Hey there, network manager! You live and breathe one core mission: keeping everyone safely and reliably connected. It’s a constant balancing act, right? That’s precisely where access point management steps in. Think of it as the central command center for your entire wireless network—the system that turns potential chaos into seamless, secure connectivity for everyone.
What Is Access Point Management Anyway?
Imagine you’re an air traffic controller for your Wi-Fi. Your job is to guide all the data flying through the air, prevent collisions, and make sure every device gets to its destination quickly and safely. Without a central tower, you’d be trying to direct each plane by hand. It would be a disaster.
That’s what managing individual access points (APs) one by one feels like, especially as your network grows. It’s inefficient, frustrating, and a recipe for errors.
Proper access point management gives you a single, unified view of your entire wireless world. Instead of logging into dozens (or hundreds) of separate devices, you get one friendly dashboard to monitor network health, tweak settings, and push out updates. This is where modern platforms from providers like Cisco Meraki really prove their worth, transforming a huge headache into a smooth, manageable operation.
Beyond Just Connectivity
Today, managing access points is about much more than just beaming out a Wi-Fi signal. It's about building intelligent, secure, and user-aware networks that are fine-tuned for their specific environment. The needs of a university campus in the Education sector are worlds apart from those of a Retail store or a BYOD Corporate office.
A well-managed network isn't just a utility; it's a strategic asset. It can boost customer engagement in a shop, power digital learning in a classroom, and lock down sensitive data in an office.
For example, a retailer can use Captive Portals to offer guest Wi-Fi in exchange for an email address, turning a simple connection into a valuable marketing tool. A school, on the other hand, has to juggle thousands of student devices at once while maintaining a safe and secure browsing environment.
Securing the Modern Network
Let's be honest: security is the most critical piece of the puzzle today. A single, shared Wi-Fi password just doesn't cut it anymore, especially when personal devices are accessing corporate data in a BYOD Corporate world.
This is where sophisticated authentication solutions come into play. Instead of a one-size-fits-all password, you can deploy smarter, more secure methods:
- Captive Portals: These create a secure, branded login page for guests, keeping their traffic completely separate from your internal network.
- IPSK (Identity Pre-Shared Key) or EasyPSK: This brilliant solution assigns a unique, private password to every single user or device, giving you incredible control.
Integrated into platforms from companies like Cisco, these tools give you incredibly granular control. When an employee leaves or a device is lost, you can just disable its individual key without having to change the password for everyone else. It’s a fundamental shift, moving Wi-Fi security from a static, vulnerable password to a dynamic, identity-based defense.
Why Centralized Control Is a Game Changer
Let's get real for a minute. Why is a centralized system for your access points so important?
Think about managing the Wi-Fi for a sprawling university campus, a multi-story office building, or a dozen retail locations. Now, imagine having to physically log into every single access point just to push a firmware update, change a password, or troubleshoot a connection. It’s a logistical nightmare waiting to happen.
This one-by-one approach isn't just painfully slow; it’s a breeding ground for human error and inconsistency. A single misconfigured AP can easily open up a security hole or create a frustrating Wi-Fi dead zone, leading to a flood of complaints and support tickets.
This is exactly where centralized access point management comes in and saves the day. Modern cloud-based platforms, like those from Cisco Meraki, take all that chaos and streamline it into a single, unified command center. From one dashboard, you can see everything: the health of your network, who's connected, and any potential threats, all in real time.
From Reactive Firefighting to Proactive Strategy
Without a bird's-eye view, IT teams get stuck playing a constant game of whack-a-mole. They spend their days chasing down isolated issues reported by frustrated users, often without enough information to diagnose the root cause quickly. Centralized management completely flips that script.
Instead of waiting for something to break, you're now in a position to proactively monitor the entire wireless environment. You can instantly see which APs are getting slammed with traffic, identify sources of interference, and get alerts before a small glitch turns into a full-blown outage.
