Hey there! Let's talk about computer networking. At its heart, it's all about getting devices to talk to each other so they can share information. Think of it like a city's road system. Data zips between your laptop, phone, and the internet, just like cars travel between home, the office, and the shops. This guide is here to demystify that system, especially the Wi-Fi we've all come to rely on.
Your Friendly Introduction to Computer Networking
If you’ve ever jumped on the guest wifi at a coffee shop, logged into your school’s network, or connected your own device at work (BYOD), you’ve already used a computer network. It's the invisible framework that keeps us connected, and it's built on some surprisingly clever technology. My goal here is to make these concepts easy to grasp, giving you a solid foundation for understanding our hyper-connected world.
We'll be looking at how technology from industry leaders like Cisco and its cloud-managed brand, Meraki, helps create these seamless experiences. From the absolute basics of how devices communicate to the more advanced ways networks manage who gets access, we're going to break it all down in a friendly, conversational way.
From Humble Beginnings to Global Connectivity
Today's sprawling networks didn't just pop into existence. The story of modern networking really starts in the late 1960s with ARPANET, which you can think of as the internet's grandparent. Back in 1969, it was just four connected computers. By 1987, it had grown to over 20,000 hosts, paving the way for the global system we can't live without. It’s truly amazing to see this timeline of network evolution and appreciate how far we've come.
That massive leap in technology is what allows us to solve very specific challenges in different environments today:
- Education: Campuses need to provide secure, separate network access for students, faculty, and guests, all at the same time.
- Retail: Shops and venues use social wifi and social login to turn a simple internet connection into an engaging customer experience.
- BYOD Corporate: Companies have to safely manage countless personal devices connecting to their private network.
Demystifying Modern Network Access
A huge part of this guide will focus on the user's side of things—how do people actually get online? We'll take a deep dive into Captive Portals, which are those login or welcome pages you see on public networks. They're more than just a hurdle; they're critical tools for branding, security, and communicating terms of service.
A well-designed network isn't just about speed; it's about providing secure, simple, and intelligent access for every single user, whether they are a customer, a student, or an employee.
We'll also pull back the curtain on modern Authentication Solutions that are much smarter than a simple shared password. We'll touch on ideas like IPSK (Identity Pre-Shared Key) and EasyPSK, which create unique, secure credentials for every single user and device. This approach completely changes the game for managing BYOD policies in Education and Corporate sectors, removing many of the classic IT headaches.
Understanding the Building Blocks of a Network
Every time you connect to a network, whether you’re plugging in a cable or hopping on Wi-Fi, a few core components are working together behind the scenes. Think of them as the fundamental grammar of digital communication. Without these basic building blocks, the instant connectivity we take for granted just wouldn't happen.
Let's start with the classic wired connection. For decades, the backbone of most wired networks has been Ethernet. It completely changed how computers talk to each other inside an organization. What began as a pretty poky 2.94 Mbps connection back in 1973 quickly evolved, becoming the global standard that now delivers the mind-boggling speeds we rely on today.
The Roles of Switches and Routers
In any wired setup, two key devices are directing the flow of data: switches and routers. It’s easy to mix them up, but they have very different jobs.
-
A switch is the traffic cop for your local network. It knows exactly which device is plugged into each of its ports and sends data directly to the right destination. This keeps communication efficient and prevents data from getting sent to every device on the network.
-
A router, on the other hand, is the gateway to the outside world. It connects your entire local network to other networks, most importantly, the internet. Think of it as the on-ramp to the information superhighway.
Understanding the essentials of a router and modem setup is crucial, as these devices are the very first step in getting any network online.
Shifting to the Wireless World
Now, let's talk about the wireless networking most of us use every day: Wi-Fi. Instead of physical cables, Wi-Fi uses radio waves to send and receive data. The star of this show is the access point (AP), the device that actually creates your wireless network.
When you pull out your phone and see a list of nearby Wi-Fi options, you're seeing their SSIDs (Service Set Identifiers). These are just the public names for each network, like "Airport_Free_WiFi" or "My_Office_Network."
Behind the scenes, these networks operate on different channels, which are like invisible lanes in the air. Using different channels helps prevent signals from interfering with each other, ensuring a more stable and reliable connection for everyone.
This is especially critical in crowded places like Education campuses or busy Retail venues. That's why top-tier hardware from providers like Cisco and Meraki is designed to manage these channels automatically, always hunting for the clearest signal to give you the best performance.
