Hey there! Think of your network as the digital central nervous system of your entire operation. It’s the invisible framework that connects everything and everyone, whether it’s the campus-wide Wi-Fi at a university, the in-store guest experience at a retail chain, or the critical daily operations of a corporate headquarters.
The Digital Foundation of Your Business
Trying to run a modern organization without a solid network is like trying to operate without electricity. It just doesn't work. Networking infrastructure services cover everything from the initial design and setup to the ongoing management of the hardware and software that lets your devices communicate with each other and the outside world.
This isn't just about getting online. It's about building a fast, reliable, and secure digital environment for your employees, guests, and customers. In education, this means students can access online resources without a hiccup. For retail shops, it’s the power behind point-of-sale systems and engaging guest wifi. And in BYOD corporate environments, it ensures staff can connect their personal devices safely and stay productive.
The Shift to Smart, Cloud-Managed Networks
In the past, managing a network meant having a team of IT pros on-site, wrestling with complex hardware. Thankfully, things have changed. Cloud-managed solutions, like those from pioneers such as Cisco Meraki, have completely rewritten the rules.
These modern platforms give you centralized control over your entire network—even if you have dozens of locations—all from a single, easy-to-use web dashboard. This shift has made enterprise-grade networking accessible to businesses of all sizes, eliminating the need for a dedicated IT specialist at every site to manage access points, switches, and security.
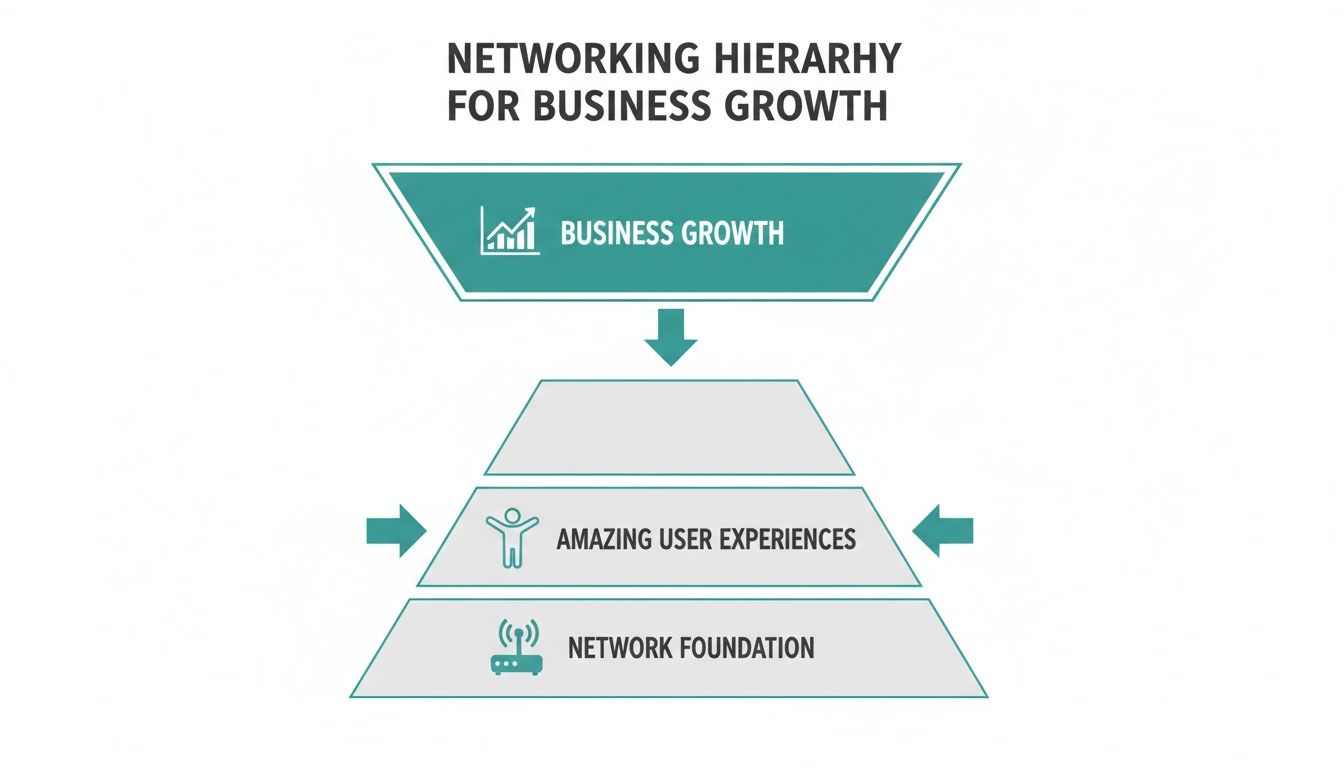
A well-designed network is more than just a utility; it's a strategic asset that unlocks better user experiences and drives business growth. It’s the starting point for creating amazing digital interactions.
