Ever walked into a busy school, retail store, or corporate office and wondered how hundreds of people can jump on the Wi-Fi without everything grinding to a halt? The secret weapon is a clever piece of hardware called a managed switch. Think of it as the friendly, intelligent traffic cop for your network, making sure everything runs smoothly, securely, and without any digital traffic jams.
Meet Your Network’s Control Center
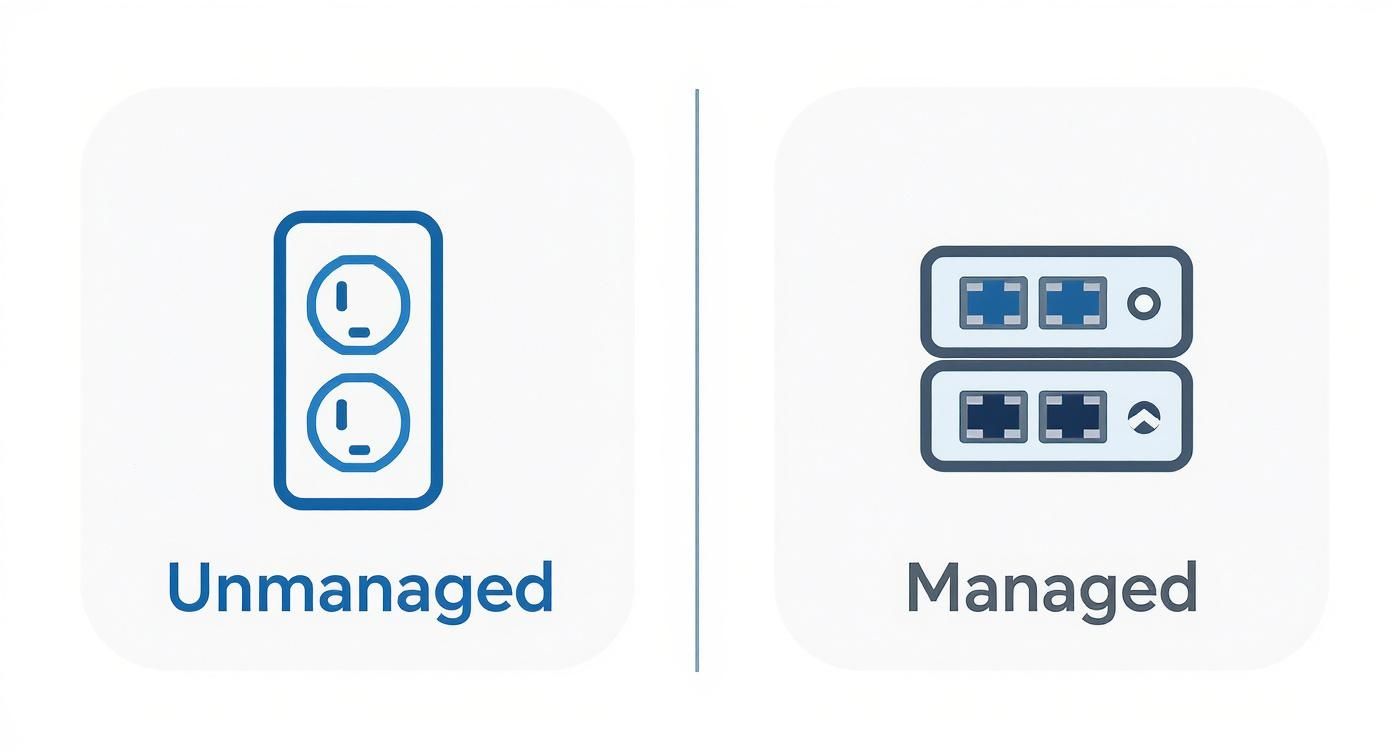
Let's break it down with a simple analogy. An unmanaged switch is like a basic power strip for your network. You plug everything in, and it shares the connection. It works, but it's a bit of a free-for-all with zero control.
