Ever wondered how a sprawling university campus, a busy shopping mall, or a massive corporate office manages to deliver flawless, secure Wi-Fi to thousands of people at once? Hey, it’s a great question! The secret isn't just powerful hardware; it's a professional network design service. Think of it as the architectural blueprint for your entire digital environment, and we're here to make it friendly and easy to understand.
What Is A Network Design Service Anyway?
A network design service is the strategic planning phase for your digital infrastructure. Instead of sketching out rooms and hallways, network architects map out data flow, device capacity, and security protocols. A truly great design moves far beyond simply providing an internet signal; it builds an intelligent, scalable, and resilient network that actively supports your business goals. It’s all about making your tech work for you, not the other way around.

This process involves meticulously selecting and configuring the right hardware, like high-performance access points from industry leaders like Cisco and Cisco Meraki, and pairing it with sophisticated software to manage how users get online. The end goal is a seamless experience, whether you're in the Education, Retail, or BYOD Corporate sector.
Core Elements Of A Modern Network Design
A comprehensive network design goes deep into several critical areas to ensure your Wi-Fi is more than just a utility. It becomes a powerful tool for security, marketing, and operations.
| Component | Why It Matters To You | Real-World Example |
|---|---|---|
| Wireless Site Surveys | Ensures zero dead zones and optimal performance by physically mapping out signal strength and interference. | An engineer walking through your hotel with specialized tools to find the perfect placement for each Cisco Meraki access point, guaranteeing great Wi-Fi in every guest room. |
| Capacity Planning | Prevents network slowdowns by calculating the number of users and devices your Wi-Fi can handle simultaneously. | A stadium needs a network designed for 50,000 fans all trying to post to social media at the same time during a concert. |
| Security & Authentication | Protects your internal data by creating separate, secure access for guests, employees, and corporate-owned devices. | Using unique, individual passwords (IPSK or EasyPSK) for each employee's personal phone and laptop in a BYOD environment, keeping them off the main corporate network. |
| Captive Portals | Creates a branded, professional login experience for guests while allowing you to present terms of service or promotional offers. | The familiar login page you see at an airport or coffee shop before you can access their free guest wifi. |
| Analytics & Reporting | Gathers valuable, anonymous data about visitor foot traffic, dwell times, and peak hours to inform business decisions. | A retail chain uses Wi-Fi analytics to see which departments are most popular and adjusts store layouts or staffing accordingly. |
By planning for each of these components, a network design service creates an infrastructure that's built for your specific needs today and ready for what's coming tomorrow.
More Than Just An Internet Connection
The real value of a professional design is its ability to solve specific business problems. A retail store, for instance, might want to offer engaging guest Wi-Fi with social login options. This not only gives shoppers a convenient perk but also turns their connection into a powerful marketing opportunity with social wifi.
Likewise, a corporate office has to provide secure access for visitors and personal employee devices (BYOD) without ever compromising the sensitive internal network. This is exactly where advanced authentication solutions prove their worth.
A well-designed network anticipates your needs. It securely isolates guest traffic from internal data, prioritizes critical applications, and provides a stable connection for everyone, everywhere on your premises.
Security is non-negotiable in any modern network design. Simple shared passwords just don't cut it anymore. Today, we implement advanced methods like IPSK (Individual Pre-Shared Key) and EasyPSK, which assigns a unique, private key to each user or device. This is an absolute game-changer for securely managing BYOD environments in the corporate and education sectors.
When combined with custom Captive Portals, these authentication methods create a secure and branded front door to your network. This level of planning is becoming essential as connectivity demands explode. The global Wi-Fi market was valued at USD 22.06 billion in 2024 and is projected to hit USD 45.12 billion by 2029, with the services component growing rapidly. You can discover more insights about this growing market and see why expert design is so critical.
Ultimately, a network design service transforms your Wi-Fi from a simple utility into a strategic asset that strengthens security, engages users, and drives real business success.
Building Your Foundation With a Wireless Site Survey
Before a single access point is mounted, the most critical step in any professional network design service is getting to know your physical space. This is precisely what a wireless site survey accomplishes.