The decision between a wired or wireless connection often comes down to balancing speed, reliability, and convenience. Here's a quick comparison to make it clearer:
Wired vs Wireless Networking at a Glance
| Feature | Wired (Ethernet) | Wireless (Wi-Fi) |
|---|---|---|
| Speed | Consistently faster and more stable | Slower, susceptible to interference |
| Reliability | Very high; not affected by other signals | Can be unstable due to walls, distance, other devices |
| Mobility | None; tied to a physical cable | High; freedom to move within the coverage area |
| Security | More secure due to physical connection | Less secure; requires strong encryption (WPA2/WPA3) |
| Installation | Can be complex and costly (running cables) | Simple and easy to set up |
| Best For | Desktops, servers, gaming consoles | Laptops, smartphones, tablets, IoT devices |
Ultimately, most modern venues use a hybrid approach—a wired backbone for reliability and a robust wireless network for user mobility and convenience.
Powering Modern Guest and Corporate Wi-Fi
In environments from bustling corporate offices supporting BYOD (Bring Your Own Device) to schools and retail stores, a great wireless experience is no longer a luxury—it's an expectation. This is where powerful hardware and smart software come together. A solid network built on Meraki access points can handle hundreds of people connecting at once without breaking a sweat.
This powerful foundation is what makes modern Authentication Solutions possible. It's the starting point for setting up a secure guest wifi network with a Captive Portal for social login or deploying advanced security protocols like IPSK and EasyPSK. These building blocks—switches, routers, and access points—are the essential stage on which all of today’s advanced networking features perform.
How Smart Networks Organize and Direct Traffic
Now that we have the physical hardware in place—the switches, routers, and access points—it's time to add the intelligence. A network isn't just about plugging things in. It’s about creating a smart, organized, and secure environment where data can travel efficiently. This is where software and logical rules come into play, turning a simple connection into a powerful business tool.
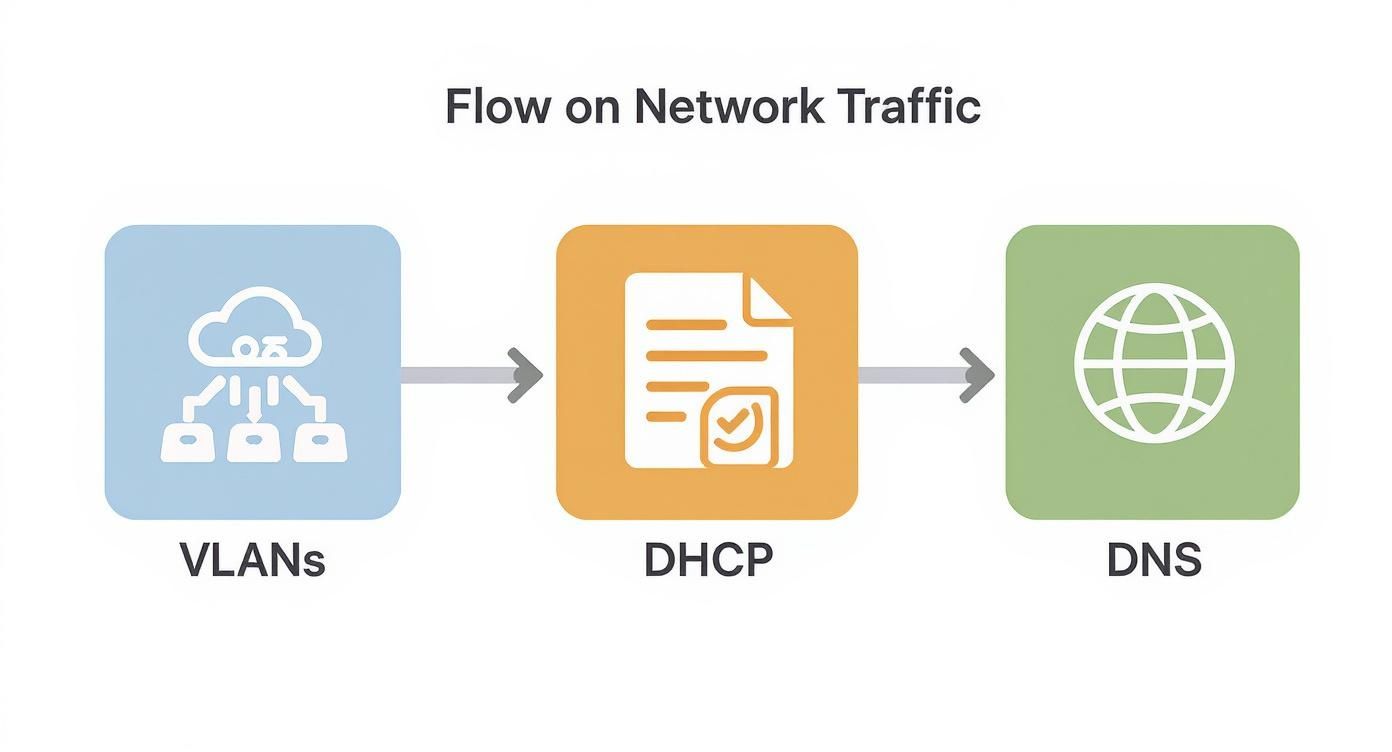
Think of it like building a new highway. You've laid the asphalt (the hardware), but now you need to paint the lanes, install traffic lights, and post road signs to prevent total chaos. In networking, concepts like VLANs, DHCP, and DNS do exactly that, making sure traffic gets where it needs to go quickly and safely. This level of organization is absolutely critical for handling the demands of modern Wi-Fi in Education, Retail, and BYOD Corporate sectors.
