Ever think about your business network as its central nervous system? It's that silent, invisible force connecting your teams, powering your most critical apps, and making sure sensitive data gets where it needs to go—safely and instantly. Real enterprise networking solutions are a whole world away from the simple Wi-Fi you have at home; they're the smart, scalable, and secure backbone that modern business truly runs on.
The Foundation of Modern Business Connectivity
In a world that’s always on, a basic router and a handful of access points just won’t cut it anymore. Whether you're managing a sprawling Education campus, a nationwide chain of Retail stores, or a corporate headquarters with a flexible Bring Your Own Device (BYOD Corporate) policy, you need a network that can handle some serious complexity without breaking a sweat.
This is where specialized, enterprise-grade systems come in. They are built from the ground up to manage hundreds or even thousands of devices connecting all at once, guaranteeing a smooth, reliable experience for everyone. For instance, industry leaders like Cisco and their brilliant cloud-managed platform, Meraki, engineer networks that are not only powerful but also incredibly smart. You can get a deeper look into how these systems operate in our friendly guide explaining what is Cisco Meraki.
The move toward smarter, more manageable networks is fueling massive industry growth.
The global enterprise networking market is on track to hit nearly $298.3 billion by 2030, according to analysis from Grand View Research. This number alone shows just how essential this technology has become for businesses of all shapes and sizes.
To better understand what makes an enterprise network tick, let's break down its core components. These are the building blocks that work together to deliver the performance, security, and reliability that businesses demand.
Key Components of a Modern Enterprise Network
| Component | Primary Function | Why It Matters for Your Business |
|---|---|---|
| Switches | Connect devices (computers, printers, servers) on the same local network. | They are the traffic directors of your internal network, ensuring data gets from point A to point B efficiently and without bottlenecks. |
| Routers | Connect different networks together and route traffic between them (e.g., your office to the internet). | This is your gateway to the outside world. A good router ensures fast, secure, and reliable internet access for your entire organization. |
| Access Points (APs) | Provide wireless connectivity (Wi-Fi) for devices like laptops, phones, and tablets. | High-performance APs deliver strong, consistent Wi-Fi coverage across your entire facility, eliminating dead zones and slow speeds. |
| Firewalls | Act as a security barrier, monitoring and controlling incoming and outgoing network traffic. | This is your first line of defense against cyber threats, protecting your sensitive business data from unauthorized access. |
| Network Management Software | A centralized dashboard for monitoring, configuring, and troubleshooting the entire network. | This "single pane of glass" gives your IT team complete visibility and control, drastically simplifying network management. |
With these building blocks in place, you create a foundation that's far more capable than any standard, off-the-shelf setup. The difference becomes obvious when you look at real-world demands.
Why a Standard Network Just Isn't Enough
Picture a university lecture hall where 300 students are all trying to stream a high-definition video at the same time. Or a retail store processing dozens of credit card transactions a minute while also providing guest Wi-Fi to shoppers. These are everyday scenarios that would completely cripple a standard network.
Here’s what truly sets enterprise solutions apart:
-
Advanced Security: We're talking way beyond a single shared password. Enterprise networks deploy sophisticated Authentication Solutions like IPSK (Identity Pre-Shared Key) and EasyPSK. With these, every single user or device gets its own unique, private key. This makes it incredibly simple to grant or revoke access for thousands of devices without compromising security.
-
Guest Access Management: For businesses in hospitality, Retail, or Education, offering great guest Wi-Fi is no longer optional. Captive Portals—those branded login pages you see at airports and coffee shops—provide a secure, controlled, and professional way to welcome visitors onto your network without giving them access to your private systems.
-
Centralized Control: Forget about logging into individual devices one by one to make changes. With an enterprise solution from a provider like Cisco Meraki, IT teams can manage an entire global network from a single, cloud-based dashboard. This makes troubleshooting problems, pushing out updates, and enforcing security policies across all locations incredibly efficient.
Solving The Secure Authentication Challenge
So, how do you give students, shoppers, and employees the easy Wi-Fi access they expect without throwing your network's security out the window? This is the million-dollar question in modern networking. Just handing out a single password for everyone might feel simple, but it’s a massive security hole. Once that password gets out, it's out forever, and your network is left wide open. Thankfully, modern enterprise networking solutions have moved way past that risky approach.
