Hey there! When it comes to boosting your WiFi performance, the real goal isn't just about chasing faster speeds. It’s about getting to the root cause of the problem to create a stable, secure, and genuinely intelligent user experience for everyone.
After all, nothing brings a busy environment to a standstill faster than that dreaded spinning loading icon.
Why Your WiFi Feels So Slow
Let’s get real for a moment. Whether you're managing a sprawling university campus, a bustling retail store, or a corporate office full of personal devices, terrible WiFi is more than just an annoyance—it's a productivity killer. The problem usually runs much deeper than simply having "too many people connected."
Often, the true culprits behind a sluggish network are hiding in plain sight. Outdated hardware that can't handle modern traffic is a huge one. You can dig into some of the common problems with WiFi routers to see if your own equipment is the bottleneck. But even with the latest gear, something as simple as improper network segmentation can create chaos, letting low-priority guest traffic bog down your critical business operations.
The Challenge of Modern Environments
High-density spaces like lecture halls, storefronts, and open-plan offices are a whole different beast. These areas are swimming in radio frequency (RF) interference from countless devices, all fighting for the same airspace. This "digital noise" can seriously mess with your signal quality and bring everything to a crawl.
In these environments, a one-size-fits-all network plan is doomed to fail.
- Education: A university has to juggle secure access for students, faculty, and guests, ensuring reliable connections everywhere from dorm rooms to massive auditoriums.
- Retail: Stores need rock-solid connectivity for their point-of-sale systems and inventory scanners, all while offering public guest WiFi that doesn’t put the main network at risk.
- Corporate: With so many employees bringing their own devices (BYOD Corporate sectors), IT teams need a way to securely onboard a flood of personal phones and laptops without creating security gaps or performance issues.
Keeping Pace with Evolving Technology
WiFi technology is moving at lightning speed, and the performance expectations have soared. Top-tier hardware from providers like Cisco and its cloud-managed Meraki line packs a serious punch, but you have to configure it correctly to see the benefits.
The leap between standards is massive. The latest Wi-Fi 7 standard, for example, delivers speeds up to 2.4 times faster than Wi-Fi 6. It's no surprise that it's projected to hit 90% adoption in enterprise networks by 2028, a clear sign of the global demand for better wireless. You can learn more about the accelerated adoption of new WiFi standards and what this means for your network's future.
Ultimately, improving WiFi performance is about more than just raw speed. It’s about creating a seamless and intelligent user experience through smart Authentication Solutions like Captive Portals and IPSK or EasyPSK systems.
Finding Your WiFi Performance Bottlenecks
Before you can fix a slow network, you have to play detective. A sluggish WiFi connection is just a symptom, and simply throwing new hardware at it is like trying to fix a sputtering engine by giving the car a new paint job. It misses the point entirely. The good news is your network is already telling you what’s wrong; you just need to know how to listen.
This whole process kicks off by digging into the analytics tools that come with platforms like Cisco Meraki. These dashboards are absolute goldmines of information, laying out everything from signal interference and client density to traffic patterns and which apps are eating up your bandwidth. By learning to read this data, you can stop guessing and start making informed, strategic fixes.
Think about a busy Retail store where the point-of-sale (POS) terminals keep dropping their connection right in the middle of the Saturday rush. Or a university campus in the Education sector where students are constantly complaining about dead zones in certain dorms. In both cases, the answer isn’t a mystery—it’s hidden right there in the network’s own data.
Digging into Network Analytics
Your first move is to figure out what "normal" actually looks like for your network. Establishing a performance baseline is key. Once you understand your typical traffic patterns, any deviation will stick out like a sore thumb. A sudden spike in latency or a nosedive in throughput during specific hours can point you directly to the source of the bottleneck.
One of the best ways to pinpoint when and where these issues pop up is by looking at historical data. Learning how to perform trend analysis can transform a mountain of raw numbers into a clear story about your network’s health over time. This is how you spot those nagging, recurring problems, like a specific access point that gets overwhelmed every single weekday at noon.
