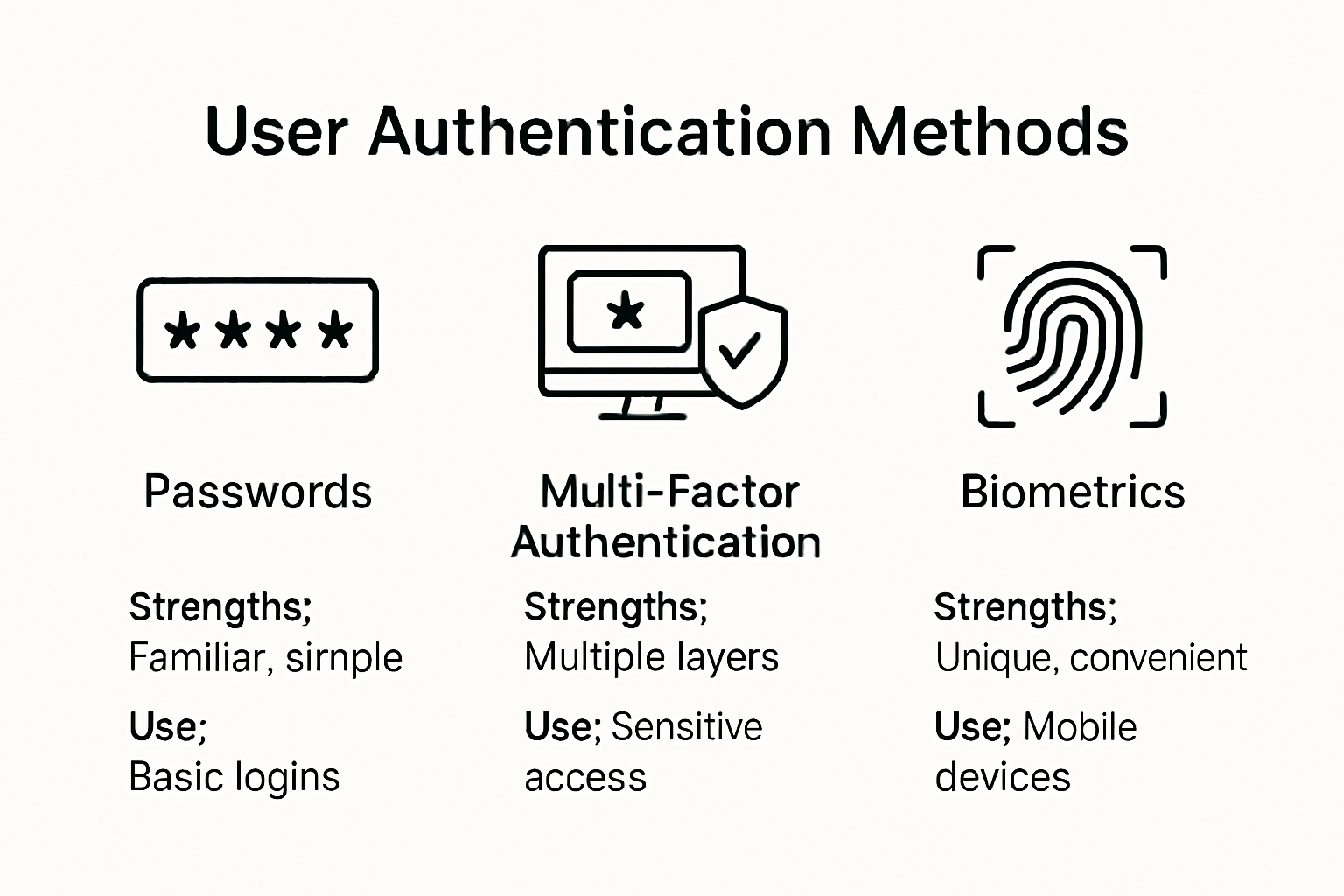
User authentication is getting a serious upgrade as cyberattacks grow more crafty every year. Multi-factor authentication can block up to 99.9 percent of automated account hacks, according to cybersecurity studies. That sounds like a magic bullet. Yet, adopting the wrong method can leave even the biggest organizations wide open. The smartest IT leaders are turning to adaptive, AI-powered systems that rewrite the rules before hackers can even step in.