We need smarter ways to control who gets on the network, especially in high-traffic places like Retail stores, university campuses, and any office with a Bring Your Own Device (BYOD Corporate) policy. This is where modern authentication methods really shine, making sure the right people get connected while keeping everyone else out.
Welcoming Guests with Captive Portals
You’ve definitely seen Captive Portals a hundred times. They're those branded login pages that greet you when you connect to the Wi-Fi at an airport, hotel, or your local coffee shop. Instead of fumbling with a complicated password, they offer a simple, clean gateway to get online.
For businesses, particularly in Retail and Education, Captive Portals are a fantastic tool. They don't just grant internet access; they create a professional first impression and open up new opportunities.
- Retail: A store can display a login page featuring its logo and latest sales. A shopper might log in using their email address, giving the business a new marketing contact in exchange for free Wi-Fi.
- Education: A university can use a Captive Portal for conference attendees or campus visitors, giving them internet access without letting them onto the main network used by students and staff.
This approach lets guests get online fast without ever touching the core, protected network where all the sensitive information lives.
A well-designed Captive Portal does double duty. It secures your guest network and simultaneously acts as a powerful tool for engagement and marketing, turning a simple Wi-Fi connection into a valuable business asset.
Beyond Shared Passwords with IPSK and EasyPSK
Captive Portals are perfect for guests, but what about trusted users like employees or students? Making them sign in through a portal every single day would get old fast. But giving everyone the same "Staff-WiFi-123" password is a security disaster waiting to happen. If one person leaves, you’re stuck changing the password for the entire organization.
This is exactly the problem that advanced Authentication Solutions like Identity Pre-Shared Key (IPSK) and EasyPSK were designed to solve. Systems like Cisco Meraki pioneered this technology, and it's a brilliant fix.
Instead of one password for the whole group, IPSK assigns a unique, personal key to each user or device. It’s like giving every employee their own private key to the office Wi-Fi.
This completely changes the game for BYOD corporate environments. When a new hire starts, IT can instantly issue a key for their laptop and phone. If that employee leaves the company, their keys can be revoked with a single click, cutting off their access immediately without affecting anyone else. This level of granular control is what makes enterprise-grade Wi-Fi so secure and easy to manage. Looking into different user authentication techniques can help you pinpoint the best strategy for your own organization.
By pairing the welcoming simplicity of Captive Portals for guests with the strong, individual security of IPSK for trusted users, you create a smart, layered defense. This two-pronged approach ensures your enterprise networking solutions are both incredibly user-friendly and exceptionally secure, no matter who needs to connect.
Tailoring Networks for Education, Retail, and Corporate
A busy university campus, a high-end retail shop, and a sprawling corporate headquarters all need great connectivity. But what "great" means for each is completely different. This is where modern enterprise networking solutions really show their value. It's not about a cookie-cutter setup; it's about sculpting the network to match the specific workflow, security demands, and daily rhythm of each environment.
Think of it like building a road system. The design for a quiet neighborhood cul-de-sac is nothing like the multi-lane, high-security layout needed for an international airport. In the same way, the Education, Retail, and Corporate sectors each need a unique network architecture to keep things running smoothly, securely, and efficiently for everyone.
Smart Networks for Modern Education
An educational campus is a whirlwind of digital activity. You have thousands of students, faculty, and guests all trying to connect, using a mix of university-owned equipment and their own personal devices. The real challenge is giving everyone the access they need while walling off sensitive administrative and research data.
A well-designed educational network, often running on Cisco and Meraki hardware, handles this by segmenting traffic. It essentially creates separate, secure "lanes" on the digital highway:
- Student Network: This is the main thoroughfare, offering broad access to learning resources and the internet, usually with content filtering to keep the environment safe and focused.
- Faculty & Staff Network: This is a more privileged lane, providing access to internal systems like grading portals and administrative databases, protected by strong authentication.
- Guest Network: Think of this as a temporary access road. It's completely isolated from internal systems and managed with a simple Captive Portal for visitors to get online without posing a security risk.
