Think about managing a sprawling Wi-Fi network like trying to run an airport from a small, windowless room in the basement. You can't see what's happening on the runways or at the gates. This is what traditional, on-premise network management feels like—a bit disconnected and clunky.
Now, imagine yourself in the main control tower, surrounded by panoramic windows showing you everything in real-time. That's the essence of cloud-based network monitoring. It takes your command center out of a cramped server closet and puts it in the cloud, giving you a complete, 360-degree view and control from anywhere on the planet. It’s a friendly, smarter way to run your network.
Your Network's Digital Command Center
At its core, cloud-based network monitoring is simply the practice of managing your entire network infrastructure—all your routers, switches, and access points—from a centralized, web-based dashboard. It ditches the need for on-site hardware and software controllers. This approach is the brains behind modern, intelligent Wi-Fi, especially when it’s running on powerful hardware from vendors like Cisco Meraki. It’s less about physical boxes and blinking lights and more about smart, agile, remote management.
This fundamental shift makes life so much easier. Instead of sending an IT tech to a branch office to fix a problem, you can diagnose issues, push security updates, or see how people are using the network, all from a single pane of glass. It’s a game-changer, turning what used to be a reactive, break-fix chore into a proactive, strategic advantage. If you're still on the fence, digging into the key differences between cloud and server-based systems is a crucial first step. Learn more about cloud vs. server infrastructure.
From Basic Connectivity to Intelligent Experiences
The real magic happens when you pair this cloud management with sophisticated authentication solutions. This is where a simple Wi-Fi signal evolves into a secure, seamless, and engaging experience for every user. It’s particularly powerful in busy environments like Education, Retail, and BYOD Corporate sectors, where lots of different people connect every day.
Just look at these real-world examples:
- Education: A university can manage Wi-Fi for thousands of students and faculty across a sprawling campus, ensuring everyone has secure, reliable access from their dorm room to the lecture hall.
- Retail: A chain of coffee shops can offer branded guest Wi-Fi through custom captive portals, gathering valuable customer feedback or building marketing lists through social login options.
- BYOD Corporate: An office can safely allow employees to connect their personal devices (BYOD) by giving each person a unique network key using methods like IPSK (Individual Pre-Shared Key) or EasyPSK.
This isn't just a technical upgrade; it's a completely new way to interact with the people who use your network. You're creating a secure, branded, and data-rich environment for every single person who connects.
Ultimately, cloud-based network monitoring goes far beyond just keeping the internet running. It’s about knowing who is on your network, understanding what they’re doing, and using that insight to give them the best, most secure experience possible. By integrating tools like social Wi-Fi and custom captive portals, you transform your network from a cost center into a powerful tool for customer engagement, security, and business intelligence—all managed effortlessly from the cloud.
Why Smart Businesses Are Moving Network Management To The Cloud
The days of housing your network’s brain in a dusty server closet are quickly fading. Smart businesses are making a strategic shift, moving their entire network management operations to the cloud—and for good reason. It’s not just about chasing the latest tech trend; it's a fundamental change that unlocks agility, security, and powerful user insights.
This move is reshaping how organizations operate across all kinds of sectors. Imagine a university campus on the first day of the semester. With a traditional setup, the IT team would be scrambling to handle the sudden surge of thousands of students connecting their devices. With cloud-based network monitoring, the system scales effortlessly, ensuring a smooth and secure onboarding for everyone without a single on-site adjustment.
Or think about a national retail chain. From a single dashboard, they can instantly update guest Wi-Fi promotions across hundreds of stores. This level of centralized control turns a simple internet connection into a dynamic marketing tool, driven by technologies like custom captive portals and social wifi logins.
The Power of Accessibility and Scalability
One of the biggest draws is the sheer freedom cloud management provides. Your IT team is no longer tethered to a physical location. They can monitor network health, troubleshoot issues, and adjust security policies for a corporate BYOD environment from anywhere with an internet connection. This is a huge deal for organizations with multiple branches or a growing remote workforce.
The scalability is just as compelling. Adding a new office, expanding a retail floor, or opening a new school building doesn't mean a massive hardware overhaul. You simply adjust your resources in the cloud, often with just a few clicks. This allows your network to grow with your business, not hold it back.
By moving to the cloud, you're not just upgrading your technology—you're future-proofing your operations. You gain the ability to adapt to changing business needs on the fly, a crucial advantage in any industry.
Driving Cost Efficiency and Smarter Security
Let's talk about the bottom line. On-premise hardware is expensive. It requires a big upfront investment, ongoing maintenance, and eventual replacement. A cloud-based approach, especially one powered by reliable Cisco Meraki hardware, flips that model, getting rid of those capital costs in favor of a predictable subscription.