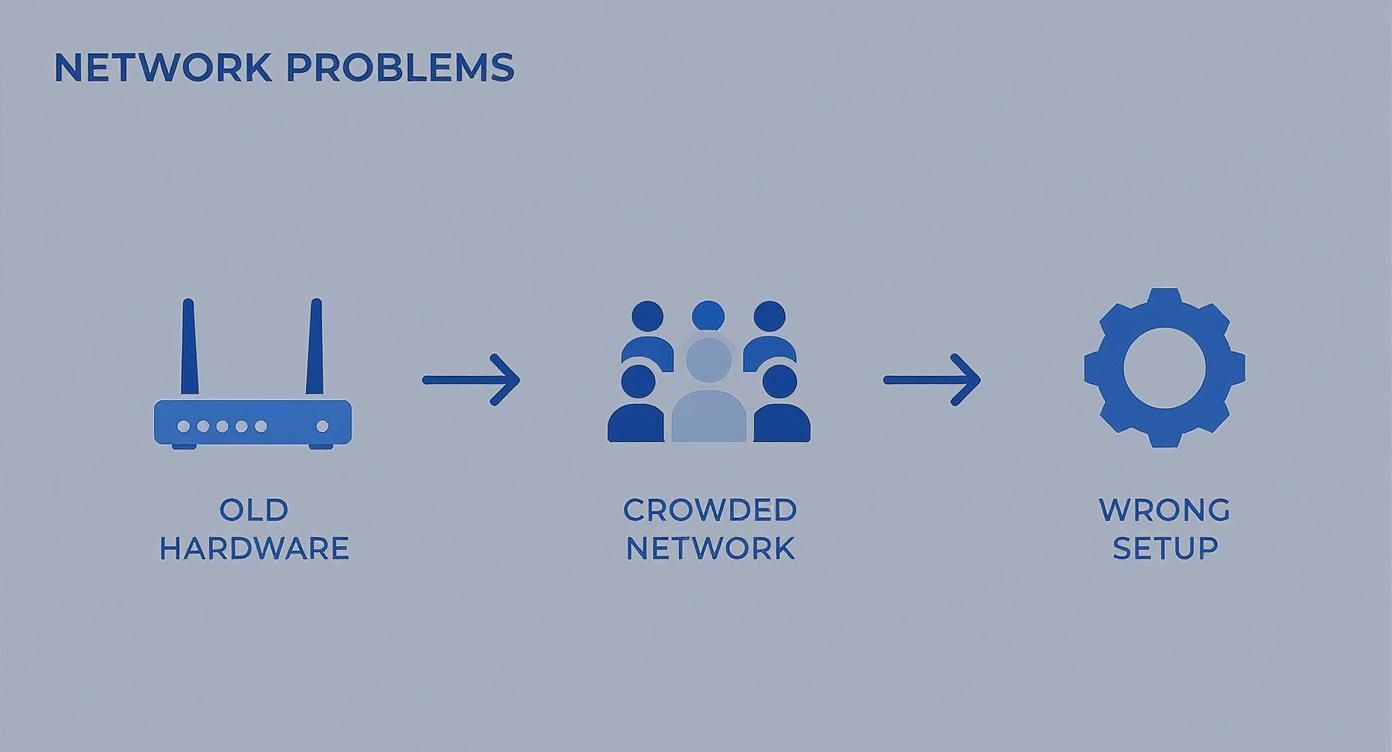
The infographic below breaks down the three most common culprits behind a slow network.
As you can see, performance problems usually boil down to aging hardware, a congested network, or a simple misconfiguration. All of these are things you can uncover with a bit of careful analysis.
Identifying Hardware and Configuration Issues
Once you've gotten the hang of your analytics dashboard, you can start hunting for specific troublemakers. In a corporate BYOD environment, for example, you might see that a single access point in the main conference room is serving 80% of the clients, while the ones nearby are sitting nearly idle. That’s a massive red flag pointing to a need for better load balancing or a rethink of your access point placement.
But a dashboard can only tell you so much. To get the full picture, you need to look at the physical layer. A professional wireless assessment is crucial for uncovering problems that analytics might miss. Our guide on how to perform a site survey for your wireless network walks you through the process of identifying physical obstructions, RF interference from non-WiFi sources, and those frustrating architectural dead zones.
Here are a few key things to investigate:
- Channel Utilization: Are all your access points fighting for space on the same crowded channels? High co-channel interference is a classic performance killer.