Table of Contents
Quick Summary
| Takeaway | Explanation |
| Adopt Multi-Factor Authentication (MFA) | Implementing MFA significantly decreases unauthorized access risks by requiring multiple verification elements, including biometric and hardware token technologies. |
| Utilize Risk-Based and Context-Aware Authentication | Dynamic assessment of contextual factors such as user behavior and geolocation during login attempts enhances security and adaptability in authentication processes. |
| Incorporate AI and Machine Learning | Leveraging AI technologies allows for more sophisticated threat detection and adaptive security measures, ensuring continuous verification and anomaly detection in user authentication. |
| Tailor Authentication Techniques to Industry Needs | Different sectors require specific solutions; for example, healthcare should focus on HIPAA compliance while financial institutions must prioritize advanced cryptographic verification. |
| Establish Foundational Security Principles | Develop robust frameworks that enforce the principle of least privilege, continuous verification, and comprehensive password policies to enhance overall authentication security. |
Understanding Modern User Authentication Techniques
User authentication techniques have dramatically transformed in recent years, moving far beyond traditional username and password combinations. Modern organizations require sophisticated approaches that balance robust security with seamless user experience across multiple digital platforms.
The Evolution of Authentication Strategies
Traditional authentication methods have become increasingly vulnerable to sophisticated cyber threats. Password-based systems often represent significant security risks, with research from NIST revealing that static credentials are easily compromised. Modern user authentication techniques now incorporate advanced technological approaches that dynamically verify user identities.
Risk-based authentication has emerged as a critical strategy for intelligent security management. According to academic research from Cornell University, these techniques evaluate multiple contextual factors during login attempts. By analyzing device information, geolocation, user behavior patterns, and network characteristics, organizations can create adaptive authentication frameworks that respond intelligently to potential security threats.
Multi-Factor Authentication Technologies
Multi-factor authentication represents a significant advancement in user authentication techniques. These approaches require users to provide multiple verification elements, substantially reducing unauthorized access risks. Key technologies include:
-
Biometric Verification: Utilizing unique physical characteristics like fingerprints, facial recognition, and retinal scans
-
Hardware Tokens: Physical devices generating time-sensitive authentication codes
-
Behavioral Authentication: Analyzing typing patterns, mouse movements, and interaction rhythms
WebAuthn standards have revolutionized passwordless authentication by enabling robust public-key cryptography mechanisms. These standards allow organizations to implement secure, device-native authentication processes that eliminate traditional password vulnerabilities.
Emerging Authentication Paradigms
Emergent user authentication techniques are increasingly leveraging artificial intelligence and machine learning algorithms. These technologies enable more sophisticated threat detection and user verification processes. By continuously learning and adapting to new potential security risks, AI-powered authentication systems can provide dynamic, context-aware security mechanisms.
Zero trust authentication models have gained significant traction, fundamentally changing how organizations approach network and system access. Instead of assuming trust based on network location, these models require continuous verification for every access attempt. This approach ensures that user authentication is not a one-time event but an ongoing, dynamic process that adapts to changing risk environments.
As cyber threats become more complex, user authentication techniques will continue evolving. Organizations must remain agile, adopting flexible frameworks that can quickly respond to emerging security challenges while maintaining seamless user experiences. The future of authentication lies in intelligent, adaptive systems that balance robust security with user convenience.