By using Authentication Solutions like IPSK (Identity Pre-Shared Key), the IT team can give each student and staff member a unique password for all their devices. This makes managing thousands of connections far simpler and more secure, ensuring that only the right people get access to the right resources.
Engaging Shoppers in Retail Environments
In the retail world, the network has two very different, very important jobs. First, it has to reliably run the business itself—the point-of-sale (POS) terminals, inventory scanners, and security cameras. This internal network needs to be iron-clad and completely isolated to protect sensitive payment and operational data.
At the same time, offering free guest Wi-Fi has become a fantastic way to draw in shoppers and encourage them to stay longer. This is where a branded Captive Portal can work wonders. When a customer logs on, they're greeted with a custom splash page showing the store’s logo, the latest sales, or an invitation to join the loyalty program. It turns a simple internet connection into a powerful marketing tool. Choosing the right Wi-Fi solutions for business is key to making this a seamless experience.
By separating the secure operational network from the public guest network, retailers can confidently engage customers without ever putting their critical business systems at risk.
Supporting Flexibility in the Corporate World
The modern office is all about flexibility, driven largely by the rise of Bring Your Own Device (BYOD) policies. Employees expect to connect and work from their personal laptops, tablets, and phones. Of course, this introduces a major security headache: how do you let all these personal devices on the network without opening the door to data breaches?
This is where advanced enterprise networking solutions from platforms like Cisco Meraki are indispensable. Using IPSK or EasyPSK, an IT administrator can issue a unique, secure key for each of an employee's personal devices.
This approach gives you incredible, fine-grained control. You can create policies so an employee's smartphone can get email and calendar updates but is blocked from accessing the company's core file server. And if that employee leaves the company? A single click revokes all their keys, instantly cutting off access from all their devices. This level of control is what makes a secure and productive BYOD environment possible.
How AI and Automation Are Making Networks Smarter
The best networks today don't just sit there waiting for something to break. They’re constantly working in the background, actively hunting for and fixing problems before anyone even notices. This is where Artificial Intelligence (AI) and automation come in, and they're completely changing the game for enterprise networking solutions.
Let's unpack how AI-powered platforms can predict network hiccups, automatically optimize Wi-Fi in a packed lecture hall, and spot security threats the moment they appear.
Think of it as giving your IT administrator a brilliant co-pilot—one that’s always monitoring performance, handling the mundane tasks, and flagging potential issues. Instead of constantly reacting to problems that have already disrupted your business, AI allows your network to see trouble coming and adjust on the fly.
This move toward intelligent automation is a huge driver of growth in the networking industry. AI is being baked into network management and security to strengthen defenses and intelligently manage traffic. This means networks can now handle their own setup, monitoring, issue detection, and even patching. It gives network admins incredible adaptability and efficiency, as highlighted in findings on the enterprise networking market on precedenceresearch.com.
Getting Ahead of Problems with AI
Picture a university library during finals week. Thousands of students are trying to connect to the Wi-Fi at the same time—a classic recipe for a network meltdown. In a traditional setup, the IT helpdesk would be drowning in calls from frustrated students.
Now, imagine that same scenario with an AI-driven network from a provider like Cisco. The system sees the surge in demand coming. It automatically reallocates bandwidth, seamlessly shifts devices to less congested Wi-Fi channels, and tweaks access point settings to handle the load. The students get the fast, reliable connection they need, and the IT team never even receives a single trouble ticket.
This isn't just for campuses. The same principle applies to a Retail store during a Black Friday sale or a BYOD Corporate office during an all-hands video conference.
AI transforms network management from a reactive, fire-fighting role into a proactive, strategic one. It's about solving problems before users ever know they exist.
A Sharper Eye on Security and Visibility
Beyond pure performance, AI is a powerful ally in network security. Its first job is to learn what "normal" network traffic looks like for your organization. Once it has that baseline, it can spot anomalies instantly.
So, when a laptop that usually only accesses marketing files suddenly tries to connect to a secure finance server, the AI flags it as a potential threat in real-time. This kind of instant anomaly detection is far faster and more reliable than any human could ever hope to be, making it a critical tool for fending off modern cyber threats.