- Client Signal Strength (RSSI): Do you have areas where devices consistently show weak signals? That’s a dead giveaway for a coverage gap.
- Application Traffic: What’s actually using up your bandwidth? Sometimes, a non-critical background app is hogging the resources your business-critical operations need.
The Role of Authentication in Performance
Finally, don’t forget to look at how people get onto your network in the first place. A clunky or poorly managed authentication process can create its own set of bottlenecks. When everyone is sharing a single password, you have zero visibility or control over who’s on your network and what they’re doing.
This is where modern Authentication Solutions can make a huge difference. By integrating a Captive Portal with your Cisco Meraki gear, you create a controlled gateway to your network. This not only lets you manage traffic more effectively but also provides valuable user data you can act on.
On top of that, using systems like IPSK or EasyPSK lets you give each user or device its own unique credentials. This doesn't just tighten security; it also helps organize network traffic, preventing the kind of digital free-for-all that can cripple performance in busy Education or Retail environments.
How Smart Authentication Boosts Performance
After you've pinpointed where your network is struggling, the next logical move is to examine who is connecting and how. The onboarding process shouldn't be a trade-off between security and user frustration, but that's exactly what you get with old-school methods. Smart, modern authentication isn't just a security upgrade; it's a fundamental part of improving WiFi performance by replacing clunky, insecure shared passwords with far more efficient systems.
This is about bringing order to network chaos. When dozens, or even hundreds, of devices all pile onto the network using the same password, you're left with a digital free-for-all. You have zero visibility into who is hogging your bandwidth and no way to prioritize critical traffic, which directly tanks performance for everyone.
Moving Beyond The Single Password
Let's be honest, the old approach of a single WiFi password scribbled on a whiteboard is a performance bottleneck waiting to happen. It treats every single connection the same, whether it's a student streaming 4K video in a dorm or a point-of-sale terminal in a Retail store processing a crucial transaction. This total lack of control is where so many performance headaches begin.
This is where smarter Authentication Solutions like Identity Pre-Shared Keys (IPSK) and EasyPSK completely change the game. Instead of one key for the entire building, these technologies assign a unique, private credential to each user or device. It’s a simple shift in concept, but the impact on network organization and speed is massive.
Think of it like this: a shared password is a giant, chaotic parking lot where everyone fights for a spot. IPSK is like giving everyone their own reserved space. The flow is smoother, congestion disappears, and you can instantly see who belongs where. From the moment a user connects, IPSK helps you automatically segment network traffic.
How Granular Control Enhances Performance
With a unique key tied to every user, you gain an incredible amount of control. A Captive Portal, especially when integrated with powerful hardware from industry leaders like Cisco and Meraki, becomes your intelligent gateway. It’s the first thing users interact with, and it’s where performance optimization really kicks in.
Take an Education environment, for example. You can set rules that automatically place different user groups onto separate virtual networks (VLANs) as soon as they connect.
- Faculty: Immediately placed on a high-priority network with full access to academic resources and servers.
- Students: Given plenty of bandwidth for research, but with throttling on non-essential streaming during peak class hours.
- Guests: Connected to a totally isolated network with strict bandwidth caps, ensuring they can't disrupt core educational activities.
This automatic sorting stops a few heavy users from dragging down the entire network. If you're looking for a deeper dive into these methods, you can explore various modern user authentication techniques that go far beyond basic passwords.
Before diving into the BYOD challenge, it's helpful to see how these methods stack up.
Comparing WiFi Authentication Methods
Different environments call for different tools. Choosing the right authentication method is key to balancing security, user convenience, and raw network performance. Here’s a quick breakdown of the most common approaches.
| Authentication Method | Best For | Security Level | User Experience | Performance Impact |
|---|---|---|---|---|
| Open Network | Public hotspots, temporary guest access | Very Low | Frictionless: No password needed. | High Risk: Prone to congestion and abuse. |
| Shared PSK | Small offices, homes | Low | Simple: One password for all. | Poor: No traffic segmentation or control. |
| Captive Portal | Hotels, retail, public venues | Medium | Structured: Requires login/form fill. | Moderate: Can segment users, but shared backbone. |
| IPSK/EasyPSK | Corporate, education, complex venues | High | Seamless: Unique key per user/device. | Excellent: Enables granular traffic shaping & VLANs. |
| 802.1X/RADIUS | Enterprise, high-security environments | Very High | Complex: Requires client-side configuration. | Excellent: Deep control, but high management overhead. |
As the table shows, methods like IPSK hit a sweet spot, offering strong security and performance gains without the complexity of a full-blown 802.1X deployment.