It’s About More Than Just a Connection
Today’s networks are built to create intelligent and interactive experiences. This is where features like Captive Portals and advanced Authentication Solutions really shine. You've seen a captive portal—it's that branded login page that pops up when you join a public Wi-Fi network. By adding tools like social login or social wifi, that simple connection becomes a powerful marketing opportunity.
For environments that demand tighter security, methods like IPSK and EasyPSK offer a way to give every user personalized and secure access without the usual IT headaches. These are just a few examples of how the right services can do so much more than connect you to the internet. To see a broader view of how these components come together, explore our guide on modern enterprise networking solutions. A strong foundation is the key to unlocking your business’s full potential.
Building a Powerful and Secure Network Foundation
To really get a handle on networking infrastructure services, you have to look at the individual parts that make the whole system tick. It’s a bit like building a high-performance engine; every component has a critical role, and they all need to work in perfect harmony to deliver the performance, reliability, and security your organization depends on.
The Local Traffic Cops: Switching
At the very core of any local network, you'll find switches. Think of them as incredibly smart traffic directors for a specific building or office. They manage the flow of data between all your connected devices—computers, printers, servers—making sure information gets where it needs to go without creating digital traffic jams.
Connecting to the Outside World: Routing
If switches handle the local neighborhood, routers are the seasoned navigators for the wider world. Their job is to connect your entire local network to the internet, charting the best course for data packets as they travel between different networks. Whether it's an email zipping across the country or a video conference connecting global teams, the router makes sure it takes the most efficient path.
This is why we talk about a network "foundation." It’s the essential first step. Without it, you can't deliver the great user experiences that ultimately lead to business growth.
The takeaway is simple: you can’t achieve big-picture goals like amazing customer satisfaction or increased revenue if the underlying technology is shaky.
And, of course, there's wireless. Wireless Access Points (WAPs) are what create your Wi-Fi network, freeing everyone from the tangle of physical cables. Proper placement of high-quality WAPs, like those from a provider like Cisco, is the key to providing strong, uninterrupted coverage, whether it's across a sprawling university campus or a multi-story office building.
The Power of a Single Pane of Glass
Not long ago, managing all this hardware was a massive chore, often requiring an IT specialist to be on-site to make any changes. This is where cloud-managed networking, especially with platforms like Cisco Meraki, completely rewrites the rulebook.
A cloud-managed network’s biggest advantage is its simplicity. It pulls all your switches, routers, security appliances, and access points into one easy-to-use dashboard you can get to from anywhere.
This shift means you can check the health of your network, push a new security policy, or fix a connection issue at a branch office 500 miles away, all from a web browser. For organizations with many locations, like in education or retail, this is a total game-changer. For a closer look at how these pieces fit together, you can learn more about what makes up the backbone of a network.
Locking Down Your Digital Perimeter
Finally, no network is complete without a serious security strategy. Firewalls are your network's digital gatekeepers, standing guard where your private network meets the public internet. They meticulously inspect all traffic coming in and going out, blocking threats and unauthorized access before they ever have a chance to do damage.
For example, in healthcare, implementing top healthcare data security solutions is non-negotiable for protecting patient data and staying compliant. The same principle applies everywhere—from safeguarding student records on campus to securing credit card information in a retail environment.
When you bring all these elements together—rock-solid hardware, smart cloud management, and robust security—you build a network that isn't just fast, but also resilient and ready for whatever comes next.
Turning Guest Wi-Fi into a Smart Welcome Mat
Think of your Wi-Fi network as more than just an internet connection—it's the first digital handshake you have with your guests. It’s a huge opportunity to make a great first impression. Let's look at how smart authentication and Captive Portals can transform that basic utility into an experience that’s engaging, branded, and full of valuable insights. This is where your networking infrastructure services start to really pay off.
The days of scribbling a long, cryptic password on a whiteboard are over. Modern network platforms, especially tools like Cisco Meraki, make the login process smooth and professional. The moment someone connects, they’re greeted with a custom-branded portal that looks and feels like your organization, whether you're a university, a retail shop, or a corporate headquarters.
This first touchpoint is your chance to set the tone. You can display your terms and conditions, share a special offer, or simply provide a clean, secure gateway to the internet. It transforms a clunky, forgettable process into a professional interaction that reflects well on your brand.