Think about it like this: you wouldn't try to light a sprawling warehouse by just guessing where to hang the lightbulbs. You’d inevitably end up with glaring bright spots and frustrating, shadowy corners. A site survey does the same thing, but for Wi-Fi signals.
Using specialized software and tools, engineers physically map your location to see how radio frequency (RF) signals behave in your specific environment. They hunt down sources of signal interference—things like concrete walls, metal shelving, or even electronic "noise" from machinery. This meticulous process ensures every Cisco Meraki access point is placed in the perfect spot for wall-to-wall, reliable coverage.
This isn’t just about stamping out dead zones. It’s about building a robust network that can handle the intense demands of modern Education, Retail, and BYOD Corporate sectors.
Why a Survey Is Non-Negotiable
A "one-size-fits-all" approach to Wi-Fi is a recipe for dropped connections, slow speeds, and frustrated users. A thorough survey is the bedrock of a high-performing network, making sure your investment actually delivers the performance your organization needs to thrive.
It’s the essential first step that allows advanced features like seamless Captive Portals and secure authentication solutions to work without a hitch.
A professional site survey transforms guesswork into a precise science. It’s the difference between a network that merely works and one that excels—providing the reliable connectivity needed for everything from student learning to retail transactions.
This foundational work is also crucial for implementing more advanced security protocols later. For instance, if you plan to use IPSK or EasyPSK to securely manage hundreds of personal devices, you first need to guarantee the underlying signal strength and coverage are flawless. A weak signal can disrupt these secure connections, undermining your entire security strategy.
Types of Wireless Surveys
Not all surveys are created equal. A professional service will recommend the right approach for your needs, as each type serves a distinct purpose in the network design process.
- Predictive Survey: This is a virtual survey where engineers use your building’s floor plans and specialized software to model Wi-Fi coverage. It’s a fantastic starting point for new construction projects or for initial budget planning.
- Passive Survey: An engineer walks the site and "listens" to all existing Wi-Fi signals in the area. This helps identify interference coming from neighboring networks and other environmental factors that could cause problems.
- Active Survey: This is the most comprehensive type. Here, an engineer connects a device to your actual access points and measures real-world performance metrics like throughput, latency, and packet loss.
By combining these methods, a network designer gets a complete, multi-layered picture of your environment. This is what ensures that when your staff, students, or customers connect to your guest WiFi using social login, their experience is fast and seamless from the very first click. A solid foundation makes everything else possible.
You can dive deeper into the specifics of how we conduct a professional site survey for a wireless network to see the detailed work involved.
Your Digital Front Door: Making an Impression with Captive Portals
Whenever a guest connects to your network, their first real interaction isn't with your staff or your products—it's with that login screen. We call this a captive portal, but it's a mistake to think of it as just a password field. A well-designed captive portal is your digital welcome mat. It’s your first chance to make a great impression and a powerful tool for branding and security.
This is a cornerstone of any modern network design service. We move beyond generic login pages to create a branded, seamless experience, often built on reliable hardware like Cisco Meraki. The idea is simple: make connecting easy for the user and incredibly valuable for the business.
This isn't just a niche feature anymore. The global Guest Wi-Fi Platform market was valued at around $2.5 billion in 2025 and is on track to explode to $7.6 billion by 2033. This surge shows just how critical secure, user-friendly connectivity has become for hotels, retail centers, and campuses everywhere. They're turning a basic utility into a direct business asset. You can read the full research on this growing market to see where things are headed.
Authentication That Fits the Scene
Not all users are the same, so why should their login methods be? The right authentication solutions are all about balancing convenience with security, and that balance changes depending on the environment. This is where a strategic network design really proves its worth.
In a Retail setting, for example, the main goals are engagement and understanding your customers. This makes it the perfect place for Social WiFi.
- Social Login: Guests can hop on the network using their existing social media accounts, like Facebook or Google.
- The Payoff: It's incredibly easy for shoppers, and in return, the business gets valuable, anonymized demographic data to better understand who is visiting.
- Branding Power: The login page itself can be a mini-billboard, showcasing promotions, new products, or loyalty program sign-ups.