This proactive stance drastically cuts down on administrative overhead. It frees up your team to work on more strategic projects—like optimizing the network for new apps or beefing up security—instead of just putting out fires.
Simplified Security and Authentication
In an age of BYOD Corporate policies, strong network security isn't just a "nice-to-have," it's non-negotiable. A centralized platform makes implementing robust authentication solutions incredibly simple. Forget configuring each access point one at a time; now you can push network-wide security policies with just a few clicks.
This is a huge advantage for managing different user groups across various environments:
- Education: Easily create separate, secure networks for students, faculty, and guests. Each can have its own bandwidth limits and content filtering rules, all managed from one place.
- Retail: Roll out a public guest Wi-Fi network using a Captive Portal to engage customers, while keeping your critical point-of-sale systems on a completely separate and secure network.
- Corporate: Onboard new employee devices securely using advanced methods like IPSK or EasyPSK. These assign a unique security key to each user or device, so if a laptop is lost or an employee leaves, you can revoke its access instantly without affecting anyone else. To learn more, check out our guide on the role of security keys for Wi–Fi.
Centralized control means your security policy is applied uniformly everywhere, all the time. No gaps, no forgotten devices, and no single weak link that can compromise your entire network.
The Power of Scalability and Growth
As your organization grows, so will its demand for fast, reliable Wi-Fi. The need for better connectivity is exploding globally. The wireless access points market, valued at $5.23 billion, is on track to hit $5.75 billion, largely driven by the boom in IoT devices and the constant push for faster speeds.
A centralized system is built for this kind of expansion. Adding a new access point becomes as easy as plugging it in. The device automatically phones home to the cloud controller, downloads its configuration, and seamlessly joins the network.
This "zero-touch provisioning" means you can scale your network from ten APs to a thousand without a massive increase in your management workload. It’s a smart, future-proof investment that ensures your network is ready for whatever comes next.
Securing Your Network with Smart Authentication
A strong Wi-Fi signal is great, but it’s completely useless if your network isn't secure. In today's world, everyone from employees with company laptops to students on their personal phones expects to get online instantly. The old-school approach of a single password for everyone just doesn't cut it anymore; it's a massive security hole waiting to be exploited.
This is where smart access point management really proves its worth. It’s not just about boosting your signal—it's about creating intelligent, secure gateways to your network that don't drive your users crazy. We’re moving beyond that one shared password and into a much smarter, identity-based way of thinking about network security. Let's dig into how you can lock things down without sacrificing a smooth connection.
The Power of the Captive Portal
Ever connected to the Wi-Fi at a hotel, airport, or your favorite coffee shop? Then you’ve already used a Captive Portal. It’s that branded login page that pops up right after you connect, before you can actually start browsing. It might seem simple, but it's an incredibly powerful tool for managing network access, especially in places open to the public.
Think of a Captive Portal as a friendly gatekeeper. It temporarily stops a new device and asks the user to take an action—like agreeing to your terms of service, entering an email, or logging in with a social media account—before it opens the gate to the internet. This creates a crystal-clear line between your trusted internal users and any temporary guests.
This single feature is a game-changer for all sorts of organizations:
- Retail: A store can use its portal to flash a special discount or invite shoppers to join a loyalty program. Suddenly, your free Wi-Fi is a powerful marketing tool.
- Education: A university campus can make sure every guest user sees and agrees to the acceptable use policy before they hop on the network.
- Corporate: In a BYOD Corporate environment, it creates a secure, separate onboarding lane for visitors and contractors, keeping them far away from sensitive company data.
By funneling all guest traffic through this controlled entry point, you get to maintain tight security while offering a professional, branded experience. If you're interested in the nuts and bolts, you can learn more about how to set up guest Wi-Fi and put these tools to work.
Upgrading Security with Individual Keys
Captive Portals are perfect for guests, but what about your own team? Asking every employee to use the same shared password for their personal phones, tablets, and laptops is asking for trouble. If that one password gets out, your entire network is wide open.
