Have you ever wondered how all the devices in your office, school, or favorite coffee shop seem to magically talk to each other? It’s not magic, but it is a master plan. That plan is the network topology in computer systems, and it's the invisible blueprint that dictates how every phone, laptop, and server is arranged and how they all communicate.
What Is Network topology and Why Does It Matter
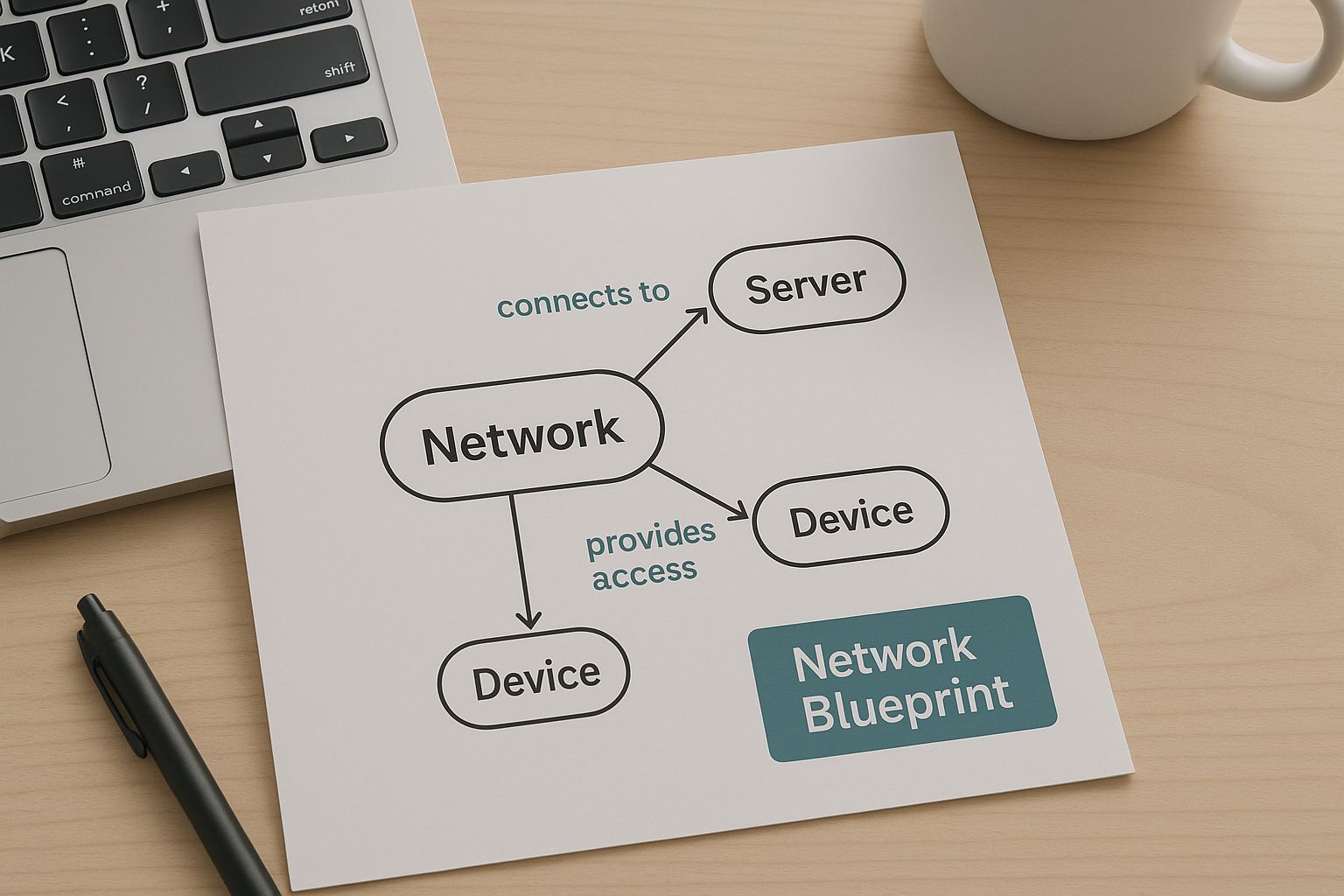
At its core, a network topology is simply the layout of a network. It defines how all the different nodes—like computers, routers, and switches—are connected. This covers both the physical arrangement of cables and hardware as well as the logical path data takes to get from one point to another.
