Hey there! Let's talk about your business's digital immune system. We're talking about your network security infrastructure. It’s not just one tool or a single firewall—it’s a complete strategy that brings together hardware, software, and smart policies to defend all your important data. Think of it as the entire framework that keeps threats out while making sure the right people have access to the right things.
Building Your Digital Fortress
A solid network security infrastructure is the absolute bedrock of your digital operation. It's the silent guardian working 24/7 to protect sensitive information, keep your business running smoothly, and maintain the trust you've built with customers and employees. Without it, you're practically leaving the front door wide open to data breaches, financial loss, and some serious damage to your reputation.
This has never been more critical than it is right now. Every industry is facing its own unique security puzzle:
- Education: A university campus has to securely manage Wi-Fi for thousands of students, faculty, and guests, all connecting with their own personal devices.
- Retail: A store needs to offer easy-breezy guest Wi-Fi for shoppers while keeping its critical point-of-sale and inventory systems completely walled off.
- Corporate BYOD: An office has to juggle the convenience of employees using their own devices (Bring Your Own Device) with the non-negotiable need to protect company secrets.
The Modern Approach to Network Defense
To tackle these challenges, security has evolved way beyond basic passwords and firewalls. Today's best practices rely on a layered defense, often starting with a powerful and reliable hardware foundation from providers like Cisco and Meraki. This gear serves as the tough, dependable backbone of your network.
But great hardware is only half the story. Smart authentication solutions are the intelligent gatekeepers. Technologies like Captive Portals have transformed into sophisticated access control tools. Meanwhile, methods like IPSK (Identity Pre-Shared Key) and its more user-friendly cousin, EasyPSK, give a unique, secure key to every single user or device. This kind of granular control is crucial for wrangling the sheer number of devices on any modern network.
This "never trust, always verify" philosophy is the core of a modern strategy. You can dive deeper into how this works in our detailed guide on Zero Trust security.
A strong network security infrastructure isn't just about stopping attacks; it's about enabling your business. It fosters a safe environment where you can innovate, collaborate, and grow, confident that your digital assets are protected.
The numbers tell the story. The global network security market is on track to soar past USD 70 billion by 2032. This explosive growth is fueled by the very challenges we're discussing—the shift to remote work, cloud adoption, and the explosion of connected devices. This isn't just an IT line item; it's a core business investment.
The Building Blocks of a Secure Network
A solid network security infrastructure isn't about buying one magic box. It's a system of layered defenses, much like a medieval castle. A castle doesn't rely on a single tall wall; it has a moat, outer walls, inner walls, watchtowers, and guards at every gate. Each layer offers a different kind of protection, and when they work together, the defense is incredibly strong.