This is where more advanced solutions like Identity Pre-Shared Key (IPSK) or EasyPSK come into the picture. The concept is simple. Instead of giving everyone the same master key to the building, you give each person their own unique key.
The big idea behind IPSK is straightforward but incredibly effective: one user, one device, one unique password. This completely changes your security, moving away from a single point of failure toward a highly specific, identity-based defense.
This approach, easily handled through platforms from providers like Cisco and Cisco Meraki, is a lifesaver. When an employee leaves the company, or if a device is lost or stolen, you don’t have to force a network-wide password change. You just log into your dashboard and disable the one key tied to that specific user or device.
Problem solved. It’s a massive headache lifted from IT admins. No more frantic password resets that disrupt dozens or even hundreds of other people. Everyone else stays connected without a hitch, and the security threat is gone in seconds. Whether you’re a busy school district in the Education sector or a security-focused corporate office, IPSK strikes the perfect balance between robust security and simple management. It's a cornerstone of modern, effective access point management.
Designing Wi-Fi for Your Unique Environment
When it comes to building a Wi-Fi network, a one-size-fits-all approach just doesn't work. The wireless demands of a packed high school are completely different from those of a quiet corporate office or a busy retail store. Real access point management isn’t about just throwing a signal everywhere; it's about carefully engineering a network that truly fits the unique needs of your space.
Think of it like setting up a sound system. A concert hall needs powerful speakers to fill the venue, while a small coffee shop requires something far more subtle. Your Wi-Fi network operates on the same principle. You have to account for user density, security policies, and the kind of experience you want people to have.
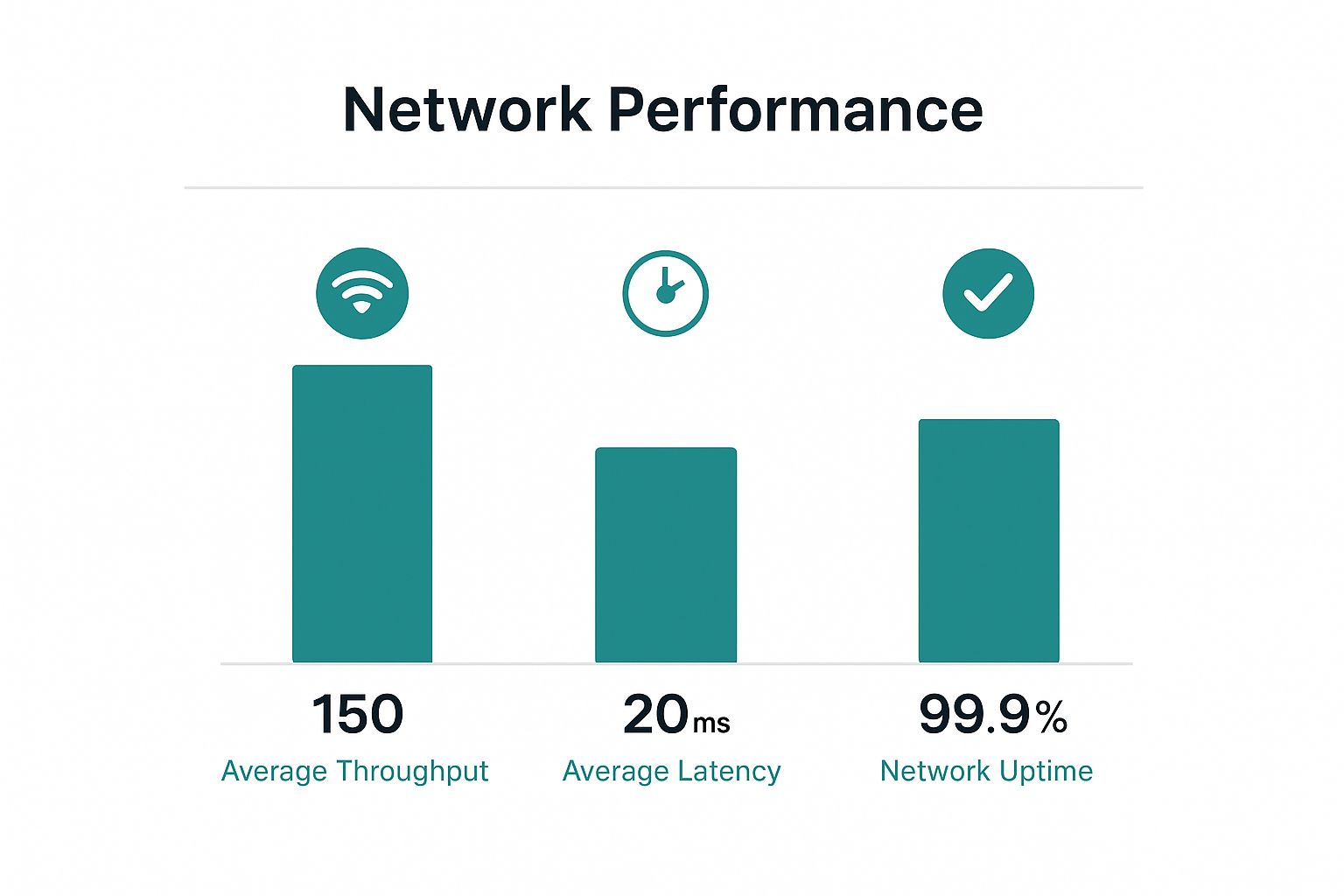
This infographic breaks down the key performance metrics that any well-designed, modern network should be hitting.
The goal is always high throughput and low latency with nearly perfect uptime. As you map out your Wi-Fi environment, remember that performance is everything. Learning about testing network latency accurately is a great step toward ensuring your deployment is solid from day one.