A managed switch, on the other hand, is a smart power hub with a central control panel. It gives you the power to see, manage, and prioritize everything happening on your network. It's like having a remote control for your entire digital world.
This level of control is a game-changer in today's connected world. For instance, in an Education setting, a managed switch can create separate, secure Wi-Fi zones for students and staff. In Retail, it can give payment systems the VIP treatment, ensuring transactions fly through even when the guest Wi-Fi is packed. For corporate BYOD (Bring Your Own Device) environments, it’s the key to letting everyone connect their personal gadgets without giving your IT manager a headache over security.
This visual shows the core difference: one is a simple connector, while the other is an intelligent controller.
The infographic perfectly illustrates that a managed switch gives you the visibility and configuration tools that unmanaged switches simply cannot offer.
To make this even clearer, here's a quick rundown of how they stack up against each other.
Managed vs Unmanaged Switch at a Glance
| Feature | Managed Switch | Unmanaged Switch |
|---|---|---|
| Control | Full administrative control over network traffic and ports. | No control; works automatically out of the box. |
| Security | Advanced security features (VLANs, port security, etc.). | Basic security; no advanced features. |
| Performance | Can prioritize traffic (QoS) for better performance. | No traffic prioritization. |
| Configuration | Requires setup via a command-line interface or web GUI. | Plug-and-play; no configuration needed. |
| Cost | Higher initial cost due to advanced features. | Lower cost, ideal for simple needs. |
| Best For | Businesses, schools, and complex home networks. | Small offices, home use, or simple network expansion. |
As you can see, the choice really comes down to whether you need to actively manage and secure your network connections.
Why This Control Matters
So, what can you actually do with all this control? Managed switches from industry leaders like Cisco and Meraki allow you to implement powerful security and user management features. For example, you can set up Captive Portals—those are the friendly login pages you see when connecting to guest Wi-Fi at a hotel or coffee shop.
These switches are also the foundation for modern Authentication Solutions. Instead of one shared password for everyone (a big security no-no!), you can use advanced methods like IPSK (Individual Pre-Shared Key) or EasyPSK. This means each person or device gets its own unique network key, which is a huge leap forward for security.
A managed switch transforms your network from a passive, one-way street into an active, intelligent system. You're no longer just a spectator; you're the traffic director, ensuring the most important data gets where it needs to go without delay.
For those curious about how these advanced features are put into practice, you can learn more about what Cisco Meraki is and how its cloud-managed approach simplifies these complex tasks. Ultimately, this foundation of control is what makes a secure, high-performing network possible.
Unlocking Granular Network Control
A managed switch isn't just a simple hub for connecting your devices; it's more like the central nervous system of your network. It gives you the power to direct and prioritize traffic with incredible precision.
Think of it like this: an unmanaged switch is a simple garden hose—you turn it on, and water goes everywhere. A managed switch, on the other hand, is a sophisticated irrigation system with programmable valves, timers, and sensors for every single plant. You get to decide exactly what gets watered, when, and how much.
This kind of fine-tuned control is exactly why the market for these devices is booming. The global fully managed switch market was valued at around USD 2.78 billion and is expected to climb to USD 4.23 billion by 2032. This isn't just growth for growth's sake; it's driven by a real need for advanced features that help businesses manage their network traffic and security effectively.
So, let's pull back the curtain on the features that give you this level of command.
Creating Secure Mini-Networks with VLANs
One of the most powerful tools in a managed switch’s arsenal is the ability to create VLANs (Virtual Local Area Networks). Imagine you have one large, open-plan office. A VLAN lets you digitally partition that single space into separate, secure "rooms" without putting up a single physical wall.
For instance, a school could use one physical switch to create three totally distinct networks:
- Student Network: This VLAN gives students internet access on their devices but keeps them completely walled off from sensitive administrative systems.
- Faculty Network: A separate network that provides teachers access to essential internal resources, like shared drives or grading software.
- Guest Network: A completely isolated network for visitors, often requiring a login through a Captive Portal. This ensures guests can get online without ever touching internal data.