Making Your Network a Marketing Powerhouse
One of the most powerful features of modern guest Wi-Fi is the ability to use social login (also called social Wi-Fi). This lets visitors log in using an existing social media account, like Facebook or Google. For the user, it’s incredibly convenient—no new password to create or remember.
But the real win is for your business. By offering a social login, you can ethically gather valuable, anonymized demographic data. This gives you a much clearer picture of your audience, helping you understand who they are and what they’re interested in. For a retail store, this could mean fine-tuning in-store promotions. For an education campus, it could reveal new insights into student engagement.
A captive portal isn’t just a gatekeeper; it’s a data-gathering tool that turns your Wi-Fi from a cost center into a strategic marketing asset, providing a direct line of communication with your audience.
The demand for these kinds of intelligent networks is exploding. The enterprise network infrastructure market, which is the backbone for sectors like retail and education, was valued at $72.61 billion globally in 2025 and is on track to blow past $115.87 billion by 2034. A huge part of that growth comes from the rising need for sophisticated guest access in corporate offices and shared workspaces. You can dive deeper into these market trends in this report from Precedence Research.
Securing Your Network in a BYOD World
While social logins are great for public-facing guest networks, other situations demand much tighter security. This is especially true in BYOD Corporate offices and across education campuses, where thousands of personal devices connect to the network every single day. Using a single, shared password for everyone is a major security blind spot just waiting to be exploited.
This is where more advanced Authentication Solutions like IPSK (Individual Pre-Shared Key) and EasyPSK make all the difference. They give you the best of both worlds: serious, enterprise-grade security that’s still simple for people to use.
A quick look at these different Wi-Fi authentication solutions shows which business environments they suit best.
Comparing Modern Wi-Fi Authentication Methods
| Authentication Method | How It Works | Best For | Key Benefit |
|---|---|---|---|
| Shared Password (PSK) | One password for everyone. Simple but insecure. | Small offices, home use. | Easy to set up and remember. |
| Social Login | Users connect with their social media accounts. | Retail, Hospitality, Public Venues. | Gathers marketing data and is very user-friendly. |
| IPSK / EasyPSK | Each user or device gets its own unique password. | Corporate BYOD, Education, Student Housing. | High security and granular control; revoke access instantly. |
| 802.1X / RADIUS | Requires credentials (username/password) authenticated by a central server. | Enterprise, Government, Healthcare. | The gold standard for security and network segmentation. |
IPSK and EasyPSK, in particular, solve the age-old IT headache of constantly changing a shared password and patching the security holes it creates.
-
IPSK (Individual Pre-Shared Key): Instead of one password for the entire network, IPSK gives each user or device its own unique key. If an employee leaves or a student loses their laptop, you can kill access for that one key instantly without bothering anyone else. It's a perfect fit for a BYOD Corporate environment.
-
EasyPSK: This takes the same idea and automates it, making it easy to generate and hand out thousands of unique keys. This is a lifesaver for massive deployments like university dorms or student housing, where you need to securely onboard a flood of new devices every semester.
If you're curious about the nuts and bolts, these advanced systems often rely on a core component called a RADIUS server. You can learn more about how to set up a RADIUS server to get a better sense of the technology behind it.
By segmenting access with unique keys, you build a much safer, more manageable network. This kind of fine-grained control, powered by hardware from leaders like Cisco and Meraki, is what separates a basic network from one that's truly smart and secure.
Networking in Action: Real-World Scenarios Across Industries
It's one thing to talk about the theory behind a great network, but where the rubber really meets the road is in its real-world application. Let's look at how networking infrastructure services solve unique, everyday challenges in different sectors.
From a sprawling university campus to a bustling shopping mall, the need for smart, reliable connectivity has never been greater. But a one-size-fits-all approach simply won't work. Each environment has its own rules and expectations, which is why tailored solutions built on robust hardware from leaders like Cisco Meraki are so critical. They provide the flexible foundation needed to create custom-tailored experiences.
The global network infrastructure market has been growing steadily, jumping from $89.925 billion in 2021 to a projected $105.2 billion by the end of 2025. That's a compound annual growth rate (CAGR) of about 4%, fueled by the relentless demand for better connectivity in sectors like hospitality, retail, and education as they modernize their Wi-Fi to handle a tidal wave of data traffic.
Powering the Modern Campus in Education
Picture a university at the start of a new semester. Thousands of students show up, each with a laptop, a smartphone, and a tablet. Getting all those devices connected securely—without a flood of helpdesk tickets—is a huge operational headache. This is the perfect use case for Authentication Solutions like EasyPSK.