Different environments have vastly different priorities. For instance, a school is focused on security and capacity, while a retail store is all about guest experience and marketing. A corporate office? Their biggest concern is securing a flood of personal devices.
Wi-Fi Management Priorities by Sector
| Sector | Primary Challenge | Key Management Feature | Recommended Solution |
|---|---|---|---|
| Education | High-density classrooms and lecture halls with students connecting multiple devices at once. | Robust content filtering and per-user bandwidth controls to ensure fair and safe access. | Centralized management platforms like Cisco Meraki that can handle thousands of simultaneous connections. |
| Retail | Providing a seamless and secure guest Wi-Fi experience without compromising internal network security (e.g., POS systems). | A branded captive portal that authenticates users and doubles as a marketing tool. | Guest Wi-Fi with network segmentation, often managed through a Captive Portal with strong authentication. |
| Corporate BYOD | Securing the network against a wide array of personal employee devices (Bring Your Own Device). | Device-specific authentication and network segmentation to isolate personal traffic from sensitive corporate data. | Advanced authentication solutions like IPSK (Individual Pre-Shared Key) or EasyPSK. |
This table gives a quick snapshot of how needs change, but let's dig into the specifics for each.
Tailoring Wi-Fi for the Education Sector
Schools and university campuses are some of the toughest environments for Wi-Fi. Picture a lecture hall with hundreds of students all trying to connect their laptops, tablets, and phones simultaneously. It's a classic high-density scenario where network performance is absolutely non-negotiable.
The main goal here is twofold: provide reliable, high-speed access and maintain a safe, compliant online space. Access point management platforms from providers like Cisco Meraki give administrators the tools to implement content filtering, manage bandwidth for each user, and keep things running smoothly even when everyone logs on at once. It's all about balancing open access with tight control.
Connecting Customers in Retail
In the Retail world, guest Wi-Fi is no longer just a nice-to-have amenity—it’s a powerful engine for customer engagement. The biggest challenge is giving shoppers a seamless and secure connection without opening a backdoor to your internal systems, like the point-of-sale terminals.