AI also helps make sense of the mountains of data a network produces. To see how this works in the real world, check out how Meraki Insight is accelerating IT by turning complex data into clear, actionable information.
Putting Routine Tasks on Autopilot
Finally, automation gives your valuable IT staff their time back. Instead of getting bogged down in tedious, repetitive work, they can set the rules and let the system handle the grunt work.
- Zero-Touch Provisioning: New hardware can be shipped to a remote office, plugged in, and it automatically downloads its configuration from the cloud. No IT visit required.
- Automated Security Updates: The system ensures every single device is running the latest, most secure firmware without anyone having to lift a finger.
- Intelligent Reporting: AI generates easy-to-read reports on network health, usage patterns, and potential weak spots that need attention.
By putting these daily tasks on autopilot, modern enterprise networking solutions empower IT teams to stop just keeping the lights on. They can finally focus on the bigger, more strategic projects that actually move the business forward.
Choosing Your Network Architecture
So, where should your network's brain live? In a server room down the hall, somewhere in the cloud, or maybe a little of both? This is one of the first, and most important, questions you’ll face when designing your enterprise networking solutions. The answer dictates how you'll manage, secure, and grow your entire operation.
Let's walk through the three main ways to build a network. We'll start with the classic on-premises model, then jump into the much more flexible cloud-managed approach, and finally, see how a hybrid setup can give you the best of both.
The Traditional On-Premises Model
Picture an on-premises network as a completely self-sufficient fortress. All your gear—the routers, switches, firewalls, and servers—is physically located inside your building. Your IT team has direct, hands-on control over everything.
For years, this was the only game in town for any serious business network. The biggest plus is that you have total physical command of your hardware. But that control comes with a lot of responsibility. You're on the hook for all of it: hardware upkeep, software updates, security patches, and swapping out old equipment.
The Cloud-Managed Revolution
The cloud-managed model, with platforms like Cisco Meraki leading the charge, turns the old way of thinking on its head. Instead of a blinking server rack in a closet, your network’s control panel lives in the cloud. This means your team can configure, monitor, and fix issues across the entire network—whether it's one office or a hundred—all from a web browser.