The BYOD Challenge in Corporate Environments
This level of control is absolutely critical in the modern corporate BYOD sector. When employees bring their personal laptops, tablets, and phones to work, IT teams are thrown into a constant battle. Onboarding all these devices securely without drowning the helpdesk in tickets is a real struggle.
With an IPSK or EasyPSK system managed through a platform like Splash Access, that entire onboarding headache disappears. An employee can self-register their devices through the Captive Portal, which automatically generates and assigns them a unique key. That one key follows them across all their devices, ensuring a consistent, secure connection everywhere.
This approach doesn't just make life easier for IT; it directly boosts network performance. Since every device is tied to a specific user, you can easily track bandwidth usage, spot resource-hungry apps, and apply targeted policies without disrupting anyone else.
Even better, when an employee leaves the company, you just revoke their single key. Instantly, all their associated devices are kicked off the network. Compare that to a shared password, where a departed employee leaves a gaping security hole and changing the password for hundreds of people creates a logistical nightmare. Smart authentication cleans up this entire lifecycle, keeping your network organized, secure, and running at peak speed.
Fine-Tuning Your Network Infrastructure
Now that you've diagnosed your network's health and have a smart authentication strategy ready, it's time to get under the hood. Fine-tuning your network infrastructure is where the real magic happens—small, deliberate adjustments can lead to massive gains in improving WiFi performance. This isn’t about ripping everything out and starting over. It’s about making intelligent tweaks to create a more stable, efficient, and reliable wireless environment for everyone.
It all starts with the physical world. Where you place your access points (APs) is one of the most critical factors, and just guessing is a recipe for disaster. This is especially true in tricky environments like a huge lecture hall in an Education setting or a multi-floor Retail store, where dead zones and dropped connections are common headaches.
Strategic Access Point Placement
You have to start thinking like a radio wave. In a massive lecture hall, for instance, sticking APs high on the ceiling might seem like the obvious move. But when you pack hundreds of students with their laptops and phones into that space, you create a dense wall of interference that chokes the signal. A smarter approach is often a mix of ceiling-mounted APs for broad coverage and under-seat APs to get closer to the devices.
The same logic applies to a multi-level retail space. Signals struggle to punch through concrete floors and navigate around metal shelving. If you just stack APs directly on top of each other on different floors, you’re asking for signal overlap and interference. Instead, stagger them vertically. This simple change ensures your point-of-sale systems stay online and your guest WiFi runs smoothly. For more ideas, check out our guide on effective access point management strategies.
Mastering Your Meraki Dashboard
Once your APs are physically in the right spots, your next stop is the Cisco Meraki dashboard. This is the command center where you can optimize the radio frequency (RF) environment, and a few key settings can make a night-and-day difference.
- Channel Planning: Don't let your APs all talk over each other. Auto-channel settings can work, but for dense environments, manual assignment is king. Set your APs to non-overlapping channels (1, 6, and 11 for the 2.4GHz band) to drastically cut down on co-channel interference, one of the most common performance killers out there.
- Power Level Adjustments: It’s tempting to crank the transmit power to the max on every AP, but this usually backfires. Overly "loud" APs create a "sticky client" problem, where a device clings to a faraway signal instead of roaming to a much closer, stronger one. Tuning the power down often creates a cleaner RF environment and encourages devices to roam seamlessly.
- Band Steering: Think of the 5GHz band as a wide-open, multi-lane highway and the 2.4GHz band as a congested side street. By enabling band steering in Meraki, you can actively nudge dual-band devices onto the faster, less crowded 5GHz frequency. This frees up the 2.4GHz band for older legacy devices that have no other choice.
These tweaks are absolute game-changers in packed BYOD Corporate offices where hundreds of different devices are all fighting for airtime. A little RF management brings much-needed order to the chaos.