Instead of handing out a single, shared password for an entire dorm (a security nightmare and a management mess), EasyPSK automatically generates a unique, personal key for every student. This changes everything.
- Effortless Onboarding: Students connect their own devices through a simple self-service portal. This frees up the IT staff to focus on more important things.
- Tighter Security: With unique keys, each student's traffic is isolated. Their devices can't "see" each other on the network, which dramatically improves security.
- Pinpoint Control: If a student's device is compromised or they violate a policy, IT can revoke their single key instantly without disrupting anyone else.
This approach turns the campus network from a simple utility into a secure, manageable asset that directly improves the student living experience.
Engaging Shoppers in the Retail Sector
For shopping centers and retail stores, the guest network is a goldmine for customer engagement. By setting up a branded Captive Portal with social Wi-Fi features, retailers can transform a simple internet connection into a powerful marketing tool.
When a shopper connects to the guest Wi-Fi, they see a login page offering a social login option. That simple click gives the business valuable, anonymized demographic data, helping them understand foot traffic, peak hours, and customer profiles. They can then use this insight to send targeted promotions or coupons right to a shopper's phone, creating a more personal and compelling visit. To learn more about how this works, take a look at our guide on business Wi-Fi solutions.
A smart retail network doesn’t just provide internet; it creates a direct line of communication with customers, turning anonymous visitors into known patrons and driving sales through personalized engagement.
Securing the BYOD Corporate Environment
In today's corporate world, "Bring Your Own Device" (BYOD) isn't a perk; it's the standard. Employees expect to use their personal laptops, tablets, and phones on the company network. While this is great for productivity, it opens up some serious security holes if it isn't managed correctly.
This is where IPSK (Individual Pre-Shared Key) becomes essential. It’s a similar concept to the education example but built for a corporate setting. IPSK assigns a unique Wi-Fi key to each employee for their approved devices. If someone leaves the company, their access key is simply shut off. No more changing the Wi-Fi password for the entire office and dealing with the chaos that follows.
This method delivers enterprise-grade security with the simplicity of a home network, ensuring company data stays safe while giving employees the flexibility they need. To see how these services apply in other sectors, you can explore the digital transformation in the hospitality industry, where similar principles of secure, seamless access are critical for guest satisfaction. These examples show that the right networking infrastructure is about far more than just technology—it's about creating secure, efficient, and engaging environments for everyone.
Unlocking Business Insights with Network Analytics
Think of your Wi-Fi network as more than just a way to get online. It's a powerful sensor grid, constantly gathering valuable data about how people move and behave in your space. Modern networking infrastructure services give you the tools to tap into this data, turning what was once just technical logs into a goldmine of business intelligence. It’s all about connecting the dots between physical movement and real-world needs.
Pair this with a smart Captive Portal, and suddenly your network starts telling a story. For a retail shop, this means you can see far beyond simple sales figures and start to understand the entire customer journey. You can finally get answers to critical questions: How many people walk past the front door compared to how many actually step inside? Which displays or aisles get the most attention? How long do shoppers stick around?
This kind of information is pure gold for optimizing everything from store layouts and product placement to staffing schedules and marketing campaigns. The analytics you get from advanced platforms, like those built on Cisco Meraki hardware, give you a clear, dashboard-level view of foot traffic, dwell times, and how often customers return.
Turning Wi-Fi Data into Actionable Strategy
But the applications for network analytics go well beyond the world of retail. Just about any organization can use this data to solve unique challenges and make their operations smarter.
-
Education Sector: Imagine a university campus. Analytics can show which libraries, study lounges, or common areas are actually being used. This gives administrators the hard data they need to make better decisions about where to invest resources, adjust operating hours, or plan new facilities that truly meet student needs.
-
BYOD Corporate Offices: In a busy office, understanding how and where the network is being used helps IT teams pinpoint potential bottlenecks before they cause problems. It ensures high-traffic zones always have the bandwidth they need and provides insights that can shape security policies and planning for a smoother work experience.
This represents a fundamental shift. You're no longer just passively providing an internet connection; you're actively gathering the intelligence needed to create better, more responsive environments for your customers, students, or employees.
The Power of Location Analytics
One of the most potent tools in this toolkit is location analytics. By analyzing the Wi-Fi signals from connected devices, your network can generate detailed heat maps of your physical space. These maps show you exactly where people congregate and how they move through your venue over time, offering a deep, real-time understanding of user presence.
By harnessing location analytics, businesses can stop making decisions based on guesswork and start using concrete data to enhance customer experiences, streamline operations, and drive smarter growth.
