Hey there! If you want to really get a handle on your network traffic, you need more than just raw data. It's all about combining powerful tools, like the friendly Cisco Meraki dashboard, with smart authentication methods. This is how you figure out who is doing what, and it’s the key to shifting your network management from reactive problem-solving to proactive strategy.
Why You Need to See What's on Your Network
Ever feel like you're flying blind managing your network? It doesn't matter if you're overseeing Wi-Fi for an Education campus, a busy Retail chain, or a BYOD Corporate office—your network is the operational backbone. Without clear visibility, you're missing a huge piece of the puzzle.
Monitoring network traffic isn't just a task for the IT department anymore. It's about uncovering insights that directly impact security, performance, and the overall user experience. The need for this level of visibility is exploding. In fact, the global network traffic analytics market was valued at around USD 6.8 billion in 2025 and is on track to hit an incredible USD 27.7 billion by 2035. You can dig deeper into these trends and discover more insights on Future Market Insights.
From Anonymous Data to Actionable Insights
Seeing a flood of data is one thing, but knowing who is behind it is a total game-changer. This is especially true in environments like schools, stores, and offices where dozens, if not hundreds, of different devices connect every day. Without a way to identify them, all that traffic is just anonymous noise.
This is where tools like Captive Portals and modern Authentication Solutions step in. By simply asking users to log in, you can immediately tie network activity back to a specific person.
Let’s chat about some real-world examples:
- In Education: You could track student bandwidth usage to make sure crucial learning platforms get priority over Netflix during class time.
- In Retail: It’s a great way to see how guest Wi-Fi traffic might be affecting your Point-of-Sale system and to gather some useful customer data through your Captive Portal.
- In a BYOD Corporate Setting: You can securely onboard employee devices and ensure their personal phone usage doesn't create security holes or drag down network performance.
When you can link traffic to actual users, you can pinpoint the source of a slowdown in minutes, investigate a security flag with confidence, or enforce your acceptable use policies effectively. Anonymous data suddenly becomes actionable intelligence.
To give you a clearer idea, here's a look at the specific goals and benefits of monitoring network traffic across different environments.
Why Network Monitoring Matters in Your Sector
A look at the specific goals and benefits of monitoring network traffic across different environments.
| Monitoring Goal | Education Sector Application | Retail Sector Application | BYOD Corporate Application |
|---|---|---|---|
| Performance Optimization | Prioritize bandwidth for educational apps and online testing platforms. | Ensure guest Wi-Fi doesn't slow down critical POS and inventory systems. | Balance bandwidth allocation between business-critical apps and personal use. |
| Security Enforcement | Block access to malicious or inappropriate content on school-owned devices. | Prevent guest users from accessing secure internal retail networks. | Isolate and investigate devices exhibiting suspicious behavior, like data exfiltration. |
| Policy Compliance | Enforce CIPA (Children's Internet Protection Act) compliance. | Gather anonymized foot traffic data for marketing insights while respecting privacy. | Ensure employees adhere to the company's acceptable use policy on their personal devices. |
| User Experience | Guarantee a stable connection for digital learning tools and video lectures. | Offer a seamless and fast login experience for shoppers to boost satisfaction. | Provide reliable connectivity for employee productivity without constant IT tickets. |
As you can see, the "why" behind monitoring is deeply connected to the unique challenges of each environment.
The Power of Advanced Authentication
Simple logins are a great start, but we can get even more granular. This is where advanced methods like IPSK (Identity Pre-Shared Key) or EasyPSK come into play. Instead of a single, shared password for everyone, each user or device gets its own unique key.
Think about a corporate office where every employee connects their personal phone to the Wi-Fi. With EasyPSK, each person has their own unique password. If one employee's device suddenly starts hogging all the bandwidth or showing signs of malware, a platform like the Cisco Meraki dashboard will tell you exactly whose device it is. This level of specific detail is crucial for modern network management, turning a potentially chaotic BYOD free-for-all into a secure, efficient, and well-managed system.
Choosing Your Tools in the Cisco Meraki Ecosystem
Getting a handle on your network traffic starts with picking the right gear for the job. If you're already working within a Cisco or Meraki environment, you’re in a great spot to get deep insights without a ton of extra work. The real powerhouse here is the cloud-based Meraki dashboard—it’s the command center for your entire network.
