Hey there! When people start talking about the performance of a network, most of us immediately think about speed. But honestly, speed is just one piece of the puzzle. Real performance is all about creating a reliable, consistent, and super-smooth online experience for every single person, whether they're a student on a university campus, a shopper browsing in your store, or an employee in a busy office.
What Really Defines Network Performance?
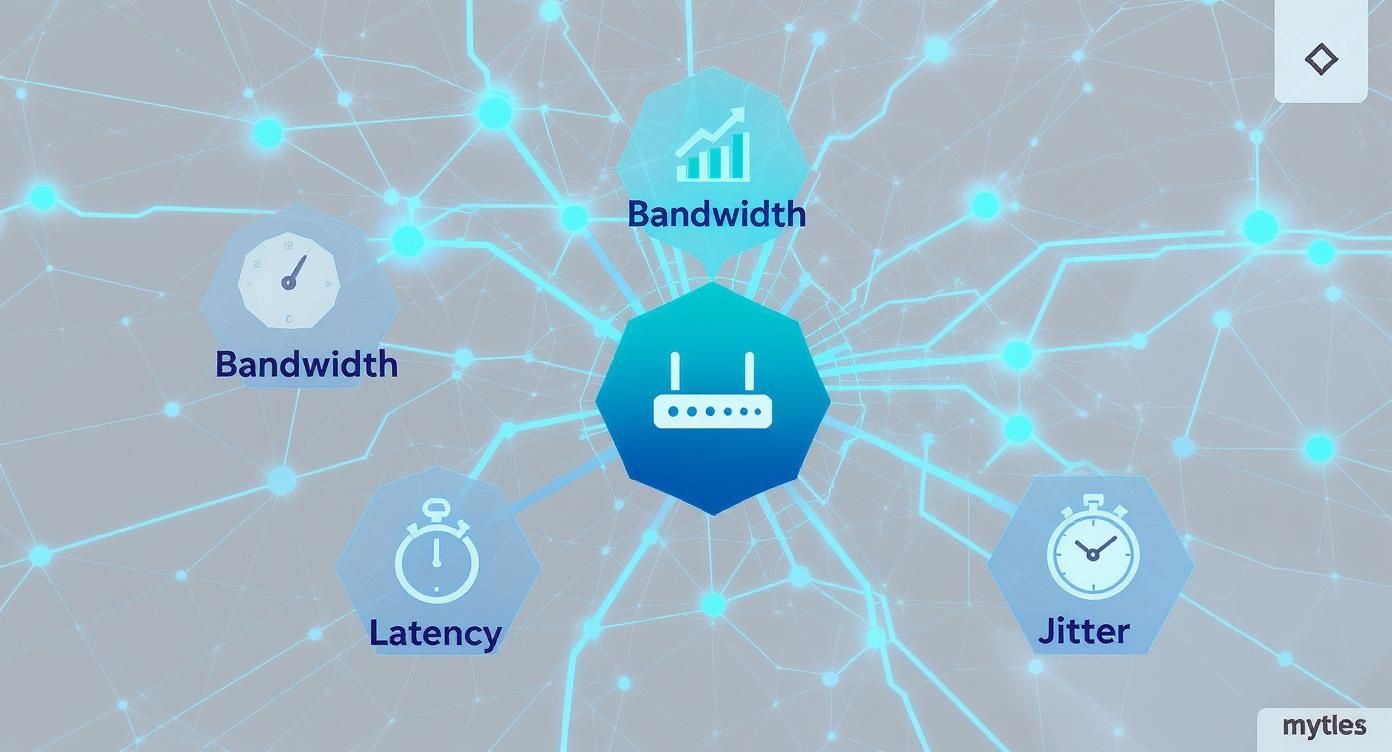
Have you ever run a speed test that shows a fantastic result, but your Wi-Fi still feels painfully slow? It's a common frustration! That’s because genuine network performance isn't just about raw speed. It's a delicate balance of four key factors all working together in harmony.
Getting this balance right is the secret sauce to a fantastic user experience, especially in crowded places like schools (Education), busy stores (Retail), and modern offices where everyone brings their own device (the classic BYOD Corporate challenge).
