Ever find yourself wondering who, or what, is really on your network? Let's peel back the layers of Cisco ISE (Identity Services Engine) and have a friendly chat about what it actually does, without all the dense tech jargon.
Think of ISE as the ultimate bouncer for your company's digital front door. Before any person or device gets past the velvet rope, ISE steps in to check their ID and decide what they're allowed to access once inside.
Your Network's Smart Security Brain
At its heart, Cisco ISE is the central command center that grants or denies network access. It's an all-in-one authentication solution that ensures only trusted users and secure devices can connect. It brings everything under one roof, making it so much easier to handle modern network headaches like guest Wi-Fi and the explosion of personal devices (BYOD).
Picture a busy Corporate office, a sprawling Education campus, or a bustling Retail store. You've got employees, students, guests, and a wild mix of smartphones, laptops, and tablets all trying to get online. How do you keep that chaos secure? That's exactly where ISE shines, especially when it's working hand-in-hand with Cisco and Meraki hardware. It gives you the clear visibility and tight control you need to manage it all.
Securing Every Connection Point
From the locked-down employee Wi-Fi to the open guest network in your lobby, ISE is the one setting the rules. It’s the engine that powers things like Captive Portals where visitors sign in, and it simplifies access for lots of devices using smart authentication solutions like IPSK (Identity Pre-Shared Key) and EasyPSK.
This means a shopper in a Retail store gets a different, more limited level of access than a student in a university dorm, or an employee connecting their personal phone in a BYOD environment. By rigorously vetting every single connection, ISE becomes a cornerstone of any strong security plan. This philosophy of "never trust, always verify" is central to a modern security model. You can dive deeper into this concept by learning more about what Zero Trust security is and how it works.
To make it even clearer, here’s a quick breakdown of what ISE is doing behind the scenes.
Cisco ISE Core Functions at a Glance
This table sums up the main jobs ISE handles to keep your network safe and sound.
| Function | What It Does in Simple Terms |
|---|---|
| Authentication | Asks, "Who are you?" It verifies user and device identities. |
| Authorization | Asks, "What are you allowed to do?" It assigns access levels based on policy. |
| Accounting | Asks, "What did you do?" It logs activity for security and compliance audits. |
| Profiling | Figures out what a device is (e.g., iPhone, printer, Windows laptop). |
| Posture Assessment | Checks if a device is secure (e.g., has antivirus, is updated). |
Basically, ISE doesn't just open the door; it checks your ID, gives you the right key, and keeps an eye on things to make sure everyone stays in their designated areas.
Why Modern Networks Need a Smarter Gatekeeper
Not too long ago, network security was a lot simpler. You essentially built a digital fortress around your office, and that was that. But the modern network is a completely different beast—it has no clear borders and is constantly buzzing with a massive variety of devices.
Just think about a typical Retail store. You've got the point-of-sale systems, employee tablets for inventory, and dozens of customer smartphones all hopping onto the same Wi-Fi. In an Education setting, that number explodes to thousands of students and faculty, each with their own laptops and phones. And in the Corporate world, BYOD (Bring Your Own Device) policies are now the norm, which means personal devices are regularly accessing sensitive company data.
A one-size-fits-all security policy simply can't handle this kind of complexity. How do you manage this flood of different devices without bringing everything to a screeching halt? You need a more intelligent gatekeeper.
The Growing Security Gap
The hard truth is that most organizations are falling behind. The 2025 Cisco Cybersecurity Readiness Index revealed a sobering statistic: only 4% of organizations globally have the 'Mature' level of cybersecurity readiness required to fend off modern threats. While that’s a small step up from the year before, it points to a huge security gap worldwide. You can dig into these findings over on cybermagazine.com.
This is exactly why a solution like Cisco ISE has become so important. It shifts the focus from reactive defense to proactive control. Instead of just building a wall, it gives you the deep visibility and granular rules needed to manage exactly who and what is on your network at all times.