Think about it: you can see real-time application usage, drill down into individual client data, and spot traffic trends across all your school buildings or retail stores with just a few clicks. That's the visibility we're aiming for. This isn't just about passively collecting data; it's about turning that information into smart decisions that actually boost your network's performance and security.
Matching the Tool to Your Mission
Here’s the thing: an effective monitoring strategy is never one-size-fits-all. The way you watch your network traffic needs to align directly with what your organization is trying to accomplish. Your priorities will look completely different depending on your industry.
Let's break down how to approach this:
- In Education: Your main goal is to support learning. That means you need to prioritize bandwidth for educational apps, make sure online testing platforms are rock-solid, and manage student device traffic to keep them on task. Your monitoring tools should make enforcing acceptable use policies almost automatic.
- In Retail: For retailers, it’s all about business continuity and the customer experience. Your tools have to ensure that critical Point-of-Sale (POS) systems never slow down, even when the guest Wi-Fi is slammed. You'll also want to pull insights on customer behavior from that guest network using your Captive Portal.
- In a BYOD Corporate Office: The big challenge here is walking the line between productivity and security. You need to lock down sensitive corporate data on personal phones and laptops while still giving everyone seamless access to the apps they need to do their jobs.
Start with your end goal. First, define what a "healthy network" actually looks like for your specific environment. From there, you can pick and choose the features within the Meraki dashboard that will help you get there—and stay there.
Prioritizing Key Monitoring Features
Once you know your mission, you can zero in on the features that truly matter. Don't get lost in a sea of technical specs; instead, focus on the capabilities that solve your real-world problems.
For instance, a school district will get huge value from application-level visibility. It lets them see if students are secretly streaming videos instead of using the learning software they’re supposed to be on. It's a game-changer for keeping everyone focused.
Likewise, a corporate office with a BYOD policy will lean heavily on authentication tools like IPSK (Identity Pre-Shared Key) or EasyPSK. These systems give each user their own unique Wi-Fi password, which turns a jumble of anonymous traffic into a clear picture of who is doing what. That simple shift is massive for troubleshooting. When an issue pops up, you can trace it back to a single user's device. You're no longer guessing—you know. And that’s the foundation of great network management.
Securing Access with Captive Portals and Modern Authentication
True network control begins at the front door. It’s not just about watching traffic once it’s flowing through your network; it’s about having the final say on who gets to create that traffic in the first place. This is where Captive Portals and modern Authentication Solutions really prove their worth.
Think about how different an Education sector's needs are from a Retail store's. The school has to juggle access for students, faculty, and guests, each with their own set of rules. A retail store, on the other hand, wants to give shoppers easy Wi-Fi access while gathering useful data. A well-designed captive portal, especially one that works with a Cisco Meraki setup, is what makes this kind of tailored access possible.
The demand for this level of visibility is only growing. With the explosion of IoT devices and cloud computing, the market for network traffic monitoring tools is expected to reach about USD 15 billion in 2025. That number is projected to grow at a 12% CAGR through 2033, which tells you just how critical solid security and performance management have become.
Tying Traffic to Individuals with IPSK and EasyPSK
Now, let's get into the real game-changers for environments with lots of personal devices, like corporate BYOD programs. I'm talking about EasyPSK and Identity Pre-Shared Keys (IPSK). These tools completely change how you monitor network traffic because they get rid of the old, anonymous, single Wi-Fi password for everyone.
Instead, you can give a unique Wi-Fi password to every single user or device.
- In Education: Imagine every student and staff member having their own key. You can immediately see who is accessing what, which makes enforcing policies a breeze.
- In Retail: You can grant secure, individual access for staff devices while keeping all the guest traffic completely separate and managed.
- For Corporate BYOD: Onboarding an employee's personal phone or laptop is much more secure when it has its own credential tied directly to that user.
Suddenly, network traffic isn't just a sea of anonymous data. It's tied directly to a specific person. This makes it incredibly easy to pinpoint a bandwidth hog, look into a security alert, or troubleshoot a connectivity problem with laser focus.
Strengthening Your Authentication Strategy
These modern authentication methods create a solid foundation for a secure network. When you can tie every connection back to a known identity, your power to manage and protect your digital space skyrockets. This approach doesn't just tighten up security; it actually makes the day-to-day work of network administration a lot simpler.