Suddenly, your guest wifi isn't just a cost center—it's a marketing machine.
A captive portal isn't just a gate; it's a conversation starter. It’s your chance to welcome guests, reinforce your brand, and provide a secure, tailored connection that meets their specific needs.
But for Education or corporate BYOD (Bring Your Own Device) environments, the focus shifts almost entirely to security and control. A shared password scribbled on a whiteboard is a huge security hole, making it impossible to know who’s doing what on your network.
The Power of Individual Keys with IPSK
This is where more advanced methods like IPSK (Individual Pre-Shared Key) and EasyPSK come into play. Instead of one password for everyone, IPSK technology assigns a unique, private key to each individual user or device.
This is a complete game-changer for a few key reasons:
- Accountability: If a device is causing trouble or acting suspiciously, IT can pinpoint it instantly and revoke its specific key without affecting anyone else.
- Containment: If a key is compromised, the breach is limited to a single user, not the entire network. This massively shrinks the potential fallout from a security incident.
- Easy BYOD Management: Giving new employees or students their own secure key makes onboarding their personal devices a safe, repeatable process. Their access is tied directly to them.
This kind of granular control is absolutely essential for any organization that needs to protect sensitive data while offering the flexibility of BYOD. By weaving together the right authentication solutions, a skilled network design service ensures every user gets the appropriate level of access, making the network both easy to use and locked down tight. You can learn more about how to design a powerful WiFi captive portal that can adapt to these different needs.
How Network Design Changes for Your Industry
A network built for a sprawling university campus has a completely different job to do than one designed for a boutique retail store or a secure corporate headquarters. A seasoned network design service understands these unique challenges and builds a network that does more than just provide internet—it solves real operational problems.
The right design turns your Wi-Fi from a simple utility into a strategic business asset. It's all about creating a digital environment that perfectly matches your goals, whether that's engaging shoppers, empowering students, or locking down corporate data.
Secure and Scalable Networks for Education
In Education, the network is the absolute backbone of modern learning. The biggest challenge here is density. Picture hundreds, even thousands, of students trying to connect their laptops, tablets, and phones all at once in lecture halls and libraries.
Any network design for a school or university has to be engineered for this high-density reality. This involves strategically placing Cisco Meraki access points to handle the immense load and kill those frustrating slowdowns during peak class times. But capacity is only half the battle; security is non-negotiable.
With so many Bring Your Own Device (BYOD) connections, a single shared password becomes a massive security hole. This is where more advanced authentication solutions are essential.
- IPSK and EasyPSK: These tools give each student and faculty member a unique, private key for their devices. This ties network access to an individual, making it far simpler to manage and secure thousands of personal devices.
- Content Filtering: The design must include robust content filtering to maintain a safe and appropriate online environment for students.
- Seamless Onboarding: The Captive Portals used for onboarding have to be dead simple for thousands of new users to navigate at the start of a semester.
Engaging Customers in the Retail World
For Retail businesses, the network’s role shifts from a basic utility to a powerful marketing and analytics engine. The main goal is to improve the customer's journey from the second they walk through the door, and it all starts with offering an incredible guest Wi-Fi experience.
A clunky, frustrating login process is a huge turn-off for shoppers. That’s why social login options are a game-changer. By letting customers connect using their social media accounts, retailers provide instant, hassle-free access. This social Wi-Fi approach not only makes customers happy but also provides valuable, anonymized demographic data.
For retailers, the guest network is no longer just about offering free internet. It’s a direct channel for communication, a source of rich customer analytics, and a tool to drive sales and loyalty.
Beyond just getting online, a retail network design focuses on:
- Location Analytics: Using Wi-Fi signals to understand foot traffic patterns, see which areas are most popular, and measure how long shoppers stay in certain departments.
- Branded Captive Portals: Turning the login page into a digital billboard to announce sales, promote new products, or get people to sign up for a loyalty program.
- Secure Payment Processing: Making sure all point-of-sale systems and staff devices operate on a completely separate and secure network, walled off from the public guest Wi-Fi.