Getting this blueprint right is the first step toward building a reliable and efficient network, whether you're setting up a system for a busy school in the Education sector, a sprawling Retail complex, or a high-security BYOD Corporate office.
The whole idea of deliberately designing a network layout goes way back to the early days of ARPANET, the internet's ancestor. Just a few months into the project, the engineers realized that just randomly connecting things wasn't going to cut it. By October 1969, they applied formal mathematical principles to redesign the network, creating a new layout that was 25% cheaper to run and delivered 40% higher throughput. This was the first real application of network optimization, and it set the stage for everything that followed.
This visual helps illustrate how a network topology acts as that foundational blueprint for connecting all your devices.
Think of it like an architectural plan for a building. A solid foundation and a smart layout are essential for ensuring everything built on top of it is stable, efficient, and ready for the future.
The Foundation for Modern Connectivity
A well-designed topology, especially when built with reliable hardware from vendors like Cisco or Meraki, is what separates a frustrating user experience from a seamless one. It directly impacts network performance, its reliability, and how easily you can scale it up later.
This is even more critical in today's wireless world. With modern WiFi, you can create complex logical layouts without touching a single physical cable. If you're curious about how physical hardware can be split to support multiple, separate networks, you can dive deeper into network virtualization.
Choosing the right topology is crucial across different industries:
- Education: A robust and scalable layout is essential to keep thousands of student and faculty devices connected and learning without a hitch.
- Retail: The network's design underpins everything from the guest WiFi and its Captive Portals to the point-of-sale systems that process every transaction.
- BYOD Corporate: In a bring-your-own-device environment, the topology must be secure and segmented enough to handle personal devices using advanced Authentication Solutions like IPSK and EasyPSK.
Ultimately, the right network design makes everything just work. From a simple guest login to complex security protocols, a good topology ensures data gets where it needs to go—quickly, reliably, and securely.
A Look at Common WiFi Network Topologies
Now that we have a solid handle on what a network topology is—essentially the blueprint for how devices connect and talk to each other—let's dive into the most common designs you'll actually see in the wild. We'll explore four classic layouts: Bus, Ring, Star, and Mesh. Each one has its own unique way of handling data, which comes with its own set of pros and cons.
Think of a bus topology like a single main street. All the data traffic travels along this one shared road, which is simple but can lead to traffic jams. A ring topology, on the other hand, is more like a one-way roundabout where data passes from one device to the next in a circle. The way a network directs its traffic has massive implications for speed, reliability, and how easy it is to manage.
For a bit of history, the original Ethernet, rolled out way back in 1973, used a bus topology. It was a straightforward design where every device was hooked up to one main cable. But as networks got bigger and busier, data collisions became a huge headache. This bottleneck paved the way for the star topology, which by the early 2000s dominated over 99% of business LANs.
The Rise of the Star Topology
The star topology has become the undisputed champion for most modern WiFi networks, and for very good reason. Picture an airport hub. Every device gets its own direct, non-stop flight to the central router or switch. This point-to-point setup makes the network incredibly stable and a breeze to manage.
Here’s a simple visual to show you what I mean.
The beauty of this design is that if one device's connection goes down, it doesn't bring the whole network crashing down with it. The other devices can keep on communicating with the hub, completely undisturbed.
This kind of reliability is a lifesaver in places like schools or retail stores, where constant connectivity is non-negotiable. You don't want a single student's laptop issue to knock an entire classroom offline, just as you don't want one glitchy payment terminal to kill the guest WiFi for an entire store.
The core benefit of a star topology is its isolation of failures. A problem with one connected device or its cable affects only that single node, leaving the rest of the network operational. This makes troubleshooting far simpler and boosts overall network stability.
The Power of Mesh in Modern WiFi
While the star topology is king for its straightforward reliability, another powerful player has emerged, especially for wireless networks: the mesh topology. In a mesh network, devices don't just talk to a central hub; they can connect to multiple other devices, creating a web of redundant pathways for data. If one connection drops, the data just finds another way to its destination.