To really lock things down, it’s worth looking into other advanced methods. Understanding what two-factor authentication is and how to implement it can be a critical piece of the puzzle. By layering your security measures, you build a much more resilient and trustworthy network for everyone, from students in a classroom to employees at corporate HQ.
Turning Raw Network Data Into Actionable Insights
Collecting network data is just the beginning. The real magic happens when you translate those raw numbers into smart, real-world decisions. With a platform like the Cisco Meraki dashboard, you’re not just watching traffic flow by; you’re learning the story it tells about your network’s health and what your users are actually doing.
This has never been more critical. We're seeing a massive surge in global network traffic, and it’s changing the game for how organizations need to monitor their infrastructure. According to a deep dive into network traffic trends by Nokia Bell Labs, both consumer and business traffic are set to grow at a staggering rate through 2033. Staying ahead of that curve is no longer optional.
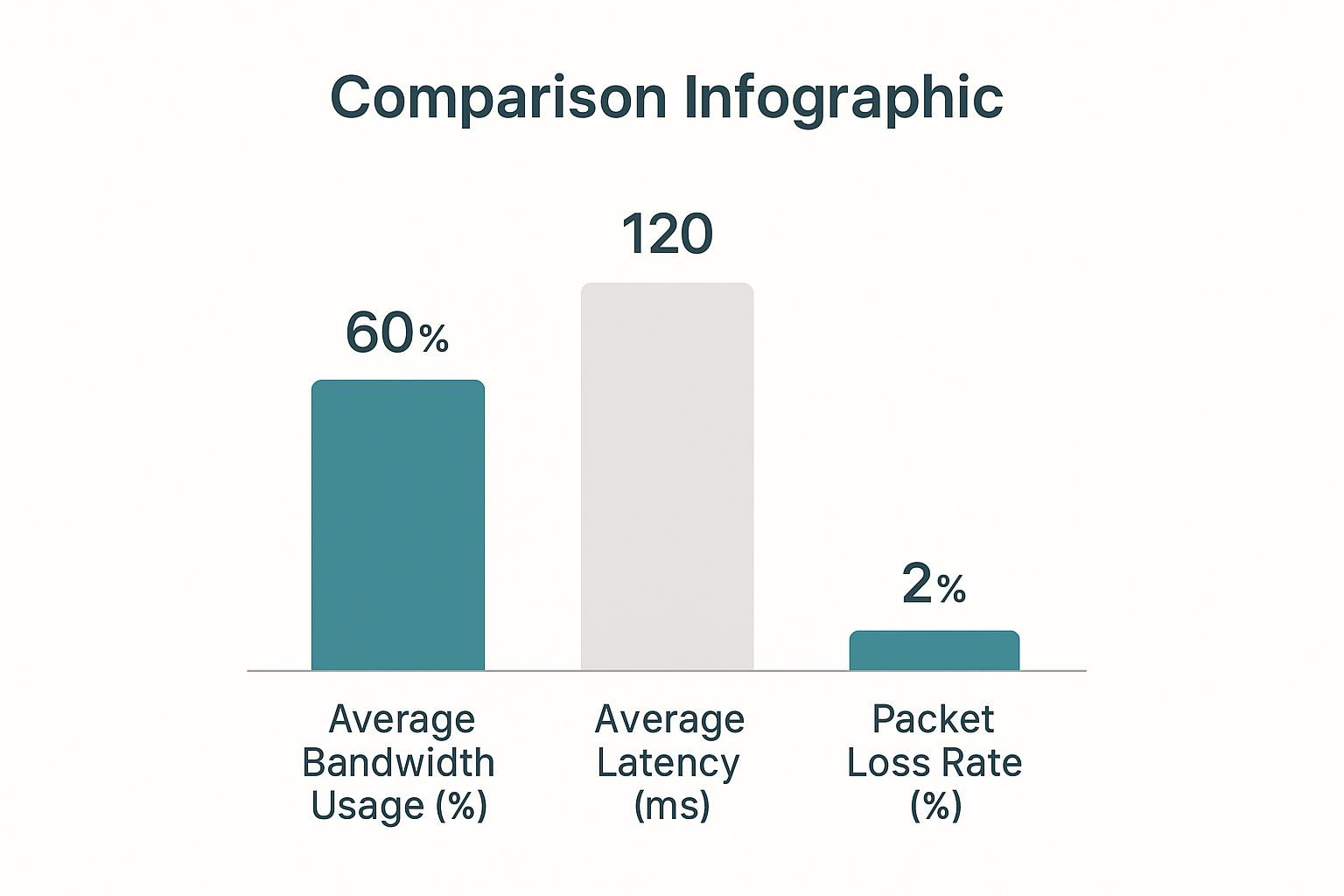
A few key metrics—bandwidth usage, latency, and packet loss—give you a constant pulse on your network’s health.
