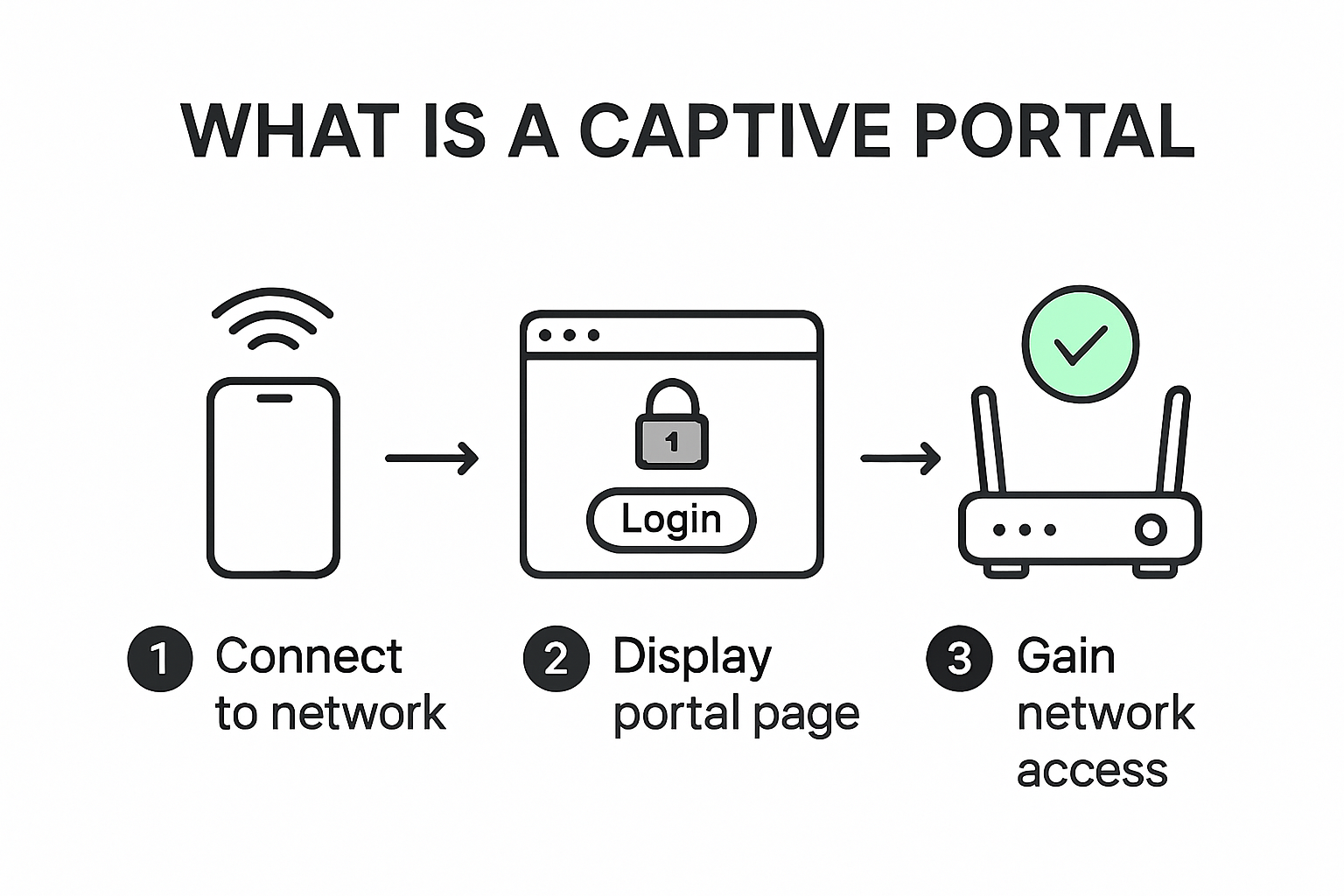
Captive portals are shaping the way businesses control who uses their Wi-Fi. Ninety percent of hotels now use captive portals to personalize guest internet access and collect valuable data. Now here is something most never consider. The real value goes far beyond basic internet logins or pop-up terms screens. These digital gatekeepers are quietly becoming the backbone of network security, user engagement and even advanced marketing strategies no matter the industry.