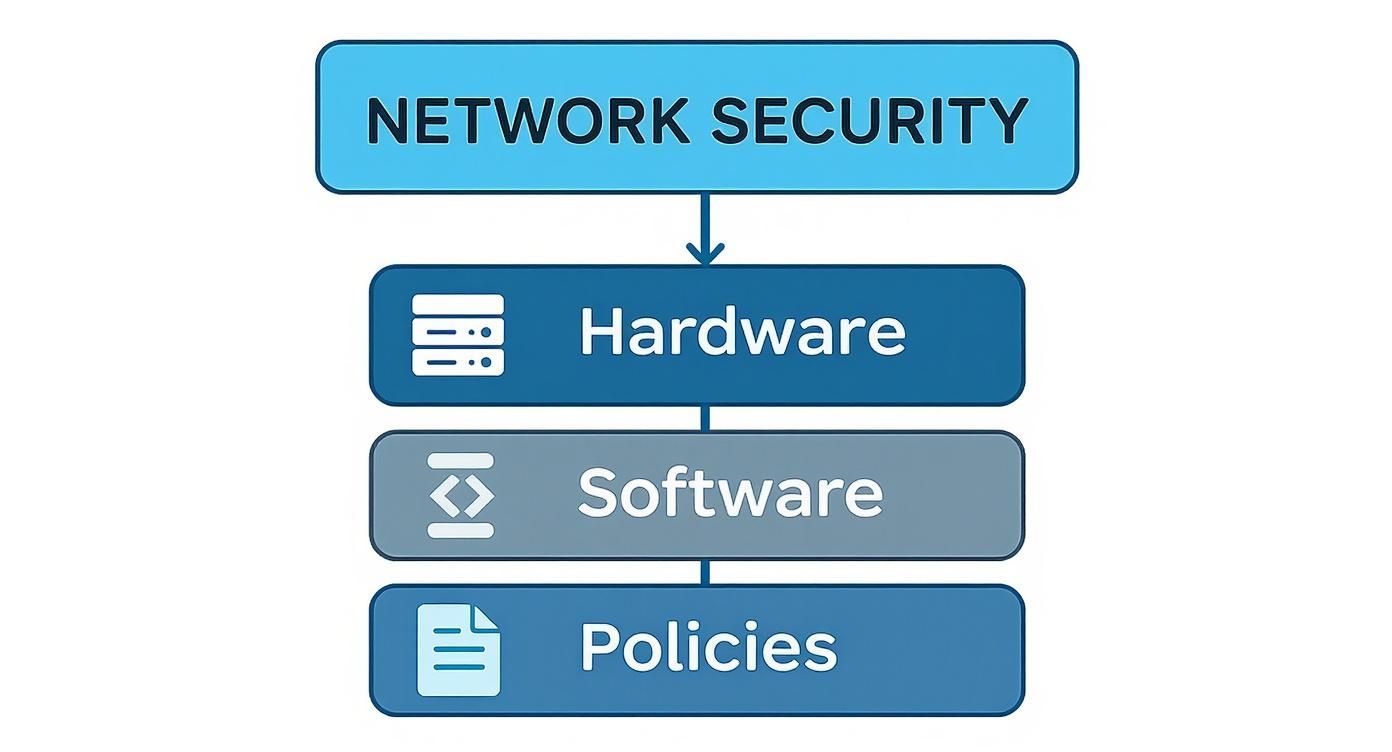
In our digital world, these layers are built from specialized hardware and software working in concert. These are the core components that every secure network, big or small, depends on to shield its data and users from constant threats.
This diagram shows how a secure network is built on a foundation of hardware, software, and well-defined policies.
As you can see, security isn't just about technology. It's a strategic mix where physical devices, smart programs, and human-led rules create a complete defense system.
Firewalls: The Digital Gatekeepers
Your first and most famous line of defense is the firewall. Picture it as the main gate of that castle. It stands between your trusted internal network and the wild, untrusted internet. A firewall's entire job is to inspect all traffic coming in and going out, making instant decisions about what to allow and what to block based on a strict set of security rules.
Modern hardware, like the powerful access points from Cisco Meraki, often has sophisticated firewall features built right in. This is a huge plus because it simplifies management and ensures your first defense is both strong and easy to configure.
VPNs: Your Secret Tunnels
A Virtual Private Network (VPN) is like a secret, encrypted tunnel for your data. When an employee connects from their home office or a local coffee shop, the VPN scrambles all the information they send and receive. This makes it completely unreadable to anyone trying to eavesdrop on the public network.
This is absolutely crucial with remote work being so common. A VPN extends the security of your corporate office to wherever your team is, keeping sensitive conversations and data private.
Intrusion Detection and Prevention Systems: The Watchful Guards
If firewalls are the castle walls, then Intrusion Detection and Prevention Systems (IDS/IPS) are the guards walking the ramparts. An IDS monitors network traffic for any suspicious activity or policy violations. When it spots something shady, it sounds the alarm.
An IPS takes it a step further. It doesn't just detect a potential threat—it actively steps in to block it. This proactive defense is critical for stopping attacks dead in their tracks before they can do any real damage.
Network Segmentation: Containing the Damage
One of the smartest strategies in network security is network segmentation. Think of a ship's hull, which is divided into multiple watertight compartments. If one compartment springs a leak and floods, the bulkheads keep the water contained, preventing the entire ship from sinking. Network segmentation does the exact same thing for your digital infrastructure.
By carving your network into smaller, isolated sub-networks, you can contain a security breach to a single area. This strategy is essential for protecting your most valuable assets.
A great example is a retail store. Segmentation keeps the public guest Wi-Fi completely separate from the network running the payment terminals. Or in a university, it can isolate student traffic from the sensitive administrative network. This principle is so important that we've put together a full guide on network segmentation best practices to help you implement it correctly.
Together, these building blocks form the core of any strong network security infrastructure, providing the layered defense needed to protect against a wide range of modern threats.