The right Authentication Solutions are the key to unlocking all this data ethically and effectively. When a user logs onto your network through a social Wi-Fi portal, they provide the necessary consent to gather this anonymized data. It's a win-win: they get quick, easy access, and you get the insights needed to serve them better. To see just how powerful this can be, you can explore the possibilities of location analytics with Splash Access.
Ultimately, these insights help you build a smarter, more responsive business from the ground up.
Finding the Right Partner to Build Your Network
Building a high-performance network isn't a journey you have to take alone. In fact, picking the right partner for your networking infrastructure services is just as important as selecting the right hardware itself. A truly great partner brings deep, hands-on experience with both the physical gear—like access points from Cisco and Meraki—and the specialized software that makes modern, secure user experiences possible.
Think of them as an extension of your own team. They should be there to guide you from the very first blueprint of your network design, through the physical deployment, and stick around for ongoing management and troubleshooting. This collaboration frees you up to focus on what you do best: running your business.
What Makes a Great Service Partner?
When you're vetting potential partners, look for specialists who genuinely understand the headaches and opportunities unique to your industry. A network built for an education campus has completely different security and device onboarding needs than one designed for a bustling retail center or a BYOD corporate office.
A top-tier partner will speak your language. They'll know the ins and outs of deploying solutions like EasyPSK for secure student housing or configuring a Captive Portal with social login to better engage shoppers. They won't just be trying to sell you boxes; their goal is to design a complete system that solves your specific problems.
Your network partner should be a strategic ally who helps you build a scalable, future-proof network. Their goal is to ensure your technology not only works today but is also ready for the challenges of tomorrow.
The right firm will have a proven track record of successfully integrating advanced Authentication Solutions, like using IPSK for seamless employee access or setting up social wifi to gather valuable business insights. They are the essential bridge between powerful hardware and the tangible results your business needs.
Investing in Your Digital Foundation
The scale of modern networking is staggering, and it's only getting bigger. The telecom network infrastructure market, which is the backbone of these services, was valued at $211.10 billion in 2025 and is on track to hit $355.00 billion by 2035. This massive investment, led by giants like Cisco Systems, underscores just how critical expertly managed networks have become, especially in demanding guest wifi environments. You can explore more on this trend in this report on the future of network infrastructure.
Ultimately, finding the right partner is an investment in your own peace of mind. You’re handing over a critical piece of your business to experts who live and breathe this technology every day. This ensures your network becomes a reliable asset that fuels your growth, not a technical headache that holds you back.
Got Questions? Let's Get Them Answered
If you're still weighing your options for networking infrastructure services, you're not alone. Here are some of the most common questions we hear, especially when it comes to guest Wi-Fi, security, and day-to-day management.
What’s the Big Deal with a Captive Portal?
Ever logged into a coffee shop's Wi-Fi and seen a branded login page? That’s a captive portal. It’s the first thing your guests see, making it a critical first impression for any retail store, hotel, or corporate lobby.
But it’s much more than just a welcome screen. A captive portal is your gatekeeper; it requires users to accept your terms of service before hopping online. Better yet, when you integrate it with systems like Cisco Meraki, you can turn it into a powerful marketing tool. By offering easy social login or email sign-up options, you provide a smooth connection for guests while gathering valuable insights to grow your business.
How Exactly Does IPSK Make BYOD Safer?
Let's talk about securing a network where everyone brings their own device (BYOD Corporate). The old way was to use a single password for everyone—a huge security headache when someone leaves the company.
IPSK, which stands for Individual Pre-Shared Key, fixes this. Instead of one password for the whole network, each person gets their very own unique key.
Think of it like a hotel room key. If a guest checks out or loses their key, you just deactivate that single key without having to re-key the entire hotel. If an employee leaves or a device is lost, you can instantly revoke their access without disrupting anyone else. It brings serious, enterprise-grade security to your network but keeps things simple for everyone. It's a game-changer for corporate offices and education campuses.
Is Managing a Network Across Multiple Locations a Nightmare?
Not anymore. This is where cloud-managed networking truly shines. With a platform like Cisco Meraki, your entire network—no matter how many locations you have—is managed from a single, intuitive dashboard.
From one screen, you can see everything. Need to update security policies for all your retail stores? Done. Want to check bandwidth usage at the corporate headquarters? Easy. You can monitor, configure, and troubleshoot your entire infrastructure without ever needing to send an IT person on-site. It’s a massive time and money saver.
Ready to upgrade your guest Wi-Fi and lock down your network? Splash Access gives you the tools you need, designed to work perfectly with Cisco Meraki. See what you can build at https://www.splashaccess.com.