To make this clearer, let's use an analogy. Think of your network as a highway system.
The Four Pillars of a Great Network
A truly solid network juggles a few critical factors to keep everything running without a hitch. The good news is, in environments using top-tier hardware from amazing brands like Cisco and Meraki, managing these elements is thankfully much simpler. Let's break down the four most important metrics.
Key Network Performance Metrics at a Glance
This table sums up the four core metrics that every network admin obsesses over. Using our highway analogy, you can see how they all play a different but equally important role.
| Metric | What It Measures | Simple Analogy | Why It Matters for Wi-Fi |
|---|---|---|---|
| Bandwidth | The maximum amount of data that can be transferred in a set time. | The number of lanes on a highway. | More lanes mean more users can stream, download, and browse at once without slowdowns. |
| Throughput | The actual amount of data successfully transferred over time. | The number of cars that actually make it through the highway in an hour. | This is the "real-world" speed your users experience, which is always less than the max bandwidth. |
| Latency | The time it takes for a data packet to travel from source to destination. | The travel time for one car to get from Point A to Point B. | Low latency is vital for video calls and gaming, preventing that annoying lag. |
| Jitter | The variation in latency over time. | The inconsistency in travel time. Some cars take 20 mins, others 25, others 30. | High jitter causes choppy video and broken-up audio calls because data arrives out of order. |
As you can see, you need more than just a wide highway (bandwidth). You need a steady flow of traffic (throughput), a quick travel time (low latency), and predictable arrival times (low jitter).
This is where all the pieces come together.
The infographic above perfectly illustrates how these elements are interconnected. A high-performance network is all about striking the right balance, not just maxing out one metric at the expense of the others.
This is also where modern Authentication Solutions, like Captive Portals equipped with IPSK or EasyPSK, become so important. Think of them as the friendly gatekeepers, ensuring only authorized users get access to your carefully balanced network resources.
Of course, understanding these concepts is just the first step. The real work comes in measuring and managing them, which is where specialized network performance monitoring tools come into play.
The growing need to manage this complexity is why the global Network Performance Monitoring (NPM) market is booming. It was valued at around $2.07 billion in 2025 and is projected to hit $4.83 billion by 2032. That's a huge jump, and it shows just how critical this stuff has become.
Common Hurdles That Degrade Guest Wi-Fi
Ever walked into a busy coffee shop or airport and found the guest Wi-Fi practically unusable? It's a familiar story. What you expect to be a smooth connection can quickly get bogged down by a few common, behind-the-scenes challenges, especially in crowded places.
Picture a university lecture hall where hundreds of students pull out their devices at the same time. This flood of BYOD (Bring Your Own Device) traffic puts an incredible strain on the network. Each phone, tablet, and laptop is fighting for a slice of the same digital pie, creating a massive traffic jam that slows everything to a crawl. This is an everyday battle in the Education and Corporate worlds.
The Invisible Walls of Interference
One of the biggest culprits you can't even see is interference. Think of your Wi-Fi signal like a quiet conversation. Now, try having that same conversation in the middle of a noisy party. It’s tough to hear anything clearly, right?
That’s what happens to your Wi-Fi. Signals from other networks, Bluetooth gadgets, microwave ovens, and even concrete walls can disrupt and weaken your connection. The more networks and devices you cram into one space—like a shopping mall in the Retail sector—the more "noise" you get. To really dig into this, you can learn more about the various sources that cause interference with your Wi-Fi.
"A great network isn't just about having the latest hardware. It's about intelligently managing the chaos of the real world—from signal interference to the sheer volume of devices all demanding a perfect connection simultaneously."
Outdated Hardware and Unmanaged Access
Another major issue is simply old equipment. Routers and access points from years ago were never built for today’s world, where everyone carries multiple connected devices. While a foundation of solid hardware from vendors like Cisco Meraki is a great start, even the best gear will struggle without smart management.
This is why controlling who gets on the network—and how—is so critical. Leaving your Wi-Fi open or protected by a single, shared password creates a free-for-all that tanks performance for everyone.