Controlling Access with Smart Authentication
Knowing who and what is on your network is the bedrock of any solid network security infrastructure. You've built your digital fortress with firewalls and segmentation, but the next critical layer is controlling every single entry point. This is where smart authentication solutions step in, acting as intelligent gatekeepers that verify the identity of every user and device trying to connect.
This process is especially vital in busy environments where countless devices come and go. Think about the unique challenges different places face:
- Education: University campuses have to securely manage thousands of students, faculty, and staff, all connecting with their own laptops, phones, and tablets.
- Retail: Stores need to give shoppers easy-to-use guest Wi-Fi while making sure that customer traffic never touches the secure network used for payment processing.
- Corporate BYOD: Businesses must accommodate employees using their own devices (Bring Your Own Device) without putting sensitive company data at risk.
In each of these situations, a single, one-size-fits-all password just won’t do. You need a much smarter, more granular way to handle access.
The Evolution of Captive Portals
The first line of defense for Wi-Fi access is often the Captive Portal. You’ve definitely seen one before—it’s that login page that pops up when you try to connect to Wi-Fi at a hotel, airport, or coffee shop. For years, these were pretty basic pages, but they've since evolved into powerful security and engagement tools.
Modern Captive Portals, especially when they're part of a robust network like one built on Cisco Meraki hardware, do a lot more than just grant access. They can enforce your terms of service, making sure every user agrees to your acceptable use policy before they get online. That simple step is a massive part of your security and legal compliance strategy.
Moving Beyond the Shared Password
The single biggest weakness in traditional Wi-Fi security is the shared password. You know the one—it's written on a whiteboard in the conference room or printed on a cafe's menu. Once it's out in the open, it's impossible to control, creating a giant security hole.
The old model of a single, shared Wi-Fi password is fundamentally broken. A modern authentication strategy demands that every user and device has a unique, revocable identity.
This is where advanced technologies like IPSK (Identity Pre-Shared Key) and EasyPSK completely change the game. Instead of one password for everybody, these systems generate a unique, secure key for every single user or device.
This approach brings some huge benefits:
- Granular Control: If an employee leaves or a device is lost, you can instantly revoke its specific key without disrupting anyone else on the network.
- Enhanced Security: With unique keys, you can trace activity back to a specific user or device, which is impossible with a shared password.
- Simplified User Experience: Onboarding is a breeze. In a corporate BYOD environment, an employee can self-register their devices and receive their own personal key, making access both simple and secure.
This level of individual control is a cornerstone of a strong network security infrastructure. It gives you the visibility and management needed for high-density places like a university campus or a bustling corporate office. For an even deeper layer of security, organizations can implement additional checks. You can learn more by exploring our guide on what multi-factor authentication is and how it strengthens access controls.
To push access control and authentication even further, consider the ongoing rise of biometric technology in cybersecurity, which adds another powerful layer of identity verification to protect your most sensitive resources. By combining these smart authentication methods, you ensure that only authorized people and trusted devices can ever get onto your network.
Adapting Security for Different Environments
There’s no such thing as a one-size-fits-all network security infrastructure. Think about it: an open university campus, a bustling retail chain, and a modern corporate office each present a completely unique set of security puzzles. The right approach always depends on the specific environment, who the users are, and what data you’re trying to protect.
Let's dig into how to apply these security principles in the real world.
We'll look at how combining powerful Cisco Meraki hardware with flexible authentication solutions like Captive Portals and IPSK creates the perfect security recipe for different sectors.
Securing the Education Sector
University and school campuses are some of the most challenging networks to secure. You're dealing with thousands of students, faculty, and visitors all trying to connect with a massive variety of personal devices. A single, shared Wi-Fi password would be an absolute security nightmare.
This is where a layered approach really shines. A Captive Portal can act as the front door, making sure every user agrees to the institution's acceptable use policy. But the real magic for taming all those devices comes from solutions like IPSK and EasyPSK.
- Individual Accountability: Each student gets a unique key for their devices. If a laptop is lost or a student misuses the network, IT can revoke that single key without disrupting anyone else.
- Simplified Onboarding: Students can self-register their devices through a simple portal. The process is smooth for them but still gives IT tight security control.
- Network Segmentation: Most importantly, student traffic is kept completely separate from the administrative network that houses sensitive records and financial data.
This strategy builds a secure, manageable, and user-friendly environment. For a deeper dive, check out our guide on creating secure Wi-Fi access for education.