This segmentation is a huge security advantage, especially in Retail environments or corporate offices with BYOD (Bring Your Own Device) policies. It makes sure that traffic from secure payment terminals, employee laptops, and the public guest Wi-Fi never cross paths.
Prioritizing What Matters with QoS
Another game-changer is Quality of Service (QoS). Think of QoS as creating a VIP express lane on your network's highway. It allows you to tell the switch which types of data are most important and must get through first, no matter what.
Picture a busy office. One person is downloading a massive design file, someone else is streaming music, and the CEO is in the middle of a crucial video conference call. Without QoS, all that data competes for bandwidth, and the result is often a choppy, unprofessional-looking video call for the boss. Not good.
With QoS, you can tag that video call traffic as high-priority, ensuring it gets the bandwidth it needs to remain perfectly smooth, even when the rest of the network is congested. It's essential for keeping business-critical applications running flawlessly.
For a deeper dive into these core differences, you can check out this detailed breakdown of a managed vs unmanaged switch.
Leading brands like Cisco and Meraki have made it incredibly easy to configure these rules. You can prioritize voice calls, video streams, or specific business apps with just a few clicks. This control also helps with Authentication Solutions like IPSK or EasyPSK, ensuring the login process itself is always fast and responsive for people joining the network.
Managed Switches in the Real World
It’s one thing to talk about the technical features of a managed switch, but seeing how they solve real-world problems is where it all clicks. Let's step away from the spec sheets and look at how these smart devices make a difference in busy, everyday environments.
Think about a bustling retail store. You've got point-of-sale (POS) systems taking payments, staff zipping around with handheld inventory scanners, and customers hopping on the guest Wi-Fi. A managed switch is the unsung hero here, making sure a credit card transaction always gets priority over a customer streaming video.
This isn't just a nice-to-have feature; it’s a business essential.
Enhancing Security in Education
School and university campuses can be a real headache for network admins. You have students, faculty, and administrative staff all sharing the same physical network, but their access needs and security levels are worlds apart.
This is the perfect job for a managed switch from a provider like Cisco Meraki. An IT admin can quickly segment the network into separate, secure virtual LANs (VLANs) for each user group:
- Student Wi-Fi: Gives students internet access but walls them off from sensitive administrative files. This is often where you’ll see a Captive Portal for logging in.
- Faculty Network: Provides teachers with the access they need to grading software, shared drives, and other internal tools.
- Admin Network: Creates a high-security zone for financial data, student records, and other confidential information.
By keeping these groups isolated, a security breach on one network—like a virus on a student's laptop—can't spread to critical systems. It’s the digital backbone of a safe and productive learning environment.
Streamlining Retail Operations
In the Retail world, network performance is directly tied to revenue. If your payment terminals go offline or your inventory scanners lose connection, sales grind to a halt.
A managed switch guarantees your most critical operations always have the bandwidth they need. It essentially creates a digital "express lane" for POS terminals and inventory tools, ensuring they run smoothly even when the guest Wi-Fi is slammed during a holiday rush.
This simple act of traffic prioritization prevents frustratingly slow transactions and keeps checkout lines moving. It’s a direct investment in a better customer experience and protected sales.
Supporting Corporate BYOD Policies
More and more companies have a Bring Your Own Device (BYOD) policy, where employees use their personal phones, tablets, and laptops for work. This is fantastic for convenience, but it can be a real security challenge. How do you let personal devices on the corporate network without risking a data breach?
A managed switch is the key. It enables powerful Authentication Solutions like IPSK or EasyPSK, which give each employee a unique key for their devices. This is a massive security upgrade from a single, shared Wi-Fi password that could be leaked or compromised. When an employee leaves, their personal access key can be disabled in seconds without disrupting anyone else.
This level of granular control lets businesses enjoy the flexibility of BYOD without putting their core network at risk. For companies looking to do this, you can explore versatile switch options for modern networks built to handle these exact challenges.
Strengthening Security with Smart Authentication
Modern network security is about so much more than a simple password. Think of a managed switch as the central gatekeeper, giving you the power to implement advanced methods for verifying who—and what—is connecting to your network. This is where you graduate from basic access to smart, context-aware security.