When you see high latency or packet loss, you can bet your users are feeling it. These are direct indicators of a poor experience, and your dashboard is the first place you’ll spot them.
Real-World Scenarios and Smart Responses
Let’s get practical and look at how you can use this data to solve actual problems. The whole point is to connect the dots between the charts on your screen and the action you need to take on the ground.
Picture this: you’re running IT for a busy retail store. Your Meraki dashboard lights up with a massive bandwidth spike on the guest Wi-Fi, right in the middle of the lunch rush. A minute later, a manager calls to complain the payment terminals are lagging. That’s no coincidence. The data is screaming that guest traffic is choking out your critical business systems.
The insight isn't just that the network is slow; it's why it's slow. This allows you to create traffic-shaping rules in your Meraki setup to instantly prioritize payment terminal traffic over guest browsing, ensuring transactions are always fast and reliable.
Here are a few other situations where data turns into decisive action:
- In a school setting, you notice that video streaming apps are eating up 40% of your network bandwidth during class hours. With that information, you can confidently implement policies to throttle or block recreational streaming, freeing up precious resources for online learning tools.
- In a corporate office with a BYOD policy, you can use Authentication Solutions like IPSK or EasyPSK to link traffic directly to a specific user's device. If you see one device suddenly uploading huge amounts of data, you can pinpoint the user and investigate for malware or unauthorized file sharing, stopping a potential security breach in its tracks.
The table below outlines a few common headaches you might encounter and the steps you can take within Meraki to fix them.
Common Network Issues and How to Fix Them
| Observed Issue | Potential Cause | Recommended Action in Meraki |
|---|---|---|
| Sluggish Wi-Fi for all users | A few devices are hogging all the bandwidth (e.g., streaming 4K video). | Navigate to Network-wide > Clients. Identify the high-usage devices and apply a per-client bandwidth limit. |
| Critical apps (VoIP, PoS) are slow | Non-essential traffic (social media, video) is getting priority. | Go to Wireless > Firewall & traffic shaping. Create a new traffic shaping rule to prioritize the critical application's traffic. |
| Reports of dead spots in a specific area | Poor wireless coverage or interference. | Use the Wireless > RF spectrum tool to visualize interference. Consider repositioning an AP or adding a new one to improve coverage. |
| A specific device is acting suspiciously | The device could be compromised or running an unauthorized P2P app. | Use the client details page to see the device's traffic analytics. If suspicious, block the client from the network with a single click. |
By using your dashboard to quickly diagnose the root cause, you can move from troubleshooting to solving problems much faster.
From Analytics to Optimization
The client analytics and application reports in your dashboard are your secret weapons for proactive management. They help you spot trends long before they become full-blown problems.
For instance, are you seeing a steady climb in the number of connected devices on campus month after month? That’s your cue to start planning for a capacity upgrade instead of waiting for things to break.
By regularly checking this data, you’ll build an intuitive understanding of your network's daily, weekly, and monthly rhythms. This historical context is gold, helping you make smarter decisions for both immediate troubleshooting and long-term strategic planning. For more ideas on how to organize this information, take a look at our guide on building relevant summary reports.
It’s all about making your data work for you, shifting your role from a network firefighter to a true network strategist.
Stop Fighting Fires: Proactive Monitoring for Peak Network Health
Great network management means you stop being a firefighter and start being a strategist. It's about spotting and solving problems long before a user ever notices something is wrong. This is the critical shift from reacting to issues to proactively preventing them, keeping your Wi-Fi running flawlessly and showcasing the true value of your IT team.
The secret? Setting up intelligent alerts and using your own historical data to see what's coming next.
This forward-thinking approach is a cornerstone of modern network management. For a more comprehensive look, we've put together a complete guide covering network monitoring best practices.