This shift is part of a much larger market trend. The global network monitoring technology market was valued at USD 2.78 billion in 2025 and is projected to hit USD 4.75 billion by 2033. Cloud adoption is a primary driver here, with SaaS dashboards growing at a remarkable 12.4% CAGR as businesses recognize the value of real-time insights without the hardware headache.
Security also gets a major boost. Cloud platforms centralize your defenses, making it much easier to deploy advanced authentication solutions. Instead of a single, easily compromised password, you can implement IPSK or EasyPSK to give each user or device a unique key. This granular control is a game-changer for securing sensitive data in education and corporate environments. When considering the strategic advantages of cloud network management, it's beneficial to understand the broader landscape of essential IT services for startups.
Ultimately, this transition frees up your IT team from the mundane work of maintenance, allowing them to focus on projects that truly drive the business forward. Exploring the reasons why cloud-managed IT is the future can provide even more clarity on this strategic shift. The move to cloud-based network monitoring is more than an upgrade—it's a smarter, more efficient, and more secure way to manage your digital backbone.
Pairing Cisco Meraki With A Powerful Cloud Platform
Think of your Cisco Meraki hardware—those high-performance access points—as a world-class orchestra. Each instrument is perfectly tuned and capable of incredible things. But without a conductor, all you get is noise. A dedicated cloud management platform is that conductor, turning raw potential into a seamless, harmonious experience for every user.
Cisco Meraki is well-known for its cloud-managed hardware, which provides the smart foundation for any modern network. Its native dashboard is fantastic for handling the nuts and bolts: device status, firmware updates, and basic traffic analysis. The real magic, however, begins when you layer a specialized management platform on top. This is what truly unlocks the full power of your cloud-based network monitoring.
This combination is what lets you build dynamic captive portals, slick social Wi-Fi logins, and advanced authentication solutions. It elevates your network from a simple utility that just provides internet access into a rich, data-driven ecosystem. If you're new to this world, understanding what Cisco Meraki is and its core functions is a great place to start.
The Foundation and The Finishing Touch
The Meraki dashboard is your solid foundation. It ensures the hardware is online, secure, and running as it should. A dedicated cloud platform like Splash Access, on the other hand, adds the finishing touches that create exceptional user experiences and unlock deeper business insights. It takes the raw data and control from Meraki and refines it into actionable intelligence and powerful engagement tools.
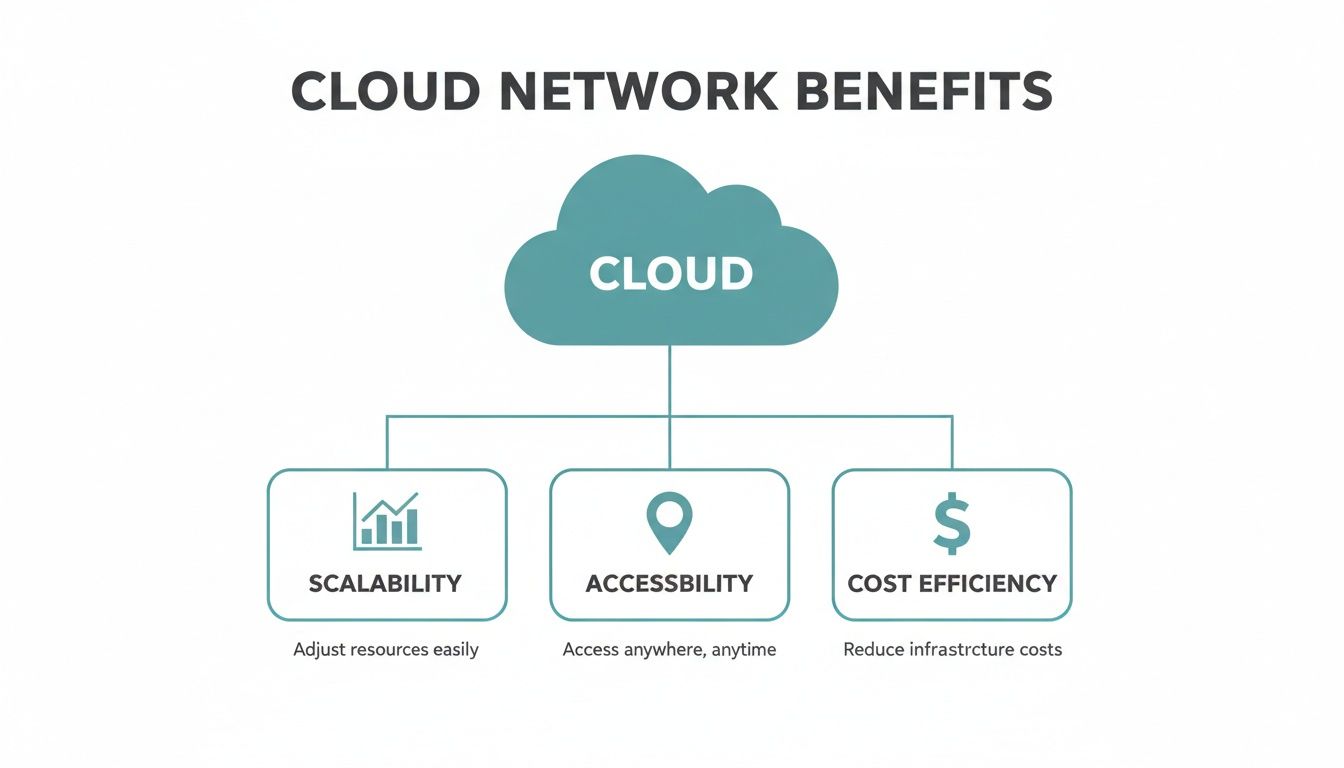
This hierarchy unlocks three core benefits: scalability, accessibility, and cost-effectiveness.