Table of Contents
- Understanding What Is A Captive Portal
- How Captive Portals Work In Different Industries
- Key Benefits And Challenges Of Captive Portals
- Best Practices For Setting Up A Captive Portal In 2025
Quick Summary
| Takeaway | Explanation |
|---|---|
| Captive portals act as network gatekeepers | Captive portals intercept web traffic, requiring user interaction, like authentication or acceptance of terms, before granting network access, ensuring a critical layer of security and data collection. |
| Industry-specific implementations enhance user engagement | In sectors like hospitality, education, and transportation, captive portals not only authenticate access but also serve strategic functions by promoting services, ensuring proper access control, and managing bandwidth effectively. |
| Balancing security with user experience is essential | Network managers must create intuitive authentication processes that do not frustrate users, balancing robust security measures with simplicity to avoid barriers to access. |
| Advanced authentication methods are crucial for security | The implementation of multi-factor authentication, device registration, and context-based risk assessment strengthens security against unauthorized access and potential vulnerabilities during the authentication process. |
| Adapting to emerging technologies is necessary for effective deployment | Continuous evaluation and updating of captive portal strategies to incorporate evolving security technologies and regulatory requirements is essential for maintaining effective network access management. |
Understanding What is a Captive Portal
A captive portal is a network security mechanism that intercepts web traffic and requires users to interact with an authentication page before gaining full network access. TechTarget defines it as a web page users must engage with before accessing a wireless network, typically found in public spaces like cafes, airports, hotels, and corporate environments.
The Core Mechanics of Captive Portals
At its fundamental level, a captive portal acts as a gatekeeper for network access. When a device attempts to connect to a Wi-Fi network, it is automatically redirected to a web page that requires some form of interaction. This interaction could involve entering a password, accepting terms of service, providing contact information, or completing a brief registration process.
The technical implementation involves sophisticated network routing. IETF RFC 8952 explains that captive portals typically modify HTTP or DNS traffic to intercept and redirect user connections. This means that even before a user can browse the internet, they must first pass through this digital checkpoint, which serves multiple critical functions including authentication, data collection, and network security.
Authentication and Security Considerations
While captive portals provide a layer of network control, they also present unique security challenges. UK Government Cybersecurity Guidelines highlight that these systems can potentially require devices to temporarily disable security measures like VPNs during the authentication process, which could expose users to potential network vulnerabilities.
Network managers must carefully design captive portal experiences that balance security requirements with user convenience. This involves creating intuitive authentication interfaces, implementing robust backend verification processes, and ensuring that the portal does not become an unnecessary barrier to network access.
For organizations seeking advanced captive portal solutions, read more about our Cisco Meraki authentication strategies that provide seamless and secure network onboarding experiences.
The evolution of captive portals continues to be driven by increasing demands for network security, user experience, and sophisticated authentication methods. Modern implementations go beyond simple password checks, incorporating multi-factor authentication, social media login options, and detailed user analytics to provide a comprehensive network access management solution.
How Captive Portals Work in Different Industries
Captive portals have become essential network management tools across diverse industries, each leveraging the technology to address unique operational requirements and security challenges. Market Research Analysts indicate that industry-specific implementations of captive portals are rapidly evolving to meet complex access control and user engagement needs.
Hospitality and Guest Network Management
In the hospitality sector, captive portals transform internet access from a basic utility to a strategic engagement platform. Hotels, resorts, and restaurants use these systems to create personalized guest experiences while gathering valuable demographic data. When guests connect to Wi-Fi, they are typically presented with a branded portal that not only authenticates their access but also promotes hotel amenities, local attractions, or special offers.
The authentication process can be tailored to specific requirements. Some properties implement social media login options, allowing guests to connect quickly using existing accounts. Others require email registration, which enables future marketing communications and helps build customer databases. Research from Hospitality Technology suggests that well-designed captive portals can increase guest satisfaction and provide actionable insights into visitor preferences.
Educational and Enterprise Network Controls
Educational institutions and corporate environments utilize captive portals as critical network security and policy enforcement mechanisms. Universities can create granular access controls that differentiate between student, faculty, and guest network permissions. This approach ensures that network resources are allocated efficiently and that usage complies with institutional policies.