Cisco ISE provides the foundation for a proactive security posture, allowing IT teams to define precise access policies that automatically adapt to the user, device, and location. This is the key to securing today’s complex Cisco and Meraki environments.
By putting a system like this in place, you unlock the ability to create sophisticated authentication solutions. For instance, you can set up a secure Captive Portal for guests or use simple yet effective tools like IPSK or EasyPSK for device-specific access. Taking these steps is fundamental to building a stronger, more resilient network. To learn more, check out our guide on the best practices for network security.
How Cisco ISE Secures Your Network
So, what’s actually happening when Cisco ISE is protecting your network? Let's break it down. The easiest way to think about it is to picture your network as an exclusive club, and ISE is the sharp, no-nonsense security team at the door.
The whole process boils down to three powerful steps. It all kicks off the second any device tries to get on your network—whether that's a company laptop in a BYOD setup, a student's smartphone on an Education campus, or a payment terminal in a Retail shop.
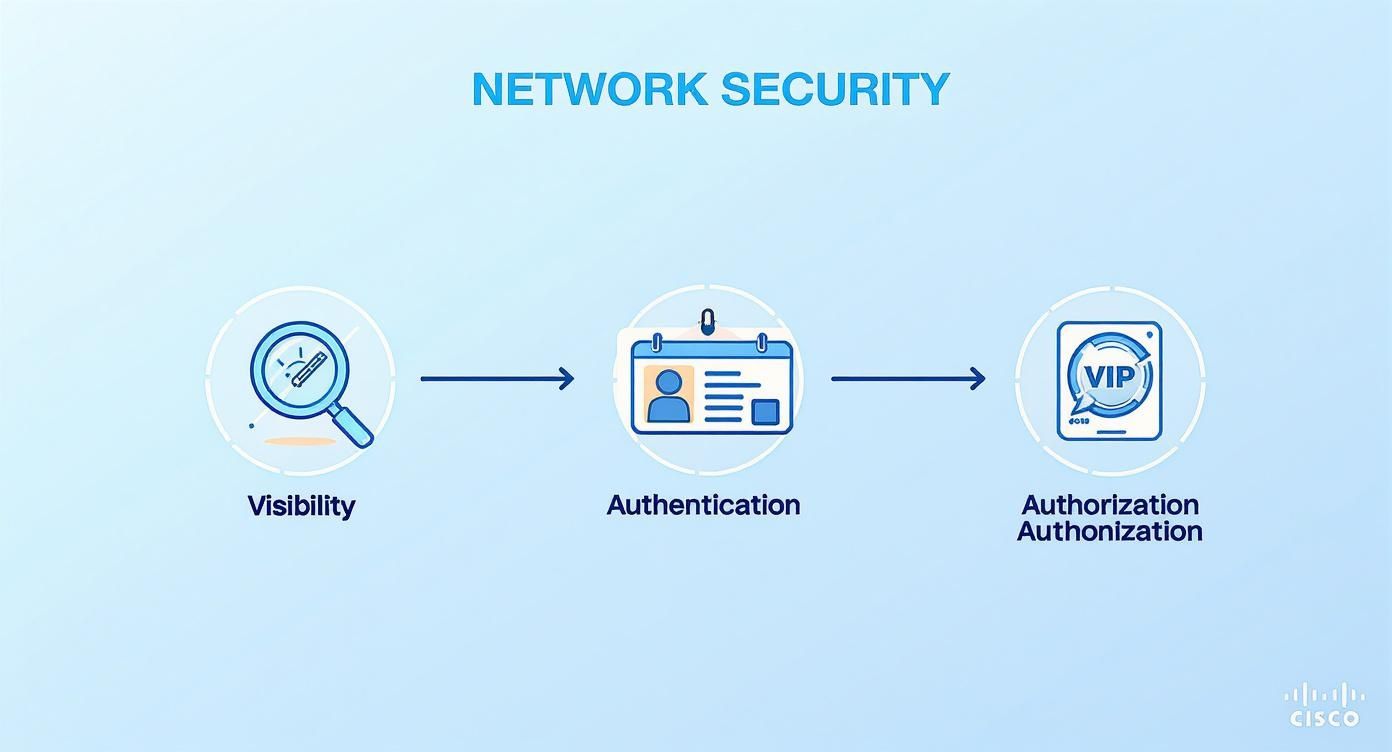
The Three Pillars of Access Control
First up is Visibility. Like a bouncer scanning the line, ISE identifies every single device attempting to connect. It doesn't matter if it's a known corporate machine or a guest's brand-new tablet; nothing slips by. This is the essential first step—after all, you can't protect what you can't see.