Here is a comparison table summarizing the key authentication methods, their security levels, and main features discussed in the “Popular Authentication Methods Compared” section:
| Authentication Method | Security Level | Key Features/Technologies |
| Password-Based | Low | Simple setup, highly vulnerable |
| Biometric Authentication | High | Uses fingerprints, facial/retinal recognition |
| Token-Based Authentication | High | Uses hardware/software tokens, time-sensitive codes |
| Risk-Based Authentication | High (Adaptive) | Context-aware, dynamic analysis |
| Multi-Factor Authentication (MFA) | Very High | Combines multiple verification elements |
| Zero Trust Authentication | Very High | Continuous verification, no inherent trust |
Popular Cisco Authentication Methods Compared
Authentication methods have become increasingly sophisticated, offering organizations diverse strategies to protect digital assets while maintaining user accessibility. The complexity of modern security environments demands a nuanced understanding of various authentication approaches.
Comparative Analysis of Authentication Frameworks
Traditional password-based systems have significant limitations, prompting organizations to explore more robust alternatives. Research from SANS Institute reveals that organizations employing multi-layered authentication strategies experience up to 60% fewer unauthorized access incidents.
Key authentication methods differ substantially in their security models and implementation complexity:
-
Password-Based Authentication: Simple but highly vulnerable
-
Biometric Authentication: Complex and context-dependent
-
Token-Based Authentication: Highly secure but potentially expensive
Risk-based authentication represents a more intelligent approach. According to academic research from Stanford University, these techniques dynamically assess multiple contextual signals during authentication attempts, providing adaptive security mechanisms that respond to potential threats in real time.
Advanced Authentication Technologies Evaluation
Multi-factor authentication (MFA) has emerged as a superior alternative to traditional single-factor methods. By requiring multiple verification elements, MFA significantly reduces unauthorized access risks. WebAuthn standards have particularly revolutionized this domain by enabling robust public-key cryptography mechanisms that eliminate traditional password vulnerabilities.
Biometric authentication technologies offer unique advantages. Fingerprint, facial recognition, and behavioral pattern analysis provide authentication methods that are inherently personal and difficult to replicate. Gartner research suggests that biometric technologies will become the primary authentication method for 70% of enterprise applications by 2025.
Emerging Authentication Paradigms
Zero trust authentication models represent the cutting edge of security strategy. Unlike traditional perimeter-based approaches, these frameworks require continuous verification for every access attempt. This model assumes no inherent trust, even within organizational networks, and mandates rigorous authentication for each interaction.
Artificial intelligence is transforming authentication technologies. Machine learning algorithms can now detect subtle behavioral anomalies, creating dynamic authentication systems that adapt to evolving threat landscapes. Learn more about our advanced authentication solutions for comprehensive security management.
Choosing the right authentication method requires careful consideration of organizational needs, technological infrastructure, and risk tolerance. As cyber threats become increasingly sophisticated, authentication strategies must remain flexible, intelligent, and user-centric. The most effective approaches will seamlessly balance robust security protocols with intuitive user experiences.
Below is a summary table outlining industry-specific authentication requirements and recommended techniques, as described in the “Choosing the Right Technique for Your Industry” section:
| Industry/Sector | Key Authentication Needs | Recommended Techniques |
| Healthcare | HIPAA compliance, secure patient data | MFA, Biometric Verification |
| Financial Institutions | Transaction security, fraud prevention | Risk-Based, Behavioral Biometrics, Cryptographic Verification |
| Education/Research | Balance openness and security | Flexible systems, Passwordless (WebAuthn) |
| Retail & Hospitality | User-friendly experience, security | Passwordless (biometrics), MFA |
Choosing the Right Technique for Your Industry
Selecting appropriate user authentication techniques requires a strategic approach that considers industry-specific security requirements, operational complexity, and user experience. Different sectors demand unique authentication frameworks tailored to their specific technological and regulatory environments.
Authentication Strategies Across Critical Sectors
Each industry presents distinct challenges that influence authentication method selection. Research from Gartner highlights the critical importance of matching authentication techniques to specific organizational needs.
Healthcare organizations, for instance, require stringent authentication methods that comply with HIPAA regulations. Multi-factor authentication becomes essential, with biometric verification providing an optimal balance between security and accessibility. Hospitals and medical facilities must implement solutions that protect sensitive patient data while enabling rapid access for medical professionals.