This self-healing ability makes mesh networks absolutely perfect for blanketing large or tricky areas with seamless WiFi. It’s an ideal choice for:
- Sprawling University Campuses: Ensuring students and faculty have a solid connection everywhere, from the lecture hall to the coffee shop.
- Large Retail Stores: Providing uninterrupted WiFi for guest Captive Portals and staff inventory scanners across the entire shop floor.
- BYOD Corporate Offices: Supporting a high density of devices in a bring-your-own-device setting without dead zones.
Modern solutions from vendors like Cisco Meraki make deploying and managing these advanced WiFi topologies surprisingly simple. To really get into the weeds, you can check out our deep dive on https://www.splashaccess.com/mesh-network-topologies/ for more on their practical uses. Of course, choosing the right hardware is just as important as the design itself. To see what's out there, it's worth looking into the best routers for small business, including mesh systems.
Quick Comparison of Common Network Topologies
To help you see how these topologies stack up against each other at a glance, here’s a quick comparison table. It breaks down the main pros, cons, and best-fit scenarios for each design.
| Topology Type | Key Advantage | Main Disadvantage | Ideal For |
|---|---|---|---|
| Star | High reliability; easy to manage | Higher initial cost due to cabling and hardware | Most modern home, office, and business WiFi networks |
| Mesh | Self-healing and highly redundant | Can be complex to configure without modern tools | Large areas needing seamless coverage (e.g., campuses, warehouses) |
| Bus | Simple and inexpensive to set up | A single cable failure can take down the network | Older, small networks or temporary setups (largely obsolete) |
| Ring | Performs well under heavy load | A single device failure can disrupt the entire loop | Specialized networks like some fiber-optic backbones (MANs) |
Ultimately, the right topology depends entirely on your specific needs—from the size of your space to your budget and reliability requirements. While star and mesh are the clear frontrunners today, understanding all the options gives you the insight to build a network that truly works for you.
Using Hybrid Topologies for Large-Scale Networks
When a single, off-the-shelf design just doesn't cut it, what do you do? You get creative and build a hybrid. In the real world of large-scale networking, organizations rarely stick to one simple network topology. Instead, they mix and match, combining different layouts to create powerful hybrid structures that offer the best of multiple worlds—scalability, reliability, and sheer performance.
Imagine a multi-floor office building or a sprawling school campus. A single star topology would buckle under the strain. This is where a hybrid approach, often called a tree topology, really shines. It’s essentially multiple star networks (think one for each floor or department) all connected to a central "trunk" line, which often functions like a bus topology. This creates a surprisingly organized and robust structure that can handle a high density of users and devices without breaking a sweat.
The Rise of Complex, Intelligent Networks
This move toward blended designs has been a game-changer for modern IT. The transition to hybrid topologies took off as organizations faced ever-growing demands for more flexible and scalable networks. In fact, by 2022, over 70% of enterprises were using hybrid network topologies in their IT infrastructure, a massive jump from less than 20% back in the late 1990s. This shift was fueled by technologies that allow for dynamic, real-time network reconfiguration. You can find more insights about this evolution at Netseccloud.com.
This flexibility is absolutely critical in environments with diverse needs, from Education and Retail to large BYOD Corporate offices. Modern network solutions from providers like Cisco and Meraki are specifically engineered to manage these complex environments. They provide the tools needed to oversee intricate layouts and ensure consistent performance across thousands of connections.
A hybrid topology isn't just about connecting more devices; it's about creating a smarter, more resilient network that can adapt to the unique demands of an organization, segmenting traffic and isolating potential issues effectively.
Connecting Topologies with Advanced Security
The real power of a well-designed hybrid topology comes to life when you pair it with modern security measures. For instance, a university might use a tree topology to connect dozens of dorm buildings. On top of that physical layout, they can implement sophisticated Authentication Solutions like IPSK and EasyPSK. This allows them to issue a unique Wi-Fi password to every single student, even though they all connect to the same network—a huge leap forward in security and management.