Enterprise implementations often integrate advanced authentication methods. Multi-factor authentication, device registration, and detailed access logging become standard features. Cybersecurity Research emphasizes the importance of robust authentication in preventing unauthorized network access and protecting sensitive organizational data.
Transportation and Public Space Network Access
Transportation hubs like airports, train stations, and public venues have unique network access requirements. Captive portals in these environments serve multiple functions beyond simple internet connectivity. They can provide real-time travel information, emergency alerts, and location-specific services while managing network bandwidth and ensuring fair usage.
For advanced Cisco Meraki network solutions that power seamless authentication experiences, organizations can implement sophisticated access strategies that balance user convenience with robust security protocols.
The versatility of captive portals demonstrates their critical role in modern network management. By providing customizable, secure, and intelligent access control, these systems enable organizations across industries to transform internet connectivity from a simple utility into a strategic asset for user engagement, data collection, and operational efficiency.
To help clarify how different industries leverage captive portals, the following table summarizes use cases and specific features mentioned in the content.
| Industry | Primary Use Case | Authentication Methods | Additional Functions |
|---|---|---|---|
| Hospitality | Personalized guest internet access & engagement | Social media login, Email reg. | Promotes amenities, collects guest data |
| Education | Granular network access control | Multi-factor, Device reg. | Differentiates user types, policy enforce |
| Enterprise | Secure organizational access | Multi-factor, Device reg. | Access logs, protect sensitive data |
| Transportation | Public access, information delivery | Quick guest/portal login | Real-time alerts, travel updates, bandwidth mgmt |
Key Benefits and Challenges of Captive Portals
Captive portals represent a complex network management solution with significant advantages and potential drawbacks. Uplevel Systems highlights that these systems provide network administrators with powerful tools for controlling and monitoring network access while creating opportunities for user engagement and data collection.
Security and Access Control Benefits
One of the primary advantages of captive portals is their robust security framework. By requiring explicit user authentication, these systems create a critical first line of defense against unauthorized network access. Network managers can implement multi-layered security strategies that go beyond traditional password protection. This includes options like multi-factor authentication, device registration, and detailed access logging.
The ability to create granular access controls enables organizations to implement precise network permissions. For instance, a university can differentiate access levels between students, faculty, and guests, ensuring that network resources are allocated efficiently and securely. Electronic Frontier Foundation notes that while these systems enhance security, they also introduce potential complexity in network management.
Potential Vulnerabilities and User Experience Challenges
Despite their benefits, captive portals are not without significant challenges. Wikipedia’s Cybersecurity Research reveals several potential exploitation methods that network managers must carefully address. These include DNS tunneling and MAC address spoofing, which can potentially compromise network security.
User experience represents another critical consideration. Intrusive authentication processes can frustrate users and create barriers to network access. Network managers must design portals that balance security requirements with user convenience. This involves creating intuitive interfaces, minimizing authentication steps, and providing clear guidance throughout the connection process.
Strategic Implementation and Risk Mitigation
Successful captive portal deployment requires a strategic approach that considers both technological capabilities and user expectations. Organizations must continuously evaluate and update their authentication mechanisms to address emerging security threats. This might involve implementing adaptive authentication techniques that adjust security protocols based on user behavior and risk indicators.
For educational institutions seeking advanced network management solutions, explore our specialized education network authentication strategies that provide comprehensive access control and security frameworks.
The evolution of captive portals demonstrates the ongoing tension between security requirements and user accessibility. Network managers must remain agile, adapting their strategies to incorporate emerging technologies while maintaining robust protection against potential security threats. By understanding both the strengths and limitations of captive portals, organizations can develop more effective and user-friendly network access strategies.
To summarize the key benefits and challenges discussed above, the following table organizes them for quick comparison.
| Aspect | Benefits | Challenges |
|---|---|---|
| Security | Multi-factor authentication, granular control, logging | Exploits like DNS tunneling, MAC spoofing |
| Accessibility | Differentiated user access levels | User frustration if process is too complex |
| Engagement | Data collection, targeted promotions | Maintaining convenience vs. data gathering |
| Compliance | Detailed audit trails, policy enforcement | Keeping up with regulatory changes |
Best Practices for Setting Up a Captive Portal in 2025
As network environments become increasingly complex, implementing a captive portal requires strategic planning and advanced technological considerations. The Tech Security Consortium emphasizes that successful captive portal deployment in 2025 demands a holistic approach that balances security, user experience, and technological flexibility.