Protecting Data in the BYOD Corporate Sector
In the corporate world, the number one priority for any network design service is iron-clad security. Employees expect to connect their personal devices (BYOD), and visitors need reliable guest access, but the internal corporate network must remain completely locked down and untouchable.
This is done through meticulous network segmentation. A smart design creates multiple, isolated networks that run independently of each other. The employee BYOD network, the guest network, and the secure corporate network never cross paths, eliminating the risk of a guest or a compromised personal device accessing sensitive company data.
Seamless integration with existing IT infrastructure is also key. Modern authentication solutions can link up with identity providers like Azure AD, ensuring user access is managed through a single, secure platform. By providing tailored business Wi-Fi solutions, companies can offer the convenience of connectivity without ever compromising on security.
Network Design Priorities Across Different Sectors
While connectivity is the common thread, the why and how of network design vary dramatically from one industry to another. The table below breaks down the primary goals and key technologies for a few key sectors, showing how the focus shifts based on business needs.
| Sector | Primary Goal | Key Technology Focus | Business Outcome |
|---|---|---|---|
| Education | High-density performance & student safety | IPSK/EasyPSK, Content Filtering, Access Point Placement | Uninterrupted learning, secure BYOD, safe online environment |
| Retail | Customer engagement & business intelligence | Social Wi-Fi, Location Analytics, Branded Portals | Increased foot traffic, higher sales, customer loyalty |
| Corporate | Data security & operational efficiency | Network Segmentation, IPSK/EasyPSK, BYOD Policies | Data breach prevention, streamlined access, employee productivity |
As you can see, a successful network is never a one-size-fits-all solution. It's about deeply understanding the core mission of the organization and building the digital infrastructure to support it directly.
Turning Your WiFi Into A Business Intelligence Engine
Your WiFi network is capable of so much more than just providing an internet connection. When designed correctly, it becomes a goldmine of data, giving you a deep understanding of how people move through and interact with your physical space. It’s no longer just a utility; it’s a powerful business intelligence tool.
When you bake analytics into your Cisco Meraki infrastructure from day one, your network starts telling a story. The access points can anonymously detect any WiFi-enabled device nearby, letting you see exactly how people move and behave inside your venue.
From Connectivity To Customer Insights
Picture a retail manager pulling up a heatmap of their store. In an instant, they can see which displays are magnets for attention and track exactly how long shoppers linger in specific aisles. This isn't some far-off concept; it's what a well-designed network delivers today. That same technology can help a university facilities manager see real-time student footfall, making it easy to optimize campus resources and ensure spaces are being used effectively.
This shift from just providing a connection to creating an intelligent environment is fueling incredible growth. The Wi-Fi analytics market is already a giant, valued at USD 8.13 billion in 2024, and it's expected to explode to USD 40.96 billion by 2032. This tells you just how hungry sectors like Retail and hospitality are for data-driven insights that give them an edge. You can discover more insights about Wi-Fi analytics market trends and see why this is happening.
By building analytics into your network design from the start, you move from simply offering a connection to creating an intelligent environment that helps you understand your users on a whole new level.
Making Smarter Decisions With Data
The data you collect is invaluable for making smarter decisions about everything from marketing and operations to staffing. Once you start to understand user behavior, you unlock some serious advantages.
- In Retail: Pinpoint your busiest hours to get staffing just right, test new store layouts to see what works, and actually measure how your marketing campaigns drive people into the store.
- In Education: Analyze how students move between classes to ease hallway gridlock, see which campus facilities are the most popular, and plan future construction based on real-world usage data.
- In Corporate BYOD Environments: Get a clear view of which conference rooms and common areas see the most action, helping you allocate resources better and design office layouts that actually encourage collaboration.
It all starts with that first connection through a Captive Portal. When someone logs in using social login or another authentication solution like IPSK or EasyPSK, the network can begin gathering anonymous presence data. This is the moment your guest WiFi goes from being a simple courtesy to a strategic asset.
A great network design service doesn't just install equipment; it builds an entire ecosystem that delivers both seamless connectivity and critical intelligence. To see this in action, you can learn more about location analytics and how they uncover powerful patterns in customer behavior. By tapping into this data, you can finally stop guessing and start making informed decisions that directly boost your bottom line.
