was a massive leap forward, built on the mandatory security requirements of the IEEE 802.11i standard.
This secure connection is critical in any environment, from a Retail store's point-of-sale system to an Education network for students, or a Corporate BYOD setup. It ensures that confidential data remains private while being transmitted over the air.
For organizations running on powerful Cisco Meraki hardware, WPA2-PSK is just the starting point. It provides the foundational security layer, but you can build on it with more advanced authentication methods. For instance, instead of one password for everyone, you can use unique security keys for Wi-Fi, a technique that gives each person or device its own private key. This is a game-changer for managing access and security in busy environments.
The Hidden Risks of a Single Shared Password
The main draw of a single password is its simplicity. It's fast and easy to get everyone connected. But as an organization grows, that same simplicity quickly becomes its greatest weakness.
This "one key fits all" model just doesn't scale, especially in busy, dynamic environments.
Think about a corporate BYOD policy or a bustling Education campus. That initial convenience can quickly morph into a major security headache. What happens when an employee leaves the company or a student misplaces their laptop?
The only real way to lock down the network is to change the password for everyone. This means manually updating every single device, from office desktops to student tablets. It’s a recipe for logistical chaos and frustrating downtime.
The Problem with Shared Accountability
This lack of individual accountability is a huge flaw. When every user has the same key, it’s practically impossible to track who did what. One leaked or compromised password puts the entire network in jeopardy. Understanding the wider landscape of common network security vulnerabilities really brings home why even a seemingly small weakness like this is so critical.
This operational nightmare is exactly why most businesses treat WPA2-PSK as just a starting point. The risks tied to a single shared key are just too high for many organizations to accept.
The core issue with a standard Pre-Shared Key is that security is collective. A breach from one user becomes a breach for all users, forcing disruptive, network-wide password changes.
This is where more advanced Authentication Solutions, especially on platforms like Cisco Meraki, become so important. Modern networks need smarter ways to handle access, moving past the single-password model and toward systems that issue individual credentials, like IPSK or EasyPSK. You can learn more about protecting your network from the latest WPA2-PSK vulnerabilities and see why these upgrades matter so much.
When Standard Wi-Fi Security Is Not Enough
For years, WPA2-PSK was the go-to standard for securing our wireless networks. We all trusted it. But in the world of cybersecurity, what's a fortress one day can develop a few cracks the next. The hard truth is that what was once the gold standard is now more of a baseline—good, but not good enough for every situation.
This became painfully obvious when researchers found clever ways to sidestep its defenses. They weren't just guessing passwords; they were finding subtle weaknesses in how the protocol itself worked.
Uncovering the Cracks in the Armor
One of the biggest wake-up calls was the KRACK (Key Reinstallation Attack) vulnerability. This wasn't a small thing. It exploited a flaw in the "four-way handshake"—the very process that's supposed to establish a secure connection. This meant an attacker could potentially intercept and read Wi-Fi traffic, even if you had a strong password.
The KRACK discovery in 2017 was a major jolt to the industry. It proved that strong encryption alone isn't enough if the handshake process can be compromised, and it directly accelerated the push for the next generation of security protocols. You can learn more about how these vulnerabilities led to the development of WPA3.
For many organizations, a vulnerability like this is a non-starter.
Think about a Retail store processing credit card transactions or an Education campus safeguarding student data. In these environments, even a tiny security gap can lead to huge problems. The risk is just too high to depend on a protocol with well-known exploits.
This is exactly where modern Authentication Solutions, especially on platforms like Cisco Meraki, come into play. They don't just rely on the Wi-Fi protocol; they add crucial security layers on top of it.
By moving beyond a single shared password and using tools like IPSK or EasyPSK, businesses can build a much tougher defense. It’s a shift from a reactive security stance to one that actively anticipates and guards against modern threats.
Taking Security to the Next Level with Identity-Based PSK
It becomes pretty clear, pretty quickly that a single, shared password just doesn't scale for growing organizations. This is where modern authentication comes in, especially when you're working within a platform like Cisco Meraki. The idea is to keep the simplicity of connecting with a password but get rid of the huge security headache that comes with sharing it.
This is where Identity Pre-Shared Key (IPSK) comes into play. The concept is actually quite straightforward. Instead of giving everyone the same master key to the office building, you give each person their own unique keycard.
This approach gives you the best of both worlds. It still uses the WPA2-PSK protocol that all our devices are built to understand, but with one critical difference: every single user or device gets its own unique password.
Gaining Granular Control Over Your Network
This move to individual keys is a game-changer for any IT admin. If an employee leaves the company or a student loses their laptop, you can revoke their specific access in an instant. No more forcing everyone else to change the Wi-Fi password. That kind of granular control is absolutely essential for managing the networks we rely on today.