This is a game-changer for businesses with multiple locations, like a Retail chain or a university with several campuses. Suddenly, a small IT team can manage a massive, spread-out network without ever getting on a plane. As you weigh your options, it's also worth considering how different data pipeline architectures might influence your network's performance and data flow needs.
This shift isn't just a niche trend; outsourcing infrastructure management is now the dominant model because it's more cost-effective and provides access to specialized skills. In fact, it now holds the largest market share in the infrastructure segment.
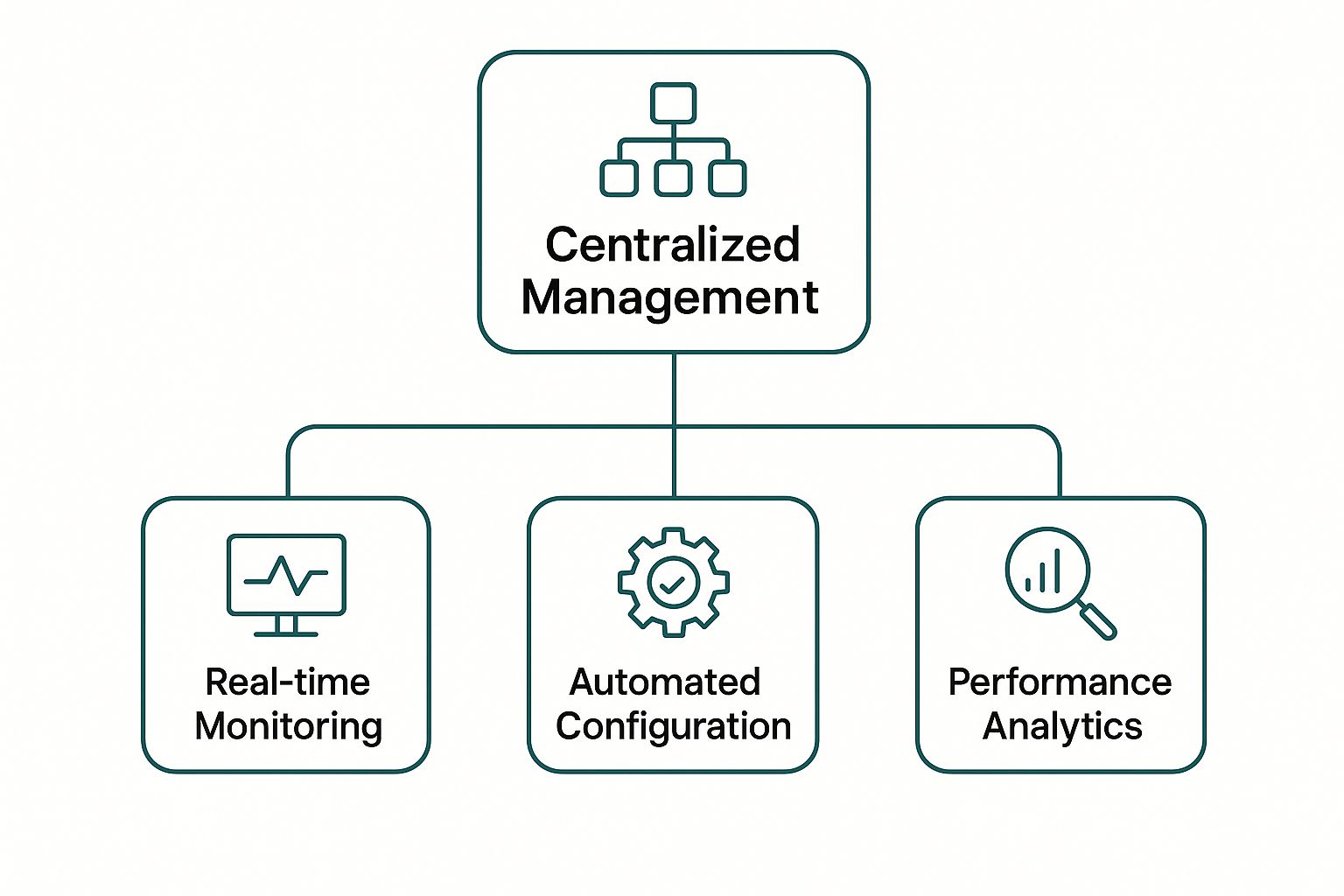
This centralized, "single pane of glass" management is what makes the cloud model so powerful, breaking down an admin's complex job into a few simple functions.
As you can see, a single management point in the cloud can oversee everything from real-time monitoring and automated configurations to deep performance analytics. It gives IT teams complete situational awareness from one dashboard.
The Flexible Hybrid Approach
So, what if you want the tight, hands-on control of an on-prem setup for some parts of your network but crave the remote flexibility of the cloud for others? That’s exactly what the hybrid model is for. It’s all about mixing and matching to get a perfect fit.
A BYOD Corporate headquarters, for example, might decide to keep its core data center and high-level security appliances on-site. This gives them maximum control over sensitive financial records. At the same time, they could use a cloud platform like Cisco Meraki to easily manage the Wi-Fi networks across all their remote branch offices.
A hybrid architecture isn't a compromise; it's a strategic choice. It allows you to place your resources where they make the most sense, balancing security, cost, and management convenience.
This approach is incredibly popular in Education. A university might manage its core campus network with on-site hardware while using the cloud to run the Wi-Fi in student housing or at satellite research facilities. By blending these models, you can build powerful and secure enterprise networking solutions that perfectly align with how your organization works, whether that means setting up Captive Portals for guests or implementing advanced Authentication Solutions like IPSK for company devices.
Best Practices for a Secure and Reliable Network
Getting your enterprise networking solutions up and running is just the start. The real work is keeping that powerful network performing perfectly day in and day out. This isn't about a one-time setup; it's about building smart habits that protect your data, your employees, and your customers from ever-present threats.
Think of your network like a building with different security clearances. You wouldn't give a visitor the keys to the server room, right? That's the core idea behind network segmentation. It’s the essential practice of creating isolated "zones" for different kinds of traffic.