Similarly, a retail chain can use a hybrid model to connect its stores, then layer Captive Portals on top for guest access. This setup not only provides a branded login experience but also allows them to gather marketing data while keeping their internal systems totally secure. The ability to manage these complex interactions is a key benefit of software-defined networking. Ultimately, hybrid topologies provide the strong, adaptable foundation needed for today's demanding and security-conscious networks.
How Network Topology Works in the Real World
Theory is one thing, but the real magic happens when you see how network topologies actually function in the places we go every day. Let's connect the dots and look at how these designs are put to work in schools, stores, and offices where the right layout is everything.
These complex physical and logical maps are the backbone of modern connectivity. At the ground level, bringing any topology to life depends on a solid physical layer. A professionally done data cable assembly is what ensures all those nodes can talk to each other without a hitch.
Education: A Connected Campus
Picture a sprawling university campus. You have thousands of students, professors, and staff all trying to get online at the same time. To manage this high-density environment securely, a star or hybrid topology is a must.
Each building—whether it's a classroom, library, or dorm—can operate as its own star network, which then connects to a central campus backbone. This segmented design, often built with hardware like Cisco Meraki, means an outage in the history department won't bring down online exams in the science building.
On top of this physical structure, schools can layer powerful Authentication Solutions like IPSK or EasyPSK. This tech lets them give every single student a unique WiFi password, tightening security and simplifying management without having to rewire the whole place.
Retail: Seamless Customer Experiences
Now, think about your last trip to a big retail store. A resilient mesh network is often the perfect choice here, blanketing the entire sales floor with seamless WiFi coverage. This setup pulls double duty. It supports the customer-facing Captive Portals for guest WiFi and, at the same time, runs the store's crucial internal inventory and payment systems.
When you log into the free WiFi, you're interacting with the network's logical topology. The store can show you a branded login page, push a special offer, and gain marketing insights. All of that guest traffic is kept completely separate from the secure point-of-sale and operational data. It’s a brilliant design that boosts the customer experience and business operations at once.
A well-designed network topology is the unsung hero of modern business. It's the framework that enables everything from secure mobile payments in a store to collaborative online learning in a classroom, all by ensuring data flows efficiently and reliably.
Corporate BYOD: Security Meets Flexibility
In a corporate office where everyone brings their own devices (BYOD), the network has a tough job. It needs to be strong enough to handle a flood of personal laptops, tablets, and phones without creating security holes. A hybrid topology is usually the go-to solution, blending the stability of star networks in different departments with a high-speed central backbone.
This lets IT teams create separate logical networks—one for company-owned devices and another for personal ones—even though they’re all using the same physical hardware. By pairing this structure with robust Authentication Solutions, IT can make sure every device is properly identified before it gets anywhere near sensitive company files.
For anyone tasked with managing these intricate environments, learning more about building a more resilient network is a fantastic next step.
Securing Your Network with Smart Authentication
A great network layout is just the starting point. The real strength comes from the security you build on top of it. Your network's structure—whether it's a star, mesh, or hybrid—is the physical foundation, but modern security measures are what bring it to life, turning a simple diagram into a controlled, secure environment.
Take the guest WiFi at your local coffee shop or retail store, for instance. The first thing you see when you connect is usually a Captive Portal—a branded login page. This is a perfect example of applying security to the network's logical design. It creates a safe gateway for visitors while keeping their internet traffic completely separate from the business's private, operational network.
This kind of separation is a must-have in any place with different user groups, from shoppers in a Retail setting to students and staff on a university campus in the Education sector.
Moving Beyond a Single Password
Not long ago, securing a WiFi network meant handing out the same password to everyone. This was a massive security headache, especially in a BYOD Corporate environment where employees bring their own devices. When someone left the company, the only way to cut off their access was to change the password for every single person. It was a logistical nightmare.
Thankfully, modern Authentication Solutions like Identity Pre-Shared Key (IPSK) and EasyPSK have completely changed the game. These systems let IT teams give a unique, private password to every user or device, all while they connect to the same WiFi network name (SSID).