This is where Captive Portals really shine. A well-crafted portal does more than just authenticate guests; it acts as a direct marketing channel. You can display promotions, collect emails for your newsletter, or point shoppers to your social media pages. This transforms a simple internet connection into a valuable marketing touchpoint.
Securing the BYOD Corporate World
Inside today's BYOD Corporate environment, the primary battle is securely onboarding a massive and diverse collection of personal devices. Every employee wants to connect their own smartphone and laptop, but each one of those devices is a potential entry point for security threats.
The core challenge in a corporate BYOD environment is segmentation. You must allow personal devices to be productive without ever letting them touch your sensitive company data.
This is where advanced authentication solutions like IPSK or EasyPSK become absolutely essential. Instead of a single, shared password that could easily leak, you can assign a unique password to each user and their specific devices. This technique, managed from a central dashboard like Cisco Meraki, lets IT teams slice and dice network traffic with surgical precision. Employee devices get the access they need, while critical company resources stay completely isolated and protected.
This kind of granular control is the bedrock of a secure, flexible, and manageable corporate network. The demand for such sophisticated connectivity is skyrocketing across all industries. In fact, the global wireless access point market is projected to grow from $17.20 billion to $32.31 billion, reflecting a major 8.2% CAGR. This boom is fueled by the adoption of faster standards like Wi-Fi 6 and Wi-Fi 7, which makes thoughtful, sector-specific network design more critical than ever.
What to Look For in a Modern AP Management Platform
Picking the right access point management platform can feel like a huge task, but it really comes down to one thing: finding a system that makes your job easier while giving users a flawless connection. A modern platform isn't just a signal-strength meter; it's the brain of your entire wireless operation. So, what features are non-negotiable?
It all starts with an intuitive dashboard. You shouldn’t need a network engineering degree just to see what’s going on. A great dashboard, like the kind you’ll find with Cisco Meraki, puts everything you need front and center—network health, who’s connected, and what they’re doing. This single-pane-of-glass view lets you catch small hiccups before they turn into full-blown outages.
But a slick interface is only half the story. The real power lies in the analytics behind it. A top-tier platform won’t just tell you the network is "on"; it will show you how it's being used. You’ll see which apps are hogging bandwidth and identify the busiest corners of your building. That kind of insight is pure gold for fine-tuning performance and planning for future growth.
Zero-Touch Deployment and Effortless Scalability
For most IT teams, one of the biggest pain points is expansion. Your platform has to grow with you, whether you’re adding a single AP in the office or a hundred across new retail locations. This is where cloud management really shines.
Imagine shipping a new access point directly to a new site. Someone plugs it in, and it automatically pulls its entire configuration from the cloud. That’s zero-touch provisioning, a cornerstone of modern access point management that eliminates hours of tedious manual setup. You can literally manage a global network from your couch.
The goal is to grow your network without growing your workload. True scalability isn’t just about adding more devices; it's about keeping management simple and centralized, no matter how big you get.
This hands-off approach is a lifesaver in fast-moving industries like Retail and Education, where new stores or classrooms need to get online yesterday. Powerful hardware is what makes this magic possible, which you can read more about in our guide to enterprise Wi-Fi access points.
Built-in Security and Authentication That Just Works
None of the bells and whistles matter if your network is wide open to threats. A modern management platform needs to have serious security tools baked right in—and we’re talking about much more than a basic firewall. Look for platforms that make sophisticated authentication solutions easy to implement.
The best systems simplify creating secure access for everyone:
- Guest Access: Quickly set up a branded Captive Portal to onboard visitors securely without giving them the keys to the kingdom.
- Corporate Security: Roll out advanced protocols like IPSK or EasyPSK. This gives every employee or company device its own unique key, which is a must-have for any BYOD Corporate environment.
- Automated Updates: The platform should handle security patches and firmware updates automatically from the cloud, so you’re always protected from the latest vulnerabilities.