As you can see, this model allows your network to grow without friction, be managed from anywhere, and reduce long-term operational costs—all critical for dynamic environments.
On-Premise vs Cloud-Based Network Monitoring
To truly grasp the shift, it helps to compare the old way of doing things with the new cloud-based approach. For years, network monitoring was a clunky, on-site affair. Today, the cloud offers a flexibility that on-premise solutions just can't match, especially for organizations with multiple locations like retail chains, school districts, or corporate campuses.
The table below breaks down the key differences.
| Feature | Traditional On-Premise Monitoring | Cloud-Based Monitoring (with Cisco Meraki & Splash Access) |
|---|---|---|
| Initial Setup & Cost | High upfront investment in servers, software licenses, and specialized IT personnel for setup. | Minimal upfront cost with a subscription-based model. No on-site hardware to purchase or maintain. |
| Scalability | Difficult and expensive. Adding new locations or more devices requires purchasing more hardware. | Effortless. Scale up or down on demand by simply adjusting your license count. |
| Accessibility & Management | Management is tied to the physical location of the server, often requiring VPNs for remote access. | Manage your entire network from anywhere in the world with a web browser. Centralized dashboard for all locations. |
| User Experience | Limited to basic access. Customizing the user journey is often complex or impossible. | Create branded captive portals, social logins, and targeted marketing campaigns directly from the platform. |
| Security & Updates | IT team is responsible for all patching, security updates, and maintenance, which can be a drain on resources. | All software updates, security patches, and new features are handled automatically by the cloud provider. |
| Data & Analytics | Provides raw network data (e.g., bandwidth usage), but getting business insights is a manual process. | Rich analytics on user behavior, demographics, and visit patterns. Turns network data into business intelligence. |
In short, the cloud model takes the burden of infrastructure management off your shoulders, freeing up your team to focus on strategic initiatives and improving the end-user experience.
Tailoring Access for Every Sector
This two-layered approach is incredibly effective across different industries because it allows for deep customization. The needs of a university campus are worlds apart from those of a retail store or a corporate office, and this partnership handles them all beautifully.
Here’s how this powerful pairing works in practice:
- Education Sector: A university can use Meraki for robust campus-wide coverage while a cloud platform manages thousands of student connections. It can deploy EasyPSK to give each student a unique key for their devices in the dorms, ensuring secure and simple access for the entire academic year.
- Retail Environments: A shopping center can use its guest Wi-Fi as a marketing engine. The captive portal can be customized with branding and special offers, while social login options help build a valuable customer database for future promotions.
- BYOD Corporate Settings: In a modern office where employees bring their own devices, security is non-negotiable. This system allows for the easy deployment of IPSK (Individual Pre-Shared Key) solutions. Every employee gets a personal network key, and if they leave the company, their access can be revoked in seconds without affecting anyone else.
This partnership moves beyond simple connectivity. It’s about creating a secure, intelligent, and branded digital front door for your organization, tailored to the specific needs of your users.
The Meraki hardware provides the reliable "how" of network connectivity, while the cloud platform provides the strategic "why" and "what" of user engagement and security. It's this combination that truly defines modern cloud-based network monitoring, turning a background utility into a frontline asset for engagement and security.