To truly optimize the performance of a network, you need more than just raw power. You need intelligent tools that manage the flow of traffic. This is where solutions come in:
- Captive Portals: Think of these as the friendly front door to your network. They act as a welcome gate, ensuring only authorized users can get online.
- Authentication Solutions: More advanced methods like IPSK and EasyPSK assign a unique key to each user, which stops password sharing and boosts security.
These tools are what transform a chaotic, congested network into an orderly and efficient one.
Using Captive Portals to Enhance Network Access
Think of a Captive Portal as the friendly front door to your guest Wi-Fi. It's that first page you see when you try to connect in a café, airport, or hotel, and its design is absolutely critical for a good user experience. A well-crafted portal, like the ones you can build with Splash Access, is so much more than a simple login screen—it’s a powerful tool for smooth onboarding, better security, and even improving the overall performance of a network.
By acting as a gatekeeper, a captive portal helps you manage your bandwidth by controlling exactly who gets onto the network. This simple step prevents unauthorized users from hogging precious resources, which is a massive headache in any busy public space. The result? The network stays stable and responsive for the people who are actually supposed to be using it.
Tailoring Access for Different Needs
The real beauty of a captive portal is its flexibility. It can be molded to fit just about any environment.
- In a Retail store, it becomes a marketing touchpoint, letting you offer a coupon or invite shoppers to join your mailing list.
- In a large corporate office with a BYOD policy, it ensures only employees and registered guests can get online, protecting sensitive company information.
- In an Education setting, a university can use its portal to make sure only authorized students and faculty can access the primary network. This kind of segmentation is essential for maintaining a high-performance academic network while still offering a separate, controlled connection for guests.
A captive portal transforms your Wi-Fi from a simple utility into a strategic asset. It’s the first interaction a user has with your network, making it a critical opportunity to set expectations for security, performance, and user experience.
This initial handshake between the user and the network is where an intelligent system really proves its worth. When you pair Splash Access with robust hardware from a company like Cisco Meraki, you create an authentication process that’s both user-friendly and secure. This combination actually improves network performance by making the connection process cleaner and safer, rather than adding another hurdle. You can explore our complete guide on how a modern Wi-Fi captive portal can work for your business.
Paving the Way for Better Authentication
A captive portal also sets the stage for more advanced security. It can be the first step in a multi-layered authentication process, guiding users toward Authentication Solutions like IPSK or EasyPSK. These methods give each user a unique key, which completely gets rid of the security nightmare of shared passwords and gives you fine-grained control over every single connection.
As networks get more complex, the demands we place on them are greater than ever. The global rollout of 5G has brought gigabit speeds and ultra-low latency into the mainstream, both of which are vital for bandwidth-hungry apps and the Internet of Things (IoT). To keep pace, modern network management is increasingly turning to artificial intelligence to predict and fix performance problems before they ever affect a user.
Securing Every Device with Modern Authentication
The "Bring Your Own Device" (BYOD) trend isn't just a buzzword anymore; it's a reality in every office, campus, and public space. People expect to connect their personal phones, laptops, and tablets to your Wi-Fi. While this is fantastic for convenience, it can be a massive security headache and drag down your network performance.
So, how do you secure hundreds or even thousands of personal devices without making people jump through hoops? The old-school approach of a single, shared password for everyone is like leaving the front door wide open. Once that password leaks, your entire network is exposed.
Shifting from Shared Passwords to Unique Keys
This is where modern Authentication Solutions completely change the game. Technologies like Identity Pre-Shared Key (IPSK), and our simplified version, EasyPSK, make the shared password problem a thing of the past. Instead of one password for everyone, this method generates a unique, private Wi-Fi key for every single user.
It’s the difference between leaving a key under the doormat for the whole neighborhood and giving each person their own personal key to the building. This approach is a lifesaver for any place managing a constant flow of new devices.
In a BYOD world, your network is only as secure as its weakest link. Moving to individual, automated credentials through IPSK and EasyPSK transforms security from a constant worry into a managed, scalable asset.