Industry leaders like Cisco have woven these security features directly into the management fabric, making robust protection feel like second nature. This kind of integration is becoming more important every day. The wireless access point market is projected to skyrocket from $21.94 billion to $43.79 billion in the next decade, a clear sign of the massive demand for secure, reliable Wi-Fi. You can discover more insights about wireless market trends to see where the industry is headed. At the end of the day, the right platform makes top-tier security feel effortless.
Common Questions About Managing Access Points
As you start to map out a wireless network, a few key questions always come up. It doesn't matter if you're building a new network from scratch or trying to improve the one you already have—getting the fundamentals right is everything. Let's walk through some of the most frequent questions people ask about access point management.
What’s the Difference Between a Router and an Access Point?
This is probably the most common question out there, and for good reason. It’s easy to get them mixed up.
Think of your router as the quarterback of your network. It's the device that connects to the outside world (the internet) and directs all the traffic, assigning local IP addresses to every device that connects.
An access point, or AP, is more like a specialized receiver. Its one job is to take a wired connection from your network and broadcast it as a powerful, stable Wi-Fi signal. The all-in-one box you likely have at home is a combination router and AP. But in larger environments like offices, schools, or retail stores, you need multiple, dedicated APs to ensure strong, seamless coverage everywhere. These APs are then managed together by a single, central system.
How Do I Secure Wi-Fi in a BYOD Environment?
When everyone brings their own devices to work—a BYOD Corporate setup—security can feel like a nightmare. But it really boils down to two things: smart separation and modern authentication.
First things first, you absolutely have to create separate Wi-Fi networks (or SSIDs) for your internal team and for your guests. This is non-negotiable. It builds a digital wall that keeps guest traffic completely isolated from your sensitive company files and systems.
For guests, a Captive Portal is the perfect solution. It’s a branded login page that greets users, requiring them to accept your terms or sign in before they can get online. You can get a good feel for how this works by learning more about a Wi-Fi Captive Portal.
For your employees' personal devices, the days of a single, shared Wi-Fi password are over. That’s a huge security hole. Instead, you need a modern authentication solution like Identity PSK (IPSK) or EasyPSK. These technologies, often found in platforms from vendors like Cisco, give each user or device its own unique, private password. This provides an incredible level of control—if someone leaves the company, you can revoke their access instantly without affecting anyone else.
The core principle of BYOD security is to never use a single password for everyone. With solutions like IPSK, you move from a shared, vulnerable key to a system where every user has their own secure, personal key.
Is Cloud-Based AP Management Better Than On-Premise?
For most businesses today, the answer is a clear and simple yes.
An on-premise controller is a physical box you have to buy, install in your server room, and maintain yourself. This means big upfront costs, manual software updates, and the headache of needing someone on-site if things go wrong.
Cloud-based management, like the system pioneered by Cisco Meraki, moves all that complexity to the cloud. The benefits are huge. There's no expensive hardware to buy, security patches are rolled out automatically, and you can monitor and manage your entire global network from a simple web dashboard. This approach makes deployment faster, cuts down on operational costs, and scales up effortlessly as you grow.
How Many Access Points Does My Space Need?
The honest answer? It depends. Figuring out the right number of APs is a balancing act. You have to consider the physical size of your location, what the walls are made of (concrete and metal are notorious Wi-Fi killers), and how many people will be connecting at once.
This last point, called user density, is critical in places like the Education and Retail sectors. A crowded lecture hall or a busy store will need far more APs than a quiet office.
The best way to get a truly accurate number is with a professional site survey. But for a quick estimate, you can think in terms of coverage zones. A typical open-plan office might need one AP for every 2,000 to 2,500 square feet. A high-density spot, like that lecture hall, might need its own dedicated AP just to handle all the simultaneous connections. Thankfully, modern access point management platforms often come with built-in planning tools like heatmaps, which let you visually map out your coverage and find any dead spots before you install a single device.
Ready to take control of your Wi-Fi network? Splash Access provides a powerful, intuitive platform that works seamlessly with Cisco Meraki to create secure, engaging, and easy-to-manage wireless experiences. Get started with Splash Access today