For instance, the guest Wi-Fi in a Retail store or on a university campus in Education should never share the same digital space as the network handling your internal financial data. It's a simple, powerful way to contain risk.
Fortifying Your Defenses
One of the easiest yet most critical habits is keeping your firmware updated. Manufacturers like Cisco and Meraki are constantly releasing patches to fix newly discovered security holes. Skipping these updates is like leaving a window open for intruders. Make them a non-negotiable part of your routine.
It's also time to move past old security mindsets. A modern network demands a modern approach to cybersecurity. The zero-trust model is gaining huge traction for a reason—it operates on the principle of "never trust, always verify." No user or device gets a free pass, even if they're already inside your network. You can see more on this and other industry shifts in these key enterprise networking insights on marketsandmarkets.com.
Proactive monitoring is the bedrock of a reliable network. By actively watching for unusual activity—like a device suddenly trying to access sensitive files—you can catch potential security incidents before they become major problems.
Strong Authentication Solutions are the gatekeepers of this secure environment. As we've covered, methods like IPSK and EasyPSK blow old-school shared passwords out of the water, especially in BYOD corporate environments. When every user has a unique key, you can grant or revoke access instantly, dramatically shrinking your attack surface. For a deeper dive, check out our guide on the best practices for network security.
Putting these practices into action transforms your network from a basic utility into a truly resilient and secure business asset. It’s all about building a digital foundation strong enough for your organization to operate with total confidence.
Frequently Asked Questions
When you start digging into enterprise-grade networking, a few common questions always pop up. Let's break down the answers to help you get a clearer picture.
What's the Real Difference Between Regular Wi-Fi and an Enterprise Network?
It's a question I hear a lot. Isn't Wi-Fi just Wi-Fi? Not quite. The gap between your home network and a true enterprise solution boils down to three core things: scale, security, and management.
Your home router is designed for a family's worth of devices. But enterprise networking solutions from vendors like Cisco and its Meraki line are built to support hundreds, even thousands, of simultaneous users without breaking a sweat.
Then there's the security. Enterprise gear comes packed with sophisticated tools you won't find on a consumer router, like integrated firewalls, traffic shaping, and powerful Authentication Solutions like IPSK. And the best part? It's all managed from a single, centralized dashboard. That single pane of glass is non-negotiable for any growing business, school, or retail chain trying to keep its network under control.
How Do Captive Portals and IPSK Fit Together?
This one can be confusing. Are Captive Portals and IPSK competing technologies? Not at all—they’re teammates, each with a specific job.
Think of a Captive Portal as your friendly front desk for guests. It’s that branded login page you see at a coffee shop or hotel, offering temporary internet access after you provide an email or agree to the terms. It's the perfect tool for visitors in Retail or Education.
On the other hand, IPSK (Identity Pre-Shared Key)—or its user-friendly version, EasyPSK—is for your trusted, everyday users. This is for your employees in a BYOD Corporate environment or students who live on campus. It gives each person their own unique password for the Wi-Fi, which is worlds more secure than sharing one password that never changes.
A university campus is a fantastic real-world example. They can use a Captive Portal for conference attendees needing Wi-Fi for a weekend, while students and faculty connect seamlessly and securely to the main network using their individual IPSK keys.
Are Cloud-Managed Networks Actually Secure?
It's natural to wonder if managing your network from the cloud, like you do with Cisco Meraki, is as safe as keeping everything on-site. The short answer? Yes, and in many ways, it's even more secure.
Here’s a key detail: while the management happens in the cloud, all of your actual user data traffic stays on your local network. Nothing sensitive ever leaves your building.
Plus, platforms like Meraki have world-class security teams working 24/7 to hunt for global threats. They push critical security patches and firmware updates to your hardware automatically. That’s a massive advantage, ensuring you're always protected from the latest vulnerabilities—a constant battle that can easily overwhelm smaller IT teams.
At Splash Access, our entire focus is on unlocking the full power of your Cisco Meraki network. We build intuitive, powerful captive portals and authentication tools that just work.
Find out how we can help you build a secure, engaging, and data-rich Wi-Fi experience. Visit us at https://www.splashaccess.com.