Next, we have Authentication. This is the part where ISE asks for I.D. Using the industry-standard RADIUS protocol, ISE talks to your network gear (like access points from Cisco or Meraki) and challenges the device for its credentials. This could be a simple username and password, a secure digital certificate, or a special pre-shared key via IPSK or EasyPSK.
The point of authentication is straightforward: prove you are who you claim to be. This check is the bedrock of network security, making sure only legitimate users and devices get a foot in the door.
Finally, there's Authorization. Once ISE confirms a device's identity, it has to decide what that device is allowed to do and where it's allowed to go. This is the difference between a general admission ticket and a backstage pass. Based on security policies you define, ISE grants precise permissions. For instance, a visitor connecting through a Captive Portal might get internet-only access, keeping them safely away from your internal servers. This is network segmentation in action.
Solutions like IPSK and EasyPSK take this a step further. Instead of a single Wi-Fi password for everyone, each user or device gets its own unique key. ISE uses that key to authenticate the device and assign the right level of access automatically. This approach makes managing hundreds or thousands of different devices in a BYOD world much cleaner and way more secure. You can read more about how IPSK with RADIUS authentication works to see it in a real-world context.
This powerful trio—visibility, authentication, and authorization—is exactly how ISE builds a modern, intelligent security perimeter around your network.
Putting ISE to Work in the Real World
Theory is great, but how does this actually help? Let's look at how Cisco ISE solves real-world problems for different organizations where secure network access is non-negotiable.
These examples show how ISE isn't just a security tool—it's a core part of making a business run smoothly and safely. This is no surprise, given Cisco’s massive footprint in the networking world. In fact, by 2025, Cisco is projected to hold a 76.89% market share in networking technologies. That means solutions like ISE are becoming a standard piece of modern IT infrastructure. You can dive deeper into these trends by checking out the full research on network technology leaders.
This diagram breaks down the fundamental process ISE uses to secure every single connection, from the moment a device appears to the point it's granted access.
As you can see, no device gets a free pass. It has to be seen, identified, and authenticated before it's given the right level of network access.
Education and Corporate BYOD
Picture a university campus. You have thousands of students, faculty, and guests all wanting to connect their personal laptops and phones. This is a classic BYOD (Bring Your Own Device) headache in an Education environment.
ISE steps in to manage this chaos. It can tell the difference between a student's smartphone and a professor's tablet, automatically placing them on the right network. Students get access to the internet and learning resources, while faculty can securely connect to internal databases and administrative systems. The exact same logic applies in a Corporate office, letting employees use their own devices without ever putting company data in jeopardy. You can explore more about solutions for managing network access in education.
Retail Guest Wi-Fi and Secure Payments
Now, let's switch gears to a busy Retail store. Offering free guest Wi-Fi is practically a requirement these days, but it can also be a huge security risk.
Cisco ISE powers branded Captive Portals that let shoppers log in with ease. More importantly, it completely isolates all that guest traffic, walling it off from the store’s critical payment systems and internal network.
But what about devices that don't have a user, like inventory scanners or digital signage? For those, authentication solutions like IPSK or EasyPSK are a perfect fit. Instead of using one shared Wi-Fi password for everything (a major security flaw), these tools assign a unique key to each device or group. This approach drastically simplifies management for IT teams while locking things down tight. It’s this kind of granular, real-world control that makes Cisco ISE so powerful.
What Makes ISE a Security Powerhouse?