The Power of Network Segmentation
Another incredibly effective tool in your arsenal is network segmentation using VLANs (Virtual Local Area Networks). A VLAN essentially creates separate, private lanes on your network highway, preventing traffic from one group of users from bogging down another.
For a university, this is non-negotiable. Using their Captive Portal alongside IPSK or EasyPSK Authentication Solutions, they can automatically sort users onto distinct VLANs:
- Guest Network: Isolated on its own VLAN with strict bandwidth limits. No Netflix streaming is going to impact academic work.
- Student BYOD Network: Gets a healthy amount of bandwidth but is walled off from sensitive administrative systems.
- Faculty & Staff Network: Receives top priority with the highest speeds and full access to internal servers and resources.
- IoT Devices: Smart locks, environmental sensors, and security cameras get their own secure VLAN, closing a potential backdoor for attacks on the main network.
This kind of organization isn't just about performance; it's a massive security upgrade. By siloing traffic, you limit the potential blast radius of any security incident.
All these local tweaks are perfectly timed to take advantage of a faster global internet. The worldwide median download speed shot up an incredible 17% in just a year, from 78.68 Mbps in 2023 to 92.96 Mbps by early 2024. With fiber-optic reaching 58.6% of households globally, the backbone is there. A well-tuned local network is what lets you actually use that speed.
Using Analytics for Continuous Improvement
Here’s the thing about WiFi performance: it's not a "set it and forget it" deal. It’s a living, breathing system that needs constant attention. The minute you stop monitoring is the moment small, nagging issues start to snowball into major network headaches. Proactive management is the only way to stay ahead, and this is where the rich data from your Splash Access Captive Portal and Cisco Meraki infrastructure becomes your secret weapon.
Think of your network analytics as an ongoing conversation. It’s constantly telling you what’s working, what’s not, and where you need to focus your energy. By tapping into this stream of data, you can finally break free from the reactive "break-fix" cycle and start making strategic moves that keep your network humming—long before users ever notice a problem.
It’s about turning WiFi management from a chore into a genuine strategic asset.
Key Metrics to Track for Better WiFi
The first step is simply knowing what to look for. Your Splash Access dashboard, working in lockstep with Meraki, is a goldmine of information. But instead of getting lost in a sea of numbers, you need to zero in on the metrics that directly impact user experience.
Here are a few of the most important data points I always keep an eye on:
- Connection and Session Times: How long does it actually take for users to get online? And are they staying connected, or are you seeing a pattern of frequent drops and reconnects? A high drop rate is a classic red flag for an unstable network.
- Data Usage Trends: Which apps and services are the real bandwidth hogs? Once you identify the top data consumers, you can implement traffic-shaping rules to protect the performance of your most critical operations.
- Client Density and Distribution: Where are the real hotspots in your facility? Analytics can show you exactly which access points are consistently overloaded, pointing to the perfect places to add more capacity.
- Dwell Times and Return Rates: How long do visitors stick around, and how often do they come back? This is especially valuable in Retail, helping you map out foot traffic and understand real-world customer engagement.
By reviewing these metrics regularly, you start to see the patterns. You spot trends and can address potential problems well before they escalate. It's possible to achieve this visibility and learn how to get more analytics with less infrastructure.
Turning Data into Actionable Insights
Collecting data is easy. The real skill is using it to make smart, decisive moves. Let's walk through how this plays out in the real world.
Imagine a large Retail environment. Your analytics might reveal that the WiFi slows to a crawl every Saturday afternoon right near the main entrance. This isn't just an annoyance for shoppers—it could be crippling your point-of-sale systems. Armed with that specific insight, you can immediately optimize AP placement in that zone or tweak bandwidth allocation to ensure payment processing always gets top priority.
Or consider an Education campus. Analytics can pinpoint peak usage times in the library or student union. Knowing that thousands of students will be hitting the network between 2 PM and 5 PM allows the IT team to get ahead of the crunch. They can use Authentication Solutions like IPSK or EasyPSK to give academic traffic the fast lane while temporarily throttling non-essential streaming.
This proactive approach is the core of modern network management. You're no longer just putting out fires; you're using data to prevent them from ever starting.