Bolstering Your Network With Smarter Authentication
In a world where "Bring Your Own Device" (BYOD) is the norm and public Wi-Fi is an expectation, strong security isn't just a feature—it's a necessity. This is where cloud-based network monitoring really proves its worth, going beyond basic connectivity to build up your network’s defenses with smarter, more detailed authentication solutions.
Think about the old way of securing Wi-Fi: a single, shared password for everyone. It's like giving every resident in a huge apartment building the same key to the front door. If one person loses that key, the entire building is suddenly vulnerable. That model is dangerously outdated for a busy retail center, a sprawling university education campus, or a modern corporate office.
Instead, today's authentication methods create a much tougher line of defense. The goal is to verify and authorize every single connection, building a secure gateway that knows exactly who is connecting, from what device, and what they should be allowed to access.
Moving Beyond the Shared Password
Advanced authentication takes powerful security protocols that were once a nightmare to set up and makes them accessible. Two of the most important technologies driving this shift are IPSK (Individual Pre-Shared Key) and its even simpler version, EasyPSK.
The concept is simple but powerful: give every user or device its own unique, personal key to the network. This completely changes the game for both security and day-to-day management, especially in places with lots of users.
- For Corporate BYOD: A new employee gets a unique key for their personal devices. When they leave the company, you just revoke their specific key. Their access is gone instantly, and nobody else on the network is affected.
- For Education: You can assign each student their own key that works for the entire school year. This stops password sharing in its tracks and makes sure only registered students get onto the campus network.
By assigning individual keys, you eliminate the widespread risk of a compromised shared password. It's like changing the lock for one person without having to re-key the entire building.
This level of precise control is made incredibly simple when a cloud management platform works with your Cisco Meraki hardware. What used to be a massive IT project is now a quick, automated task. For those wanting to explore even more robust security frameworks, you can learn about options like 802.1X authentication to see the full spectrum of network protection available.
Your Captive Portal: The Digital Front Door
Your captive portal is much more than a simple login screen. It's the first impression of your network and a critical security checkpoint. By acting as a secure gateway, it forces users to identify themselves before they can get online.
This is your opportunity to offer secure and convenient login options. For instance, social login (often called social wifi) lets guests in a retail store or mall connect using their existing social media accounts. Not only does this make it easier for them to get online, but it can also provide you with valuable, consent-based demographic data for your marketing.
The connection between strong authentication and cloud monitoring is essential for keeping a business running smoothly. For retail shopping centers, security monitoring is a huge part of data center revenue, which is crucial for defending against costly breaches. By integrating tools like a billing gateway and social Wi-Fi, businesses can avoid the kind of downtime that cripples operations, even with high-availability SLAs in place.
Ultimately, these layers of authentication, all managed from the cloud, give you a complete picture of who is on your network. Whether it’s a student at a university, a shopper at the mall, or an employee using their own laptop, you have total visibility and control. This approach turns your Wi-Fi from a simple utility into a secure, intelligent, and fully managed asset.
Tailoring the Perfect Guest Wi-Fi Experience for Your Industry
Long gone are the days of a generic, one-size-fits-all Wi-Fi login. Today, a modern cloud based network monitoring platform gives you the power to create a secure and memorable guest Wi-Fi experience for any industry. It's about turning a simple connection into a real tool for customer engagement.
When you pair reliable hardware like Cisco Meraki with an intelligent management layer, the possibilities really open up. Let's look at a few real-world examples to see how different sectors can tailor the guest experience using custom captive portals and smarter authentication solutions.
Transforming Retail With Social Wi-Fi
For any retail business, guest Wi-Fi is an absolute goldmine. Instead of just offering a basic connection, you can use a custom captive portal to greet shoppers with your latest promotions, ask for quick feedback, or invite them to join your loyalty program.
One of the most effective strategies is using social login, or social wifi. By letting customers connect using their social media profiles, you make their lives easier while gathering valuable, consent-based demographic data. With that information, you can:
- Build Marketing Lists: Automatically add new email addresses to your newsletter.
- Deliver Targeted Offers: Send exclusive discounts right to a shopper's phone as they browse.
- Understand Customer Behavior: Analyze foot traffic and dwell times to optimize your store layout and staffing.
Suddenly, your Wi-Fi network shifts from a cost center to a direct marketing channel. If you're wondering where to start, this complete walkthrough shows you how to set up guest wifi for your business.
Securing the Modern Education Campus
The education sector has a unique challenge: managing thousands of users—students, faculty, and guests—each with different access needs across a sprawling campus. A single, shared network is neither secure nor practical. Cloud management makes creating distinct, secure networks for each group straightforward.
For students, especially in dorms, security and ease of use are everything. This is where solutions like EasyPSK become essential.