With IPSK, you're shifting from a collective, all-or-nothing security model to one based on individual identity. It lets you grant, deny, or change access for one person without causing a network-wide disruption.
This capability is especially powerful in a few specific environments:
- Corporate BYOD: You can easily manage employee-owned devices, making sure only authorized people can get onto the network without complex certificate setups.
- Education: It's perfect for handling the constant churn of students, faculty, and all their devices across campus.
- Retail: You can provide secure, segmented access for staff, point-of-sale systems, and inventory scanners, keeping them totally separate from the public guest Wi-Fi.
Solutions like EasyPSK make deploying these unique keys even simpler. As you think about improving your network security, remember that a solid policy is your foundation; checking out some information security policy templates can help you formalize your rules. To see how this tech fits into a professional setup, you can also learn more about setting up IPSK with RADIUS authentication.
Enhancing Guest Wi-Fi with Captive Portals
While a simple password works well for basic access, combining WPA2 PSK with a Captive Portal is a far more powerful strategy for guest networks. This one-two punch is the standard for businesses in Retail, hospitality, and Education that want to offer branded, secure Wi-Fi access. It’s a simple but incredibly effective way to welcome visitors online.
Think of it as a two-step verification for your network. The WPA2 PSK password is the first layer, encrypting every connection from the moment a device joins. This keeps both your guests and your business safe from anyone trying to eavesdrop. This initial password can be anything—often something simple and easily displayed for customers.
Creating a Branded Welcome Gate
Once a guest connects using the password, the Captive Portal kicks in. Instead of getting immediate internet access, they are redirected to a custom login page. This is where the magic happens, turning a basic Wi-Fi connection into a powerful engagement tool.
This "welcome gate" does a few important jobs all at once:
- Reinforces Brand Identity: Greet users with your logo, colors, and messaging.
- Shares Promotions: Display current sales, special offers, or upcoming event details.
- Communicates Terms of Service: Ensure everyone agrees to your network usage rules before they hop online.
Modern Authentication Solutions on platforms like Cisco Meraki make managing this entire experience straightforward. Integrating a Captive Portal turns a technical security step into a polished and valuable touchpoint with your customers. You not only secure your network but also open up a new channel for communication.
If you're interested in setting this up, this guide to Wi-Fi captive portals offers a great deep dive. This approach is perfect for any organization, from a Corporate BYOD guest network to a public library, that needs to provide controlled and professional internet access.
WPA2-PSK Questions We Hear All the Time
Let's tackle some of the most common questions people have about WPA2-PSK and where it stands in the world of Wi-Fi security today.
Is WPA2-PSK Still Good Enough for My Home?
For most home networks, the short answer is yes, WPA2-PSK with AES encryption is still reasonably secure. But there's a big "if" attached to that: your password has to be incredibly strong and unique. The biggest threat to a home network isn't some complex cyberattack; it's a password like "password123" or "Fluffy2024" that can be cracked in seconds.
If your router offers WPA3, you should absolutely use it. It’s the newer, better standard. That said, a WPA2-PSK network with a rock-solid password still offers a decent layer of defense for your day-to-day browsing.
WPA2-PSK vs. WPA2-Enterprise: What's the Real Difference?
The fundamental difference comes down to authentication—how the network verifies who you are. An easy way to think about it is building access:
- WPA2-PSK (Personal): This is like giving everyone the same physical key to the front door. It’s simple, but if one person loses their key (or the password leaks), you have to change the lock for everyone.
- WPA2-Enterprise: This is like giving each person a unique keycard. Access is tied to an individual's credentials (like a username and password). This is the gold standard for businesses, Education, and Retail because you can track who is on the network and revoke a single person's access instantly.
Enterprise mode is far more secure and manageable because you can kick someone off the network without affecting anyone else.
How Does IPSK Make PSK Better?
This is where things get really interesting. IPSK (Identity Pre-Shared Key), and similar Authentication Solutions like EasyPSK, are a fantastic hybrid. They give you the individual control of Enterprise mode but with the simplicity of a pre-shared key system.
Instead of one password for the whole network, an admin using a platform like Cisco Meraki can generate a unique key for every single user or device.
Think about it: if an employee in a Corporate BYOD environment leaves, or someone in an Education setting loses their laptop, you just disable their specific key. The rest of the network keeps running without a hitch. This kind of targeted control is a massive security upgrade without the heavy lifting of a full-blown Enterprise configuration.
At Splash Access, our whole game is about enhancing the incredible security features built into Cisco Meraki. We layer our smart Captive Portals and Authentication Solutions over WPA2-PSK and IPSK to build Wi-Fi experiences that are not only secure but also seamless and perfectly on-brand.
Ready to see what your network is truly capable of? Learn how Splash Access can help you.