One of the most common examples is the Captive Portal. You’ve definitely run into this before. It's that login page that pops up when you connect to the Wi-Fi at an airport, hotel, or your local coffee shop. That entire process is orchestrated by a managed switch working in tandem with the wireless access points. It's an indispensable tool for managing guest access, especially in Retail and public spaces.
But for your own team, especially in corporate or Education settings, security needs to be tighter and more seamless. That's where some of the more advanced authentication solutions, all enabled by the intelligence of a managed switch, really shine.
Beyond the Shared Password
Let's be honest: the old method of giving everyone the same Wi-Fi password is a massive security hole. If just one person leaves the company or a password leaks online, you’re stuck having to update it on every single device. It’s a management nightmare, and it's far from secure.
This is exactly the problem that managed switches from brands like Cisco and Meraki are designed to solve. They have built-in support for smarter Authentication Solutions. Two of the most popular methods are:
- IPSK (Individual Pre-Shared Key): Instead of a single password for everyone, IPSK technology lets you assign a unique "Wi-Fi key" to each specific user or device. It's like giving every employee their own personal key to the office network.
- EasyPSK: This takes the IPSK concept and makes it incredibly straightforward for IT admins to generate and manage thousands of unique keys without the complexity you’d normally expect at the enterprise level.
This approach is a total game-changer, especially for BYOD Corporate sectors. When an employee leaves, you just revoke their individual key. Nobody else is affected, and your network remains secure. Simple.
A managed switch is the engine that makes these modern authentication methods work. It enforces the rules, making sure only devices with a valid, unique key are allowed to connect. In effect, it creates a personalized security perimeter for every single user.
A Foundation for Secure Access
Ultimately, these features are all about building a network that’s both secure and manageable from the very beginning. To truly lock down your network's defenses, implementing robust network access control policies is crucial, and that’s a core capability of any good managed switch. They give you the fine-grained control needed to see who is on your network, what they are doing, and how they are connecting.
When you start combining features like VLANs with smart authentication like IPSK, you build a powerful, layered defense system. A managed switch is your foundation for a truly secure and efficient modern network.
Navigating Network Layers Like a Pro
When you start digging into managed switches, you'll inevitably hear the terms Layer 2 and Layer 3. It sounds a bit technical, but the idea is actually pretty straightforward once you think about it in real-world terms.
Imagine a Layer 2 switch as the local mail carrier for a single neighborhood. It's an expert at getting letters (data packets) to the right houses (devices) on its specific route. It does this by knowing the unique mailing address of each house (its MAC address). But ask that mail carrier to deliver a package to a different town? They're lost. That’s not their job.
Now, think of a Layer 3 switch as the central post office for the entire region. It doesn't just know local addresses; it understands the whole map. It can read the destination city and state on the package (the IP address) and figure out the most efficient route to get it there, even if it has to cross multiple networks (VLANs) to do it.
When Do You Need a Layer 3 Switch?
For a small office with a handful of devices, a Layer 2 switch usually works just fine. It keeps everything connected on that simple, single network. But as you grow, you'll start to feel the pinch. Layer 2 networks can get bogged down by broadcast traffic—like junk mail sent to every single house—which slows everything down for everyone. Learning about certain protocols can help here, and you can start by understanding what the Spanning Tree Protocol is in our detailed guide.
This is precisely where a Layer 3 switch steps in and becomes a necessity. Its ability to route traffic is crucial in more complex setups:
- Education: Think of a large university campus. The dorms, library, and faculty offices all have their own networks. A Layer 3 switch is what connects them, intelligently routing traffic so a student in a dorm can access library resources seamlessly.
- Retail: A big department store might have separate networks for its point-of-sale systems, inventory management, and the free guest Wi-Fi. A Layer 3 switch keeps these networks isolated for security but allows them to communicate when necessary.
- BYOD Corporate Sectors: In a multi-story office, each department—like marketing, finance, and engineering—might be on its own virtual network (VLAN). A Layer 3 switch acts as the central hub, managing traffic flow between them so the marketing team's video uploads don't slow down the finance department's critical applications.