Creating Digital Lanes with VLANs
Imagine a busy school with students, teachers, and guests all on the same Wi-Fi. You definitely wouldn't want a student's device on the same slice of the network as sensitive administrative data. This is precisely the problem that VLANs, or Virtual Local Area Networks, solve.
A VLAN acts like a digital divider, splitting a single physical network into multiple, separate virtual ones. Even though everyone is connected to the same hardware, the VLANs keep their traffic in its own dedicated lane.
- VLAN 10: Could be for students, with limited access to certain websites.
- VLAN 20: Could be for faculty, with full access to internal servers and printers.
- VLAN 30: Could be a secure guest wifi network, completely walled off from the internal school network.
This segmentation is a cornerstone of good network security. Platforms like Cisco Meraki make creating and managing VLANs incredibly simple through a cloud dashboard, letting IT staff secure a network in just a few clicks. The ability to dynamically organize traffic is a game-changer, powered by a concept called software-defined networking. For a deeper dive, check out our guide on what software-defined networking is.
Automatically Assigning Addresses with DHCP
Once a device joins the correct VLAN, it needs an address to communicate, just like every house on a street needs its own mailing address. Manually assigning an IP address to every single phone, laptop, and tablet would be an absolute nightmare, especially in a busy BYOD environment.
This is where the Dynamic Host Configuration Protocol (DHCP) saves the day. Think of DHCP as the network's automated receptionist.
When a new device connects, the DHCP server automatically assigns it a temporary, unique IP address from an available pool. The process is completely seamless, allowing users to get online without any manual setup.
This automation is essential for a smooth guest wifi experience. When a customer connects to a retail store's network for a social login, DHCP ensures their device gets an address immediately, paving the way for the Captive Portal to appear.
Translating Names into Numbers with DNS
So, your device has an address and is in the right lane. Now you want to visit a website. You type "google.com" into your browser, but computers don't understand names—they only speak in numerical IP addresses.
The Domain Name System (DNS) is basically the internet's phone book. It takes the human-friendly website name you type and translates it into the machine-readable IP address. This all happens in the blink of an eye, every single time you browse the web. Without DNS, we'd all be stuck memorizing long strings of numbers for every site we wanted to visit.
Together, VLANs, DHCP, and DNS are the logical foundation of any well-run network. They work silently in the background, often managed by systems like Meraki, to make complex processes feel completely effortless. This intelligent traffic management is what enables secure and efficient Authentication Solutions, from simple social wifi access in a cafe to advanced IPSK and EasyPSK systems in a corporate setting.
The Digital Welcome Mat: Captive Portals and Authentication
We've covered the hidden nuts and bolts of networking—the hardware that gets you online and the rules that direct your data. Now, let's look at the very first thing a guest sees and interacts with when they join your Wi-Fi. This is the digital handshake, and it’s a critical piece of the puzzle.
This welcome mat has a name: the Captive Portal. You've seen them a hundred times. It’s that page that pops up at a hotel, airport, or coffee shop, asking you to agree to terms, provide an email, or log in before you get full internet access.
For any business, especially in Retail or hospitality, a captive portal is way more than just a login screen. Think of it as the digital front door to their physical space. It's a prime branding opportunity, a legal checkpoint for getting users to agree to your terms, and a gateway for understanding who is visiting your venue.
The diagram below shows how a user's device gets to this welcome page in the first place.
As you can see, the device is first guided into the right network lane (VLAN), given a temporary address (DHCP), and then uses the internet's address book (DNS) to be directed straight to the captive portal.
From Simple Logins to Secure Authentication
A basic "click-to-connect" portal might be fine for a small café, but different environments demand different levels of security and user verification. This is where modern networking gear from brands like Cisco and Meraki really comes into its own, supporting a whole range of authentication methods.