So, what’s the secret sauce that makes Cisco ISE such a go-to tool for network professionals? It’s not just one feature, but a combination of powerful capabilities that work in harmony to build a seriously tough security posture. Think of ISE as the single, authoritative gatekeeper for your entire network.
The Cisco Identity Services Engine (ISE) is a network access control (NAC) platform at its core. It's built to lock things down by enforcing consistent security rules for every single user and device trying to get onto your network. As a flagship product in Cisco's security lineup, ISE brings policy enforcement, device visibility, and zero-trust principles under one roof—all of which are non-negotiable in today's complex environments.
Centralized Policy and Deep Visibility
Picture this: you have to manage security rules on hundreds of different switches, routers, and wireless access points. It’s an absolute nightmare just waiting to happen. ISE completely changes the game by acting as a centralized policy engine. You build your access rules in one dashboard, and ISE takes care of pushing them out across your entire Cisco and Meraki infrastructure.
This unified control really hinges on two critical functions:
- Device Profiling: ISE is smart enough to automatically identify and classify anything that connects to your network. It knows the difference between a company laptop in a BYOD setup, a handheld scanner in a Retail warehouse, or a student's personal phone in an Education environment.
- Posture Assessment: Before letting a device on the network, ISE can perform a health check. Is its antivirus software current? Are the latest operating system patches installed? If a device fails this check, it can be automatically shunted to a quarantine network until it's brought up to standard.
The real magic of ISE is its ability to make intelligent, context-aware decisions. It doesn't just ask "who are you?" but also "what kind of device are you using, where are you connecting from, and is your device even secure enough to be here?"
A Cornerstone of Zero Trust Security
This brings us to its most critical role: ISE is a foundational building block for a Zero Trust security model. The philosophy behind Zero Trust is simple but powerful: never trust, always verify. Every single access request is challenged and authenticated, no matter if the user is sitting in your office or connecting from a coffee shop.
By enforcing strict access controls and segmenting users and devices into isolated zones, ISE gets rid of the old, dangerous assumption of internal trust. Strong authentication solutions are absolutely vital here. A great example is multi-factor authentication, and you can learn more about what multi-factor authentication is and why it's so crucial.
Whether it's through secure Captive Portals for guest access or advanced methods like IPSK and EasyPSK for IoT devices, ISE gives you all the tools you need to build a truly resilient network from the ground up.
Got Questions About Cisco ISE? We've Got Answers
If you're just getting started with Cisco ISE, a few questions always seem to pop up. Let's clear the air on some of the most common ones.
Does Cisco ISE Only Play Nice with Cisco Gear?
That's a common misconception. While ISE is designed for incredibly tight integration with Cisco and Meraki hardware, it’s not locked into a proprietary bubble.
It's built on open standards like RADIUS, which means it can talk to and manage network devices from many other vendors. That said, to really unlock its most advanced capabilities and get that seamless, "it just works" experience, you'll get the best results by keeping it in the Cisco family.
Is Cisco ISE a Headache to Set Up?
We won't sugarcoat it—the initial deployment can be complex. A tool this powerful needs thoughtful planning to make sure your security policies are mapped out correctly from the get-go.
But here’s the trade-off: once it's up and running, daily management becomes a breeze. Everything is handled from a single, centralized dashboard. Whether you're managing BYOD policies for a Corporate headquarters or securing thousands of devices across a huge Education campus, it all happens in one place.
How Does ISE Make Guest Wi-Fi Better?
For guest access, especially in places like Retail or hospitality, ISE is a total game-changer. It lets you build slick, custom-branded Captive Portals for a professional and easy login experience.
More importantly, it completely walls off guest traffic from your secure internal network. This ensures you can offer visitors great Wi-Fi without ever putting your sensitive company data at risk. It’s the kind of bulletproof authentication solution that modern networks demand.
Ready to take the complexity out of your network security and guest Wi-Fi? At Splash Access, we're experts at integrating with Cisco Meraki to build powerful and user-friendly authentication systems.
See what our platform can do for you at https://www.splashaccess.com.