Authentication and Security Architecture
Modern captive portal implementations must prioritize robust multi-factor authentication strategies. Network managers should design authentication workflows that incorporate diverse verification methods, including biometric validation, device fingerprinting, and adaptive risk assessment. Cybersecurity Experts recommend implementing contextual authentication mechanisms that dynamically adjust security protocols based on user behavior, device characteristics, and network environment.
Critical security considerations include encryption protocols, SSL/TLS certificate management, and comprehensive logging mechanisms. The Tech Cyber Life highlights the importance of enabling HTTPS encryption to mitigate risks such as eavesdropping and potential man-in-the-middle attacks. Network administrators must ensure that all authentication processes are conducted through secure, encrypted channels to protect user credentials and sensitive information.
User Experience and Design Principles
Effective captive portals in 2025 transcend traditional authentication mechanisms by creating intuitive, engaging user interfaces. Design principles should focus on minimizing friction during the login process while maintaining comprehensive security protocols. This involves creating responsive, mobile-friendly authentication pages that adapt seamlessly across different device types and screen sizes.
Implement streamlined authentication options such as social media login, single sign-on integrations, and guest access workflows that provide rapid network entry without compromising security standards. The goal is to create an authentication experience that feels effortless and professional, reducing user frustration and potential abandonment rates.
Advanced Configuration and Compliance Strategies
Network managers must develop captive portal configurations that align with emerging regulatory requirements and industry-specific compliance standards. This involves creating granular access control mechanisms that can differentiate between user roles, implement time-based access restrictions, and generate comprehensive audit trails.
For organizations seeking cutting-edge network authentication solutions, discover our advanced Cisco Meraki network configuration strategies that provide comprehensive and flexible access management frameworks.
Successful captive portal implementation in 2025 requires a forward-thinking approach that anticipates technological shifts. Network managers must remain adaptable, continuously evaluating and updating their authentication strategies to address emerging security challenges while maintaining an optimal user experience. By integrating sophisticated authentication technologies, prioritizing user-centric design, and maintaining rigorous security standards, organizations can create captive portal solutions that are both robust and user-friendly.
Frequently Asked Questions
What is a captive portal?
A captive portal is a network security mechanism that intercepts web traffic, requiring users to interact with an authentication page before gaining full access to a wireless network. It’s commonly used in public spaces and businesses.
How do captive portals improve network security?
Captive portals enhance network security by requiring explicit user authentication, which serves as a barrier against unauthorized access. They can also implement advanced security measures like multi-factor authentication.
What are the main uses of captive portals in different industries?
Captive portals are widely used in hospitality for personalized guest experiences, in education for controlling access levels among users, and in transportation for providing public information while managing network bandwidth.
What challenges do captive portals present?
Captive portals can create user experience challenges if authentication processes are too complex, potentially frustrating users. They also face security vulnerabilities that need continuous management to protect against exploits like DNS tunneling.
Unlock Complete Control and Security for Your Network in 2025
Network managers like you face constant challenges with balancing security, user experience, and compliance when deploying captive portals. The article highlights the need for strong authentication, seamless onboarding, and adaptable control across different industries. If the thought of combating emerging security threats and handling complex authentication processes keeps you up at night, you are not alone.
Explore all our customizable captive portal solutions perfectly built to address your pain points. Splash Access makes it easy to roll out cloud-managed guest Wi-Fi, granular authentication, and advanced analytics while leveraging your Cisco Meraki infrastructure. Gain peace of mind with multi-factor authentication, secure guest onboarding, and real-time user insights that help you adapt with confidence to new network demands.
Take action now to enhance your network’s security and user satisfaction. Visit Splash Access or see our industry-leading solutions for captive portal management and secure your digital gateway for 2025 and beyond.
Recommended
- Splash Access | Cisco Meraki Solutions | WiFI | Camera | Splash Access
- Elevate Your Cisco Meraki Network with SplashAccess for Captive Portals & Authentication | Splash Access
- EducationPortal | Splash Access
- Cisco User Defined Network with Splash and ISE | Splash Access
- Cisco Meraki Radius Serverwith Group Policy | Splash Access
- Do It Yourself | Splash Access