For a deeper dive into the mechanics, you can explore this overview of how a modern Wi-Fi captive portal operates.
Choosing the right way for users to log in depends entirely on your goals—whether you’re offering quick access at a shopping centre or securing a corporate network.
Guest Wi-Fi Authentication Methods
Here’s a quick comparison of the most common ways to grant Wi-Fi access.
| Authentication Method | How It Works | Best For | Key Benefit |
|---|---|---|---|
| Social Login | Users connect using existing social media profiles like Facebook, Google, or LinkedIn. | Retail, hospitality, public venues. | Gathers valuable, anonymised demographic data while giving users fast access. |
| Email/Form Fill | Users provide their name, email, or other details via a simple form to get online. | Marketing-focused businesses, event venues. | Builds a marketing contact list and helps you understand your customer base. |
| Voucher/Access Code | Pre-generated, unique codes grant access for a limited time. | Hotels, conference centres, paid Wi-Fi hotspots. | Provides controlled, temporary access that's easy to manage and monetise. |
| Identity PSK (IPSK) | Each user or device is assigned its own unique Wi-Fi password. | Corporate BYOD, schools, long-stay housing. | Blends password simplicity with individual user security and accountability. |
| SAML/Azure AD | Users authenticate against a corporate directory (like Microsoft Azure AD). | Enterprise environments, corporate offices. | Offers the highest level of security by leveraging existing company credentials. |
Each method provides a different balance of convenience, security, and data-gathering potential, making it crucial to pick the one that fits your organisation's needs.
A Smarter Password: Introducing Identity PSK (IPSK)
For any organization juggling a Bring-Your-Own-Device (BYOD) policy, managing network access is a constant headache. Handing out a single, shared Wi-Fi password is a huge security risk—when one person leaves, you have to update the password for everyone, which rarely happens.
This is where IPSK, or Identity Pre-Shared Key, is a game-changer. It’s a brilliant solution that combines the ease of a simple password with the robust security of individual accounts.
With an IPSK system (often called EasyPSK), every single user and their devices get a unique, private password to access the network.
- In a school: Every student gets their own key. When they graduate, you just revoke that one key. Simple.
- In an office: An employee’s laptop and phone each get their own key. If a device is lost or the employee leaves, you can cut off access instantly without affecting anyone else.
This approach massively boosts security without the overhead of complex enterprise authentication systems. It makes managing a BYOD Corporate or Education network infinitely simpler and safer. You know exactly who and what is connected at all times—a massive leap from the old "one password for all" method.
Bringing It All Together with Cisco Meraki
So, we’ve covered a lot of ground—from the layers of the OSI model to the nitty-gritty of VLANs and captive portals. Now it’s time to see how all these pieces come together in the real world. This is where a solution like Cisco Meraki comes into play, taking all those complex networking principles and making them surprisingly straightforward to manage.
The real magic behind Meraki is its cloud-based dashboard. Instead of plugging into switches, routers, and access points one by one, you can manage an entire network—even one that spans the globe—from a single web browser. This has completely changed the game for organizations in Education, Retail, and BYOD Corporate sectors.
The Power of Cloud-Managed Networking
Cloud management means that tasks that once demanded an on-site technician can now be handled from anywhere. Need to launch a new guest wifi network for a pop-up shop? You can get it done in minutes. Have to reconfigure VLANs across an entire school district? It’s just a few clicks.
This shift to the cloud makes sense when you consider the internet's explosive growth. In the early 1990s, it was a niche academic tool. By 2007, it was carrying over 97% of all telecommunicated information. Fast forward to today, with over 5 billion people online, and the demand for simple, scalable networking has never been higher. If you're interested, you can dive into the internet's incredible growth story to see how it paved the way for modern cloud solutions.
The Cisco Meraki platform was built for this scale. It provides a bird's-eye view of your entire network, freeing up IT teams to focus on improving the user experience instead of just keeping the lights on.
Tailoring the Wi-Fi Experience for Any Sector
What makes a cloud-managed system so powerful is its flexibility. A single platform can deliver totally different Authentication Solutions tailored to the specific needs of each environment.
-
For Retail: A clothing store can set up a slick, branded Captive Portal for social wifi. Customers log in with their Facebook or Google accounts, giving the business valuable demographic data in exchange for a smooth connection.
-
For Education: A university needs layers of security. It might use a secure IPSK (or EasyPSK) system for its BYOD environment, giving every student and staff member their own unique, private key to access the network.
-
For BYOD Corporate: An office can tie its Wi-Fi authentication directly into its employee directory. This is security at its best—network access is linked to an employee's active status and is instantly cut off the moment they leave the company.