A Layer 3 switch is the upgrade you make when your network outgrows a single, flat environment. It’s the intelligence that allows different parts of your organization to talk to each other securely and efficiently as you scale.
This routing capability is a big deal, and it’s why the Layer 3 managed switch market is valued at an estimated USD 15 billion. Businesses need that advanced IP routing and security, especially in large enterprise and data center settings. This is the technology that enables powerhouse brands like Cisco and Meraki to deliver sophisticated solutions like Captive Portals and advanced Authentication Solutions like IPSK across complex, segmented networks.
Choosing the Right Managed Switch for Your Business
So, you're ready to pick a managed switch. The key is to avoid overbuying or under-buying by matching the switch's capabilities to what your network actually needs.
Let's start with the most basic question: scale. How many devices are you plugging in? Answering this tells you the port count you need. You might only need a simple 8-port switch for a small satellite office, but a busy corporate floor could easily require a 48-port model to connect every computer, printer, and access point.
Next up, think about what you're plugging in. Many of the devices we rely on today—like Wi-Fi access points, VoIP phones, and security cameras—run on Power over Ethernet (PoE). A switch with PoE support is a game-changer. It sends both power and data through the same Ethernet cable, which means you can ditch all those clumsy power adapters and simplify your cabling.
Cloud Management for Modern Networks
For certain environments, the management interface itself is a massive part of the decision. If you're running a network in Education, Retail, or a corporate setting with a bring-your-own-device (BYOD) policy, ease of use is everything.
This is where cloud-managed switches, like those from Cisco Meraki, really shine. Forget about staring at a command-line interface. These systems give you a clean, web-based dashboard that puts everything at your fingertips.
From a single pane of glass, you can set up a Captive Portal for guest Wi-Fi access or configure sophisticated Authentication Solutions like IPSK and EasyPSK. This approach takes powerful, enterprise-grade features and makes them accessible to just about any IT team.
Imagine being able to monitor your entire network, pinpoint problems, and tweak security settings from anywhere with an internet connection. That's the power of cloud management.
As you weigh your options, don't forget the bigger picture. When it's time to upgrade down the road, it's worth knowing the benefits of recycling networking equipment. The best choice is a switch that not only handles your performance needs today but also fits your budget, security posture, and future growth plans.
Frequently Asked Questions
Managed switches are powerful, and with that power comes a lot of questions. It's only natural. Let's tackle some of the most common ones head-on.
Can I Use a Managed Switch at Home?
You absolutely can, but the real question is, should you? For most home setups—streaming, browsing, and a few smart devices—an unmanaged switch is a perfectly simple and cost-effective solution.
However, a managed switch really starts to make sense in a more complex environment. Think of a high-tech smart home, a business network, or even an Education campus where you need granular control over who gets on the network and what they can access.
Are Managed Switches More Secure?
Without a doubt. This is one of their biggest selling points. Unlike their "plug-and-play" cousins, managed switches give you a whole toolkit of security features.
You can segment your network into virtual LANs (VLANs) to keep sensitive data isolated, block unauthorized devices from even connecting, and roll out sophisticated Authentication Solutions. Imagine setting up a Captive Portal for guests or using IPSK to safely manage a corporate BYOD policy—that's the kind of security a managed switch delivers.
Do I Need to Be a Tech Expert to Use One?
In the past, the answer was a firm "yes." You needed to be comfortable with command-line interfaces and complex networking concepts. But things have changed dramatically.
Modern cloud-managed switches, like those from pioneers like Cisco Meraki, have turned this idea on its head. They’ve replaced the cryptic command line with intuitive, web-based dashboards. Now, just about anyone can configure, monitor, and manage a powerful network without needing a deep background in IT.
Ready to unlock the full potential of your network with smart authentication and guest Wi-Fi? Splash Access provides instantly deployable captive portals and advanced IPSK solutions built for Cisco Meraki. Learn more about our solutions at Splash Access.