In a BYOD Corporate setting, the challenge is different. Analytics can help you spot rogue devices or users consuming an unusual amount of data, which could signal a misconfigured app or even a security risk. By tying each connection to a specific user through an EasyPSK system, IT can quickly find the source of the problem and address it directly—without disrupting the entire office.
The Global Push for Better Connectivity
This intense focus on continuous improvement is happening alongside a massive global investment in network infrastructure. The widespread adoption of advanced Wi-Fi technologies has led to a major drop in latency, which is that critical delay in data transfer. In 2024, the global median latency for Wi-Fi connections plunged to just 9 ms, a huge boost for real-time applications like video calls. This trend is reinforced by the fact that 43% of Americans now have access to fiber internet, a key driver of faster, more reliable speeds. You can read more about these global trends in internet speeds and connectivity.
These breakthroughs set a new standard for performance, making it even more crucial to fine-tune your local network. You can have the fastest internet pipe in the world, but if your internal WiFi isn't optimized with smart analytics and robust Authentication Solutions, you’ll never feel the full benefit. It’s the combination of a strong internet backbone and intelligent local management that truly delivers an exceptional user experience.
Common Questions About Improving Wi-Fi Performance
Even with a solid plan, a few questions always seem to pop up when you're deep in the trenches of boosting a network's performance. I get asked these all the time, especially from folks managing busy networks in Education, Retail, and corporate BYOD environments.
Let's clear the air on a few key points.
How Does a Captive Portal Actually Improve Wi-Fi Performance?
It’s a fair question. Most people just see a login page, but a well-designed Captive Portal is so much more than that—it’s an intelligent gatekeeper for your entire network.
Think of it this way: you can create different tiers of access. For example, in a retail store, you could give full-throttle bandwidth to the staff running point-of-sale systems while gently limiting the speeds for guest shoppers. This kind of traffic shaping is crucial. It stops non-essential guest activity from bogging down the systems that actually make you money.
Plus, when you use a solution like Splash Access with a platform like Cisco Meraki, you get a goldmine of data. You can see how people are using the network and how long they're connected, giving you the insights to fine-tune everything from AP placement to resource allocation.
Why Is IPSK Better Than a Single Wi-Fi Password?
This one is huge for both security and day-to-day management. Identity Pre-Shared Key (IPSK) and EasyPSK give every single user or device its own unique password, even though they're all connecting to the same network name (SSID). This is a game-changer compared to sharing one password around.
For starters, if one person's key gets compromised, you just revoke that single key. The rest of your network stays secure, and no one else is affected. This is a lifesaver in places like university campuses or large offices where people and their devices are constantly coming and going.
With Authentication Solutions like IPSK, you move from a chaotic "everyone for themselves" network to an organized, secure, and efficient system where every connection is accounted for.
This level of control also makes troubleshooting a breeze. When you can trace a performance issue back to a specific user or device, you can solve problems in minutes, not hours.
Can I Improve My Cisco Meraki Wi-Fi Without New Hardware?
Absolutely. In fact, you'd be surprised how much performance you can squeeze out of your existing setup just by optimizing what you already have. Your Meraki dashboard is your best friend here.
Before you even think about buying new access points, a simple site survey to check for RF interference and find coverage dead zones can work wonders. From there, you can make a few key adjustments without spending a cent:
- Adjust Channel Widths: In crowded areas, narrowing your channels can seriously cut down on interference from neighboring networks.
- Tune Transmit Power: Sometimes, turning the power down is the right move. It helps prevent "sticky clients" that refuse to roam to a closer AP.
- Enable Band Steering: Gently nudge devices that can use the 5GHz band over to that less-congested highway, leaving the 2.4GHz band free for older devices.
When you combine these technical tweaks with a smart onboarding strategy using a Captive Portal and IPSK, you can completely revitalize your network. It’s all about managing traffic and user access intelligently. You're not just buying newer, faster gear; you're making the gear you own work smarter.
Ready to transform your network management from a reactive chore into a strategic asset? Splash Access provides the powerful Captive Portal and authentication solutions you need to optimize your Cisco Meraki infrastructure.
Discover how Splash Access can help you improve your WiFi performance today!