What to Expect from Your Network Design Partner
Kicking off a network design service project isn't just a transaction; it's a partnership. From the very first conversation to the long-term health of your system, we're in it together. Knowing what the process looks like helps set clear expectations and ensures the network we build not only works for today but is ready for whatever comes next.
It all starts with a Discovery phase. This is where we simply listen. We want to understand your specific goals, your daily operational headaches, and what you ultimately need your network to do for you. Are you a retailer looking to engage shoppers through social login? Or maybe a university that needs to securely onboard thousands of student devices using IPSK? This initial chat is absolutely critical.
The Blueprint and Build-Out
After discovery, we dive into the Site Survey and Design phase. This is where the technical blueprint gets drawn up. Our engineers get hands-on, analyzing your physical space to map out the perfect placement for hardware, like Cisco Meraki access points, to guarantee rock-solid coverage everywhere it's needed. This plan is the foundation of a great user experience.
Once you approve the design, we move to Implementation. This is where the blueprint becomes a reality. Hardware is professionally installed and configured precisely to the design specs. That means setting up secure authentication solutions, branding your Captive Portals for guest WiFi, and properly segmenting the network for your BYOD Corporate sector needs.
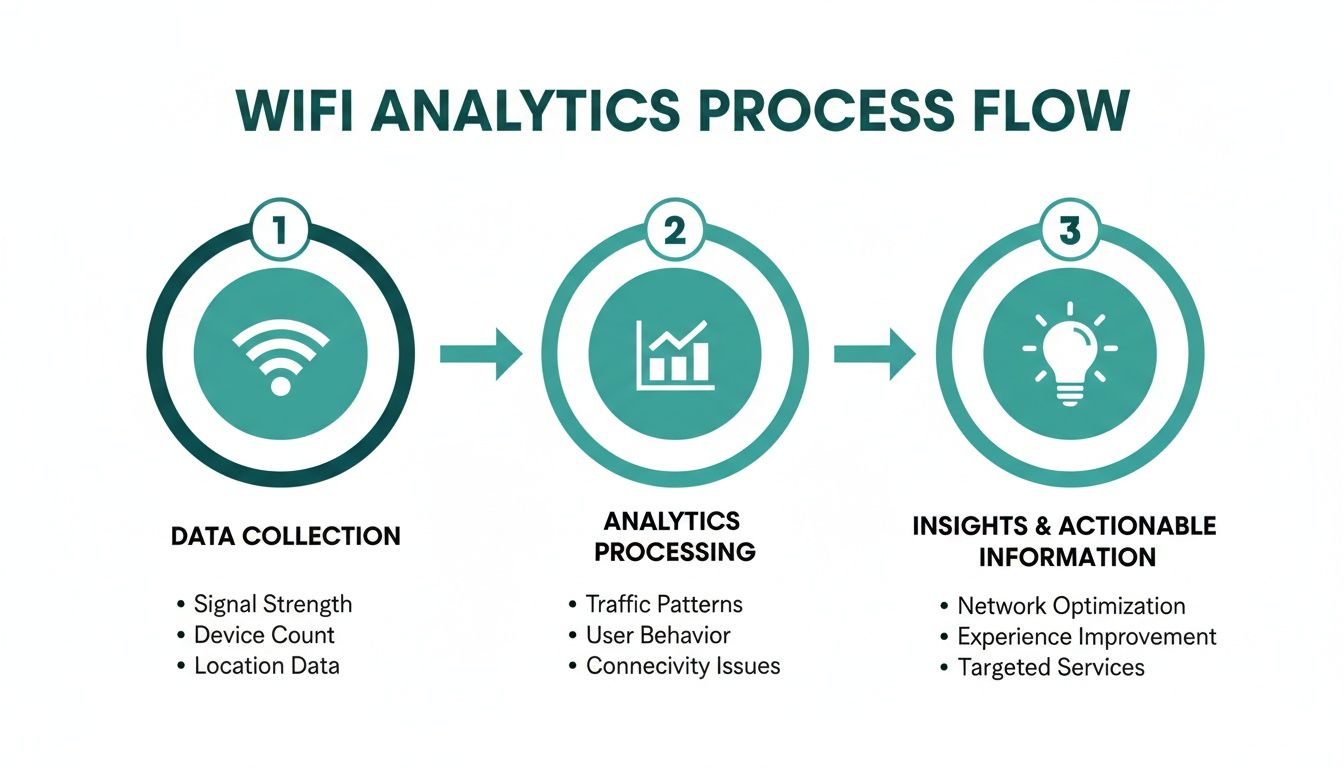
This diagram breaks down the simple but powerful flow from raw data collection to real business intelligence.