This technology is especially powerful in demanding environments:
- Education: Schools can effortlessly manage thousands of student and staff devices, guaranteeing that only authorized users access academic resources. When a student leaves, revoking their access is as simple as deleting their key.
- Retail: Stores can provide secure Wi-Fi for staff to use with inventory and POS systems, keeping that traffic totally separate from the public guest network.
- BYOD Corporate: Companies can safely onboard employee devices without complicated IT setups, making sure personal phones and laptops are secure before they ever touch the network.
Making Enterprise Security Simple
The best part? This level of security doesn't have to be complicated. When you pair a solution like Splash Access’s EasyPSK with powerful hardware from Cisco Meraki, the whole process becomes incredibly straightforward. Our system automates the creation and management of these unique keys, giving you top-tier security that’s as easy to use as your home Wi-Fi.
For a deeper look into protecting individual devices, it's helpful to understand what endpoint security entails.
Before we dive deeper, let's compare the old way with the new.
Traditional vs. Modern Wi-Fi Authentication
| Feature | Traditional Shared Password | IPSK / EasyPSK Solution |
|---|---|---|
| Security | Low. One leaked password compromises the entire network. | High. Each user has a unique key. A single compromised key only affects one user. |
| Accountability | None. All traffic comes from the same shared credential. | High. Activity is tied directly to an individual user, making it easy to track. |
| Management | Difficult. Changing the password means updating every single device. | Easy. Onboarding is automated, and revoking access for one user takes a single click. |
| User Experience | Simple but insecure. Users often share the password freely. | Seamless. Users get their own key and connect once without complex configurations. |
As you can see, the move to a modern solution like IPSK is a massive leap forward.
By giving every user their own key, you're not just boosting security—you're getting precise control over your network. You can see exactly who is connected, instantly kick off a single device, and even set different rules for different people. This level of control is key to maintaining great network performance and can be stacked with other security layers. You can learn more about how this works in our guide on what is multi-factor authentication.
Ultimately, this secure, controlled access stops network abuse and makes sure your valuable bandwidth is saved for the people who actually need it, leading to a faster, better experience for everyone.
Putting Network Performance into Practice
Theory is one thing, but how does all this work in the real world? A high-performance network isn't just about fancy hardware. It’s about smart management—controlling who gets access, when, and how, especially when things get busy. This is where the right tools, working together, make all the difference.
Think about a university campus during finals week. It's a pressure cooker. Thousands of students are hitting the network simultaneously to download research, upload assignments, and jump into online study sessions. This huge wave of personal devices—what some might call BYOD Corporate in a business setting—can easily bring a standard network to its knees, causing headaches and risking missed deadlines.
A Blueprint for the Education Sector
In a high-stakes environment like this, you need a solid plan. It starts with a strong hardware foundation, like deploying Meraki access points across campus. But the real game-changer is adding smart access controls on top. A Splash Access Captive Portal acts as the gatekeeper, making sure only registered students and staff get on the primary network.
Once a student is verified, EasyPSK steps in to assign them a unique, personal Wi-Fi key. This isn't just a small security tweak; it stops password sharing in its tracks and gives administrators a clear view of who is using the network. This allows them to allocate bandwidth fairly and maintain the overall performance of a network, even when it's pushed to its limits.
By segmenting access and securing each connection, a university can transform its Wi-Fi from a potential bottleneck into a powerful learning tool, even under the heaviest loads.
Powering the Retail Experience
Now, let's pivot to a completely different scene: a busy department store. The network demands here are twofold. You need to offer great guest Wi-Fi to shoppers, but you also have to protect your mission-critical systems like cash registers and inventory scanners.
A Cisco and Splash Access combination is perfect for this. The public-facing Captive Portal can give shoppers free Wi-Fi after they agree to a marketing opt-in, which turns your network into a fantastic customer engagement channel. At the same time, staff devices connect to a completely separate and secure network using IPSK authentication. This ensures that payment data and operational traffic are always isolated and protected. To get a setup like this right, you absolutely have to start with a professional site survey for your wireless network.