Modern networking isn't just about providing an internet connection; it's about creating a secure, intelligent, and branded experience that aligns perfectly with an organization's goals.
This is where platforms like Splash Access come in, building on Meraki’s solid foundation to unlock its full potential. To get a better sense of how these systems work together, our guide explaining what Cisco Meraki is is a great place to start. This kind of integration enables even more sophisticated features, from running targeted marketing campaigns on your guest wifi to gathering detailed analytics on foot traffic.
Ultimately, combining powerful hardware with intuitive software puts advanced networking within reach for everyone. It’s proof that you don’t need a huge IT department to build a world-class, secure, and user-friendly network.
Where to Go From Here
We’ve really covered some ground, haven't we? From networking basics all the way to crafting slick captive portals, you've seen how the essential pieces of a network fit together. My hope is that this friendly, conversational guide has demystified computer networking and shown you that it's all built on a logical, understandable foundation.
A well-built network is the unsung hero of modern business, quietly powering everything we do. This is especially true in sectors like Education, Retail, and corporate offices full of BYOD devices. Whether it’s a coffee shop offering guest WiFi via social login or a large venue using advanced authentication solutions like IPSK, the core principles we discussed are always at play.
The ultimate goal is always the same: create a secure, reliable, and frustration-free experience for every single user.
Mastering Your Network's Defenses
Building a network is one thing; keeping it safe is another. Now that you have this solid foundation, your next move should be to dive into security. A great place to start is with a practical framework to improve security posture to make sure the environments you create are as resilient as they are functional.
The magic of modern networking is its ability to hide complexity. It's about taking these foundational concepts and using smart tools to deliver an effortless experience to the end-user.
I highly recommend you continue exploring how platforms like Cisco Meraki can revolutionize how an organization manages its connectivity. When you pair your understanding of networking fundamentals with intuitive, powerful tools, you can build systems that don’t just work—they actively help the business succeed.
This is just the beginning of your journey. The world of networking is always evolving, offering endless opportunities to learn, build, and innovate.
Frequently Asked Questions About Computer Networking
Welcome to our FAQ section! This is where we’ll tackle some of the most common questions that come up when people first start digging into computer networking 101. Let's clear up some of those nagging questions and make sure you have a solid handle on these key ideas.
How Do Captive Portals Actually Work?
Think of a Captive Portal as the digital doorman for a guest wifi network. When you first connect, the network hardware—like a Cisco Meraki access point—catches your first attempt to go online. Instead of letting you go to Google or your email, it redirects you to a special web page first.
This page is where the interaction happens. It might ask you to agree to the terms of service, log in with a social wifi account, or pop in a password. Once you've done what it asks, the portal essentially tells the network, "This person is good to go," and grants your device full internet access.
Why Is IPSK Better Than a Single WiFi Password?
Handing out the same password to everyone is a huge security headache. IPSK, which you might also hear called EasyPSK, completely changes the game by giving every single user or device its own unique key. This is incredibly useful in BYOD Corporate and Education settings.
If a student leaves the school or an employee loses their phone, an IT admin can just deactivate that one specific key. The rest of the network stays completely secure, and you avoid the massive hassle of changing the password for hundreds of other people. It’s the perfect blend of simple access and strong, individual control.
That kind of granular control is crucial for managing any modern network. It's easily one of the most practical Authentication Solutions out there today.
Can I Use Social Login for My Business?
Definitely! Adding a social login option to your Captive Portal is a brilliant move, especially for businesses in the Retail space. It creates a win-win situation: your customers get onto the guest wifi quickly without the friction of creating yet another account, and you gain valuable (and anonymized) demographic insights about who is visiting your store. This kind of data can be gold for understanding your customer base and fine-tuning your marketing.
What Causes Most WiFi Connectivity Problems?
More often than not, Wi-Fi troubles trace back to two usual suspects: signal interference and network congestion. Interference can be caused by anything from your neighbor's Wi-Fi network to a running microwave or even just thick concrete walls. Congestion is what happens when too many devices are trying to talk over the same Wi-Fi channel at once—picture a traffic jam on the information superhighway.
Knowing the common causes is half the battle. If you're ready to dig deeper and start fixing things, our guide on resolving WiFi connectivity issues offers some great troubleshooting steps and solutions.
Ready to create a seamless, secure, and intelligent Wi-Fi experience for your users? Splash Access integrates with your Cisco Meraki hardware to deliver powerful captive portals, advanced authentication, and valuable analytics. Visit https://www.splashaccess.com to learn how we can help your business.