Protecting the Retail Environment
In retail, you’re playing a double game. You need to provide a fantastic, seamless guest Wi-Fi experience for shoppers while completely locking down the business-critical network. Things like point-of-sale (POS) systems, inventory databases, and employee communications have to be untouchable by public traffic.
The biggest mistake a retailer can make is putting guest Wi-Fi and POS systems on the same network. A strong security infrastructure makes this separation airtight, protecting customer payment data and ensuring PCI compliance.
A Cisco Meraki powered network makes this separation straightforward. A well-designed Captive Portal not only grants secure internet access but also doubles as a valuable marketing tool for engaging customers. Behind the scenes, strong network segmentation acts as an impenetrable wall between the public and private sides of the business.
Tackling the Corporate BYOD Challenge
The "Bring Your Own Device" (BYOD) trend isn't going anywhere. Employees love the convenience of using their personal phones and laptops for work, but this creates a massive security headache for IT departments. How do you give them the access they need without putting sensitive corporate data at risk?
Once again, the answer is smart, individual authentication. An EasyPSK system is a perfect fit for a BYOD corporate environment because it balances employee convenience with the strong security the business demands.
- An employee is issued a unique key just for their personal devices.
- This access is tied directly to their corporate identity, ensuring only active employees can connect.
- If an employee leaves the company, their access is instantly and automatically revoked across all their devices.
This method provides the granular control needed to embrace BYOD safely. It helps build a network security infrastructure that is both flexible and formidable, protecting the company's digital assets without frustrating the team. This move towards flexible, cloud-managed solutions reflects a major market shift—the adoption of cloud-based network security is now the dominant trend, driven by hybrid work and the need for scalable protection.
Maintaining Your Security Posture Over Time
Getting your network security infrastructure up and running is a great start, but the work doesn't stop there. True security isn't a "set it and forget it" project. It’s a continuous cycle of vigilance, adaptation, and improvement. Your digital defenses need constant care to stand up against threats that are always evolving.
Think of it like owning a high-performance car. You wouldn't just buy it and drive for years without changing the oil or checking the tires, right? Your network demands that same level of commitment. This ongoing effort is what turns a solid initial setup into a resilient, long-term security posture.
The Non-Negotiable Task of Patching and Updates
One of the most fundamental routines for maintaining security is keeping everything patched and updated. Cybercriminals are always on the lookout for known vulnerabilities in outdated software, firmware, and operating systems. Every unpatched hole is essentially an unlocked door in your digital fortress.
Thankfully, providers like Cisco Meraki simplify this by pushing security updates and patches automatically from the cloud. This ensures your hardware is always running the latest, most secure firmware without your IT team having to chase down every single device.
A proactive patching schedule is one of the single most effective things you can do to shrink your attack surface. The vast majority of successful cyberattacks exploit vulnerabilities for which a patch was already available.
This proactive approach is essential for any organization, from an Education campus managing thousands of student devices to a Retail chain handling sensitive customer data.
Your People: The Strongest Asset or Weakest Link
All the best technology in the world can't protect you if your people aren't on board. Your employees are on the front lines every day, and their awareness can be either your strongest shield or your biggest vulnerability. This is why ongoing employee training isn't just a nice-to-have—it's absolutely essential.
Regular training sessions should hammer home key topics like:
- Phishing Awareness: Phishing is still a top method for initiating attacks, so teaching staff how to spot and report suspicious emails is critical.
- Password Hygiene: Consistently reinforce the need for strong, unique passwords and the power of multi-factor authentication.
- Secure Wi-Fi Usage: Make sure they understand the risks of connecting to unsecured public networks, especially in a corporate BYOD environment.
A well-informed team acts as a human firewall, adding a powerful, intuitive layer of defense that technology alone can't provide. And to truly protect the business, your security posture must also cover the entire lifecycle of your equipment, which includes having a robust IT Asset Disposition (ITAD) strategy for when technology reaches its end of life.
Audits and Incident Response Planning
You can't protect what you don't monitor. Regular security audits and proactive monitoring are the equivalent of a health check-up for your network, helping you spot weaknesses before an attacker does. For a deeper dive, you can explore key strategies in our guide on network monitoring best practices.