Even with mobile networks getting faster, reliable in-building Wi-Fi is as important as ever. It's interesting to note that while 4G and 5G are more widely available, 5G download speeds have actually dropped in some places. For example, South Korea, a global leader in mobile tech, saw its 5G speeds fall by -4.1 Mbps. This suggests that as more people use the network, the capacity is struggling to keep up, reinforcing the need for robust, on-site Wi-Fi.
So, What's the Game Plan for a High-Performance Network?
You don't need to rip everything out and start from scratch to boost your network's performance. The real secret is making smart, strategic moves that turn your existing components into a powerful, cohesive system.
It all starts with a rock-solid hardware foundation. Think of your access points as the bedrock. Using proven, reliable hardware like Cisco Meraki access points is crucial because they're built to handle the sheer volume of devices and traffic you see in almost any environment today.
Once that foundation is solid, you need to add a layer of intelligent access control. This is where a Splash Access Captive Portal comes in. It’s essentially the front door to your network, creating a smooth and secure sign-on experience for everyone, whether you're juggling a corporate BYOD policy, managing a packed Retail center, or supporting a sprawling campus in the Education sector.
A Quick Sanity Check for Better Wi-Fi
The final piece of the puzzle is bringing your security into the modern era. Let's be honest, shared passwords just don't cut it anymore. Moving away from those outdated pre-shared keys to a more advanced Authentication Solution like EasyPSK is a game-changer. Why? Because you're assigning a unique key to every single user, which completely eliminates the security headaches of shared credentials and gives you pinpoint control over network access.
To see where you stand, run through this quick checklist on your current setup:
- The Foundation: Are you using hardware from a trusted vendor like Cisco or Meraki? Can it actually handle the high-density traffic you expect?
- The Access: Do you have a Captive Portal in place to manage guest Wi-Fi, control bandwidth, and offer a branded, professional experience to users?
- The Security: Have you finally ditched shared passwords for a modern approach like IPSK that provides individual user accountability?
This three-pronged approach is your action plan. Strong hardware, smart access, and modern security—that's how you truly improve the performance of a network.
Frequently Asked Questions
You've got questions, and that's a good thing. It means you're thinking critically about how all these moving parts come together to create a high-performing network. Let's tackle some of the most common ones we hear.
Can a Captive Portal Actually Slow Down My Network?
It's a fair question, but the short answer is no—not if it's implemented correctly. A modern Captive Portal, especially a solution like Splash Access running on powerful Cisco Meraki hardware, has a negligible impact on network speed.
Think of it as a quick ID check at the door. Its job is authentication, which is just a brief, one-time handshake. Once a user is verified, they're on the network. In fact, by keeping unauthorized users from hogging your bandwidth, a captive portal often improves overall performance by making sure resources go to the people who are actually supposed to be there.
Isn't Something Like EasyPSK Difficult to Manage for a Huge University?
It's actually the other way around. Trying to manage a single, shared password for thousands of students and staff in a busy Education or corporate BYOD environment? That’s the real headache.
This is precisely the problem that Authentication Solutions like EasyPSK or IPSK were built to solve. Instead of you manually creating, distributing, and revoking keys, the system automates the entire lifecycle. It makes network access far more secure and infinitely simpler to manage, even with a large, constantly shifting user base.
The key thing to remember is that modern authentication isn't about adding complexity. It's about using smart automation to handle security at scale, which is essential for keeping networks running smoothly in crowded places like schools and retail stores.
Do I Have to Replace All My Hardware to See Better Performance?
Not necessarily. While top-tier equipment from brands like Cisco certainly provides a solid foundation, you can often make significant gains by optimizing what you already have.
Putting intelligent software in place for guest management and authentication is a fantastic starting point. A platform like Splash Access can give you the tools to manage traffic more effectively, strengthen security, and dramatically improve the user experience—all on your existing infrastructure. You'd be surprised what a difference it can make.
Ready to turn your guest Wi-Fi from a frustrating bottleneck into a high-performance asset? Splash Access works hand-in-glove with your Cisco Meraki hardware to deliver secure, reliable, and intelligent network access. Find out how we can help you build a better network at https://www.splashaccess.com.