Think about a large university campus built on a hybrid star topology. With IPSK, each of its 10,000 students can get their own personal WiFi key. If a student's laptop gets stolen or compromised, the IT team can instantly disable that one key without disrupting thousands of other students.
This level of detailed control is a huge step up for network management. It makes adding new users a breeze, seriously boosts security, and simplifies troubleshooting. When a problem pops up, administrators can pinpoint it to a specific user or device instead of digging through a sea of anonymous connections. These methods are powerful on their own and become even more robust when combined with other security layers, which you can read about in this guide on what is multi factor authentication.
Making Advanced Security Simple
You might think putting these advanced security tools in place would be a complicated project, but solutions from vendors like Cisco Meraki make it surprisingly easy. Their platforms are built to roll out sophisticated authentication across any network topology in computer systems without a lot of heavy lifting.
For example, an IT manager overseeing a retail chain can use a single Meraki dashboard to:
- Deploy a Guest WiFi Network: Quickly set up branded Captive Portals across dozens of store locations.
- Implement IPSK for Staff: Automatically create unique keys for company-owned devices to ensure they securely access internal resources.
- Manage BYOD Access: Establish policies that let employees use their personal devices for work safely, without giving them unrestricted access to the entire network.
This is what makes a modern network so powerful: the ability to easily and securely manage different groups of users on the same physical hardware. The right topology draws the map, but smart authentication acts as the gatekeeper, making sure only the right traffic gets where it needs to go.
Alright, let's dive into some common questions that come up when we talk about network topology. These are the practical, real-world things people want to know, so I've pulled together some straightforward answers to clear things up.
What's the Go-To Network Topology for WiFi These Days?
Hands down, the star topology is what you'll find in almost every modern WiFi setup. Think about your home or office: all your devices—laptops, phones, smart speakers—connect directly to a central hub, which is usually your wireless router or an access point. It's a classic hub-and-spoke model.
There's a good reason it's so popular: reliability. If your tablet loses connection, my laptop isn't affected. For larger spaces, like a corporate campus or a university, IT teams will often link multiple star networks together, creating what's called a hybrid or tree topology. This allows them to manage everything seamlessly using systems from providers like Cisco Meraki to ensure you have a strong signal no matter where you roam.
This centralized design also makes life a lot easier when you need to add a new device or figure out why something isn't connecting properly.
How Does Topology Impact Security Tools like IPSK?
It's a great question. Your network's topology is the roadmap—it defines how data physically and logically moves around. On the other hand, Authentication Solutions like IPSK (Identity Pre-Shared Key) act as the gatekeepers, controlling who can get onto that roadmap in the first place. The two are deeply connected.
Picture a sprawling star topology across a university campus, where thousands of students need WiFi access. Instead of giving everyone the same password (a huge security risk!), IPSK lets the IT department assign a unique WiFi password to every single student, even though they all connect to the same network name (SSID).
This is a game-changer. The university can instantly revoke access for a student who has left or grant it to a new one, all without having to reset the password for thousands of others. It brings incredible security and control to a simple, scalable layout.
This approach is incredibly powerful for managing access, whether it's for students on campus, employees in an office, or customers logging into a Captive Portal at a coffee shop.
What's the Best Topology for a Business with a BYOD Policy?
For any company embracing a BYOD (Bring Your Own Device) policy, a hybrid topology is almost always the right answer. Specifically, one that uses interconnected star networks as its foundation. This setup gives you the perfect mix of scalability and resilience to handle all those personal phones, tablets, and laptops.
You can get pretty granular with it. Each department could have its own star network, and all of these then connect back to a central, high-speed corporate backbone. This segmentation is fantastic for managing network traffic and containing potential security issues.
Combine this smart layout with a strong authentication method like EasyPSK, and you have a rock-solid BYOD strategy. The business can safely bring employee devices onto the network without exposing sensitive corporate data. It’s that one-two punch of a well-designed topology and robust access control that makes it all work securely.
At Splash Access, we're experts at using the power of Cisco Meraki hardware to build top-tier WiFi authentication and user engagement systems. We make it easy to set up secure access, whether you need branded Captive Portals or advanced IPSK, no matter what your network topology looks like. Learn more about what we do at https://www.splashaccess.com.