Set Up Alerts That Actually Matter
Imagine getting a notification the second an issue pops up, instead of hearing about it from an angry user an hour later. That’s what smart alerts do. With a platform like the Cisco Meraki dashboard, you can configure alerts for nearly any event, giving you a huge head start on troubleshooting.
Let's look at how this plays out in the real world:
- Retail: You could get an alert if the primary access point covering your checkout lanes goes offline. This lets you dispatch a tech immediately, preventing a line of frustrated customers and lost sales.
- Education: An alert can flag a single student device suddenly pulling down massive amounts of data. That could be malware or a P2P client, and you can isolate it before it bogs down the network for everyone else.
- Corporate BYOD: What if Wi-Fi latency suddenly spikes above your baseline? An alert can tell you right away, pointing to a potential misconfiguration or an overloaded AP that's about to drag down productivity.
By setting these kinds of tripwires, you transform your monitoring dashboard from a passive reporting tool into an active, 24/7 early warning system. You’re making the data work for you.
Use Your History to Predict the Future
Beyond just instant alerts, all that historical data you're collecting is a goldmine. It’s your crystal ball for capacity planning. Analyzing trends over weeks and months helps you spot patterns that signal a need for an upgrade long before performance takes a nosedive.
Think about a school campus that sees a steady climb in connected devices semester after semester. That data is a clear sign that it's time to budget for more access points or a bandwidth increase.
In a corporate BYOD environment, maybe you notice that video conferencing apps are eating up more and more bandwidth each quarter. That’s your cue to adjust traffic-shaping rules to prioritize that critical traffic. This is where tools that provide user context, like Captive Portals and Authentication Solutions such as IPSK or EasyPSK, become invaluable. They help you make data-driven decisions to prevent future bottlenecks, not just guess at what you might need.
Common Questions About Network Traffic Monitoring
Let's dive into some of the real-world questions we get all the time about monitoring network traffic. These are common scenarios, especially for anyone managing networks in schools, retail stores, or offices with bring-your-own-device (BYOD) policies.
How Can I See Traffic From One Specific User's Phone in a BYOD Environment?
This is a classic problem, but modern authentication makes it surprisingly easy to solve. Instead of one shared password for everyone, you can use an Authentication Solution like EasyPSK or an Identity Pre-Shared Key (IPSK).
With this approach, every single user gets a unique password to join the Wi-Fi. The magic here is that their traffic is no longer anonymous.
In the Cisco Meraki dashboard, all of that user's activity is automatically linked to their specific identity. You can instantly filter for that one person, see exactly which apps they're using, and get a clear picture of their total bandwidth consumption. It completely changes the game for troubleshooting a specific complaint or enforcing usage policies.
Can I Guarantee My Retail Payment Systems Always Have Enough Bandwidth?
Absolutely, and this is a critical task for any retail environment. The tool for the job here is traffic shaping. First, you'll need to use your monitoring tools to positively identify the traffic flowing from your Point-of-Sale (POS) devices.
Once you know what that POS traffic looks like, you can jump into the Meraki dashboard and create a specific traffic shaping rule. This rule’s only job is to give your payment systems the highest priority on the network, no matter what.
This simple configuration ensures your critical payment transactions always go through without a hitch, even if your guest Wi-Fi is slammed with shoppers streaming video. It’s a direct way to protect revenue and keep those checkout lines moving.
What Is the Safest Way to Offer Guest Wi-Fi?
The best way to handle this is with a two-pronged strategy: combine a Captive Portal for access control with network segmentation on the backend.
Here's how that breaks down:
- The Captive Portal: This is the branded login page your guests see before they get online. It’s the perfect spot for them to agree to your terms of service.
- Network Segmentation: This is the crucial security step. You configure your network to completely isolate all guest traffic onto its own VLAN.
This setup builds a virtual wall between your guests and your sensitive internal resources, like company servers or that POS system we just prioritized. You can offer a great Wi-Fi experience without ever exposing your core operations to risk. For a deeper look at the options available, our guide on various network performance monitoring tools is a great resource.
Take control of your guest Wi-Fi and turn network data into real insights with Splash Access. We provide powerful, easy-to-deploy captive portals and authentication solutions for your Cisco Meraki network. https://www.splashaccess.com