Ultimately, this whole process turns simple Wi-Fi signals into a goldmine of insights you can use to make smarter business decisions.
Testing and Ongoing Success
The last step before we go live is Testing and Handover. We are meticulous here, testing every single component of the network to confirm that performance, security, and the user experience are all up to snuff. We make sure everything works just as it should, from seamless social wifi logins to secure connections via EasyPSK.
A true network partner doesn't just install the hardware and walk away. The handover is really just the beginning of our commitment to your success. We're here for the long haul, providing ongoing support to keep your network optimized and secure.
But our work isn't done at handover. We believe in the importance of ongoing management and support because technology and business needs are always changing. Your network has to be able to adapt. We stick around to provide continuous optimization, security updates, and day-to-day support, making sure your network remains a powerful asset for your organization.
Your Network Design Questions, Answered
Let's tackle some of the most common questions we hear about professional network design and getting the most out of platforms like Cisco Meraki.
What's The Single Most Important Part Of A Network Design?
If you had to pick just one thing, it would be the wireless site survey. It’s the bedrock of the entire project.
You can have the best Cisco Meraki gear in the world, but without a deep understanding of your building's layout and the invisible world of radio frequency (RF) interference, that equipment will never live up to its potential. A proper survey ensures your investment in advanced features like Captive Portals and secure authentication solutions rests on a foundation of solid, reliable connectivity.
How Do You Actually Secure A Guest WiFi Network?
This is a huge priority, and the answer involves a few key layers. First and foremost, we use network segmentation. Think of it as building a digital wall that completely separates your guest traffic from your private, internal network where all your sensitive data lives.
Beyond that, it's all about how users get onto the network. For businesses with lots of visitors or BYOD (Bring Your Own Device) policies, we often turn to solutions like IPSK or EasyPSK. These systems give each user or device its own unique password, which is a world away from the security risk of having one shared password for everyone.
The real goal is to give guests a fantastic, seamless connection that is completely and totally isolated from your critical internal systems. A professional network design service ensures that separation is bulletproof.
Do You Design WiFi Differently For Specific Industries?
Of course. A generic, one-size-fits-all WiFi plan just doesn't cut it in the real world. We tailor every design to the specific challenges and goals of different environments.
- Education: The design has to handle extreme density—like a lecture hall packed with students—while securely managing thousands of personal devices with authentication solutions like IPSK.
- Retail: Here, the focus shifts to customer engagement. We design the network to support social login (social wifi) and collect valuable footfall analytics to understand customer behavior via a custom Captive Portal.
- BYOD Corporate: The number one priority is security. The entire design revolves around keeping employee-owned devices and guest traffic walled off from the core corporate network.
How Exactly Does IPSK Or EasyPSK Make A Network More Secure?
IPSK (Individual Pre-Shared Key) and its simpler cousin, EasyPSK, are a massive leap forward for network security, especially in BYOD-heavy places like schools and corporate offices. Instead of a single password that everyone knows (and shares), each person gets their own private key.
Think about the implications. If one employee leaves or a student's device is compromised, you can revoke that one specific key in seconds without disrupting a single other person. This approach makes managing hundreds or even thousands of personal devices simple, secure, and fully traceable, drastically cutting the risk of a major security incident.
Ready to turn your network from a basic utility into a powerful business tool? The experts at Splash Access specialize in designing smart, secure, and high-performing WiFi solutions. Get in touch with us today to start building a network that truly works for you.