Instead of a single password for an entire dorm that gets passed around, EasyPSK gives each student a unique, personal key for all their devices. This stops unauthorized access in its tracks and makes life much easier for the IT staff. If a student’s device is ever compromised, their key can be instantly revoked without disrupting anyone else.
This kind of complexity is driving the rapid growth of the cloud network performance monitoring market. Valued at USD 1.2 billion in 2024, it's projected to hit USD 3.5 billion by 2033, growing at a 12.5% CAGR. The demand for speed is also clear, with the 40 Gbps bandwidth segment holding over a 35% share in 2023—a testament to the need for powerful cloud solutions in dense environments like universities. You can find more insights about this growing market on verifiedmarketreports.com.
Impressing Visitors in a BYOD Corporate World
In a corporate setting, your guest Wi-Fi experience says a lot about your professionalism. A clunky, insecure login process leaves a bad first impression. At the same time, with "Bring Your Own Device" (BYOD) policies now the norm, the network must be carefully segmented to protect sensitive company data.
A cloud based network monitoring platform is the perfect answer. You can create a seamless and secure guest network that is completely walled off from your internal corporate network. This is often done with advanced authentication solutions like IPSK.
Here’s how it works:
- Seamless Guest Onboarding: Visitors can get temporary, unique access keys, or the system can integrate with tools like Azure AD for authentication, providing a professional and secure login.
- Robust BYOD Security: Employees can be issued their own IPSK keys for their personal devices. This ensures every device on the network is accounted for and authorized, which dramatically reduces security risks.
- Complete Network Separation: The cloud dashboard lets you enforce strict policies that keep guest traffic completely separate from internal resources, ensuring visitors get online without ever touching your critical systems.
From retail stores to university campuses and corporate offices, tailoring the guest Wi-Fi experience is no longer just a nice perk. It’s a strategic move for better security, engagement, and operational excellence.
Answering Your Questions About Cloud Network Monitoring
Making the jump to a cloud-managed network is a significant move, so it's smart to have questions. You need to know you're choosing the right path for your business. Let's tackle some of the most common questions we hear about cloud based network monitoring and what it actually looks like day-to-day.
Think of this as a quick FAQ to clear up any lingering doubts. We’ll give you straight answers so you feel confident about how this technology will fit into your organization, whether you're running a retail store, a school campus, or a corporate office.
What Is A Captive Portal And How Does It Work?
A captive portal is that branded login page you see when you connect to public Wi-Fi at a coffee shop or airport. It's your network's digital welcome mat and your first, best chance to make an impression. It's also a critical piece of the security and user experience puzzle.
From a cloud platform, you can control every aspect of this portal from anywhere. You can add your logo, a welcome message, a special offer, or your terms of service. The portal works hand-in-glove with your Cisco Meraki hardware, intercepting any new device that tries to connect. It presents this login page before letting anyone online, ensuring every user authenticates in a way you've defined. This creates a secure, branded, and incredibly valuable onboarding process.
How Is IPSK More Secure Than A Single Wi-Fi Password?
Using a single Wi-Fi password for everyone is like having one master key for an entire building. If one person loses that key, the entire building is compromised. That's a massive risk for any busy environment. IPSK (Individual Pre-Shared Key), especially with easy-to-use solutions like EasyPSK, flips this model on its head by giving each person or device its own unique key.
This boosts your security immensely. Just think about it:
- Corporate BYOD: When an employee leaves the company, you just revoke their personal key. No one else is affected, and you don't have to change the password for the entire office.
- Education Campus: Every student gets a unique key for their laptop and phone that's valid for the school year. Once they graduate, their access is simply turned off.
This level of granular control means a single compromised key no longer puts the whole network at risk. It’s like changing just one person's lock instead of re-keying the entire building—a far more practical and secure authentication solution for any dynamic setting.
Can I Connect Social Wi-Fi To My Marketing Tools?
Yes, you absolutely can. This is where a cloud based network monitoring system truly shines as a business growth engine. Modern captive portals are built with these integrations in mind. When you offer social Wi-Fi (also called social login), you let guests log in using their social media accounts.
With their consent, this gives you powerful demographic insights. Better yet, you can link this data directly to your marketing platforms. For instance, when a customer logs into your retail store's guest wifi, their email can be automatically sent to your CRM or newsletter list. This allows you to build a relationship and keep the conversation going long after they’ve left the store, turning a simple Wi-Fi connection into a powerful marketing channel.
Ready to see how a powerful, cloud-managed Wi-Fi experience can transform your business? Splash Access provides an all-in-one platform that works seamlessly with your Cisco Meraki hardware to deliver secure, engaging, and intelligent Wi-Fi for any industry. Start your free trial today.