This is becoming more important as global trends in security spending shift. While North America still leads, the fastest growth is now in emerging markets across Asia and Latin America. In fact, Southeast Asia's network security market is projected to grow at a CAGR of 10.8%. This rapid expansion highlights a global need for stronger security practices everywhere.
Finally, you must have a clear incident response plan. When a threat does slip through, your team needs a playbook. They need to know exactly who to contact, what steps to take, and how to contain the damage immediately. A well-rehearsed plan can mean the difference between a minor hiccup and a full-blown crisis.
Why a Strong Network Is Your Best Business Asset
We've walked through the nuts and bolts—the components and strategies—but let's bring it all back to the most important point. Investing in a robust network security infrastructure isn't just another line item on the IT budget. It's one of the smartest business decisions you can make, directly fueling your growth, resilience, and the trust your customers have in you.
Think of it this way: your network is the invisible foundation supporting everything you do. Every transaction, every video call, every piece of data shared—it all rides on that foundation.
Whether it’s a student submitting their coursework in an Education environment or a shopper hopping on the guest Wi-Fi in a Retail store, security is non-negotiable. A breach isn’t just about stolen data; it’s about shattered trust, and that’s a currency you can’t easily earn back.
It's About More Than Just Protection
A powerful network, especially one built on reliable Cisco and Meraki hardware, does far more than just keep the bad guys out. It actively enables your business to do more. When you layer on smart authentication solutions, you transform a simple internet connection into a secure, managed, and valuable experience.
For instance, by using tools like Captive Portals with IPSK or EasyPSK, you can:
- Empower Your Team: Securely roll out BYOD policies in your office, giving employees the flexibility they crave without putting company data at risk.
- Build Customer Confidence: Offer seamless, safe guest Wi-Fi that shows customers you take their digital safety seriously from the moment they connect.
- Guarantee Business Continuity: Sidestep the kinds of disruptive attacks that can grind operations to a halt, protecting both your revenue and your hard-won reputation.
In the end, a secure network is a powerful competitive advantage. It's the silent asset that tells customers and partners that you're a trustworthy, professional, and forward-thinking organization.
This kind of strategic investment lets you keep your focus where it belongs: on your core mission. You can move forward with confidence, knowing your digital backbone is strong enough to carry your ambitions. It truly is the bedrock of modern business.
Frequently Asked Questions
Got questions about building a solid network security infrastructure? We've got answers. Here are a few common queries we hear about getting started, handling different users, and how modern authentication fits into the puzzle.
What's the Very First Thing I Should Do to Improve Our Network Security?
The best place to start is always with visibility. It's an old saying, but it's true: you can't protect what you can't see. You need a clear picture of every single device connecting to your network and who's behind it.
Putting a robust authentication solution in place is a fantastic first move. For Wi-Fi, a Captive Portal paired with IPSK or EasyPSK gives you immediate control over network access. Think of it as the foundation of your security house, especially if you're running on a Cisco Meraki network. Once that's solid, you can start layering on other essentials like firewalls and segmentation.
How Can We Secure a BYOD Network Without Annoying Our Employees?
The secret to a successful BYOD (Bring Your Own Device) policy is hitting that perfect balance between airtight security and a smooth user experience. This is where tools like IPSK and EasyPSK really shine in a corporate setting.
Instead of passing around a clunky, shared password—which is a massive security hole—each employee gets their own unique key for their personal devices. It’s incredibly simple on their end, but it gives the organization powerful, device-level security on the back end. This way, you get all the flexibility of BYOD without putting your company's sensitive data at risk.
A seamless onboarding process is just as important as the security behind it. When employees can connect their devices with minimal friction, they are far more likely to embrace security policies rather than try to work around them.
Is a Basic Captive Portal Good Enough for Guest Wi-Fi in My Retail Store?
A basic Captive Portal is a decent start, but a modern one can do so much more. In the Retail world, a well-designed portal is both a security gate and a powerful customer engagement tool. On the security front, it enforces your terms and conditions and—most importantly—keeps all guest traffic completely isolated from your critical business network, like your point-of-sale systems.
This total separation means your customers get the easy Wi-Fi they want, while your sensitive business data stays safely walled off. It's an absolutely essential layer in any retail network security infrastructure.
Ready to lock down your network and give users a seamless Wi-Fi experience? Splash Access offers powerful authentication tools, including advanced Captive Portals and EasyPSK, built to integrate perfectly with your Cisco Meraki gear. Find out more and get started today.