Financial institutions demand the most rigorous authentication approaches. Banks and financial service providers typically employ:
-
Risk-Based Authentication: Dynamically assessing login attempts
-
Behavioral Biometrics: Analyzing user interaction patterns
-
Advanced Cryptographic Verification: Ensuring transaction security
Industry-Specific Authentication Considerations
Educational institutions and research centers present unique authentication challenges. These environments require flexible systems that balance open academic collaboration with robust security protocols. WebAuthn standards offer promising solutions, enabling secure, passwordless authentication across diverse technological ecosystems.
Retail and hospitality sectors increasingly prioritize user convenience without compromising security. Passwordless authentication methods have gained significant traction, with approximately 62% of organizations already implementing biometric technologies. These approaches simplify user access while maintaining robust security mechanisms.
Strategic Authentication Technology Selection
Choosing the right authentication technique involves comprehensive evaluation of multiple factors:
-
Regulatory compliance requirements
-
Existing technological infrastructure
-
User experience considerations
-
Potential security vulnerabilities
-
Scalability and future adaptability
Learn more about our customized authentication solutions that address industry-specific challenges.
Artificial intelligence and machine learning are transforming authentication strategies, enabling more adaptive and intelligent verification processes. Organizations must remain agile, continuously reassessing their authentication frameworks to address emerging technological and security landscapes.
Ultimately, successful authentication strategy implementation requires a holistic approach. IT and facility managers must collaborate closely with security experts, understanding that authentication is not a one-size-fits-all solution but a dynamic, evolving ecosystem tailored to specific organizational needs.
Best Practices for Strong User Authentication
Implementing robust user authentication requires a comprehensive and strategic approach that goes beyond traditional security measures. Organizations must develop multi-layered authentication strategies that adapt to evolving technological threats and protect critical digital assets.
Foundational Authentication Security Principles
Research from the National Institute of Standards and Technology (NIST) emphasizes the critical importance of developing authentication frameworks that balance security complexity with user accessibility. Effective authentication strategies require a holistic approach that considers multiple dimensions of cybersecurity.
Key foundational principles include:
-
Principle of Least Privilege: Granting users minimal access required for their specific roles
-
Continuous Verification: Implementing ongoing authentication mechanisms
-
Context-Aware Authentication: Dynamically assessing risk factors during access attempts
UK Government Security Guidelines recommend creating comprehensive password policies that enforce complexity and regular rotation. This includes implementing minimum password length requirements (15 characters for high-value accounts) and mandating combinations of uppercase, lowercase, numeric, and special characters.
Advanced Authentication Implementation Strategies
Multi-factor authentication (MFA) represents a cornerstone of modern security approaches. Cybersecurity research indicates that implementing MFA can block up to 99.9% of automated account compromise attempts.
Key MFA implementation strategies include:
-
Combining multiple verification methods
-
Utilizing biometric and hardware token technologies
-
Implementing adaptive authentication frameworks
Biometric authentication technologies offer unique advantages in creating more secure and user-friendly authentication experiences. Facial recognition, fingerprint scanning, and behavioral pattern analysis provide inherently personal verification methods that are significantly more difficult to compromise.
Continuous Security Management
Authentication is not a static process but a dynamic, ongoing security practice. Organizations must develop robust mechanisms for:
-
Regular access rights review
-
Prompt credential revocation
-
Continuous monitoring of authentication attempts
Learn more about our advanced authentication solutions designed to address complex security challenges across various industries.
Artificial intelligence and machine learning are increasingly integrated into authentication systems, enabling more sophisticated threat detection and adaptive security mechanisms. These technologies can analyze subtle behavioral patterns, detect anomalies, and respond to potential security risks in real time.
Successful user authentication requires a proactive, comprehensive approach that combines technological solutions, user education, and continuous adaptation. IT and facility managers must remain vigilant, understanding that authentication is an evolving ecosystem demanding constant refinement and strategic thinking.
Frequently Asked Questions
What are the top user authentication techniques for 2025?
The top user authentication techniques for 2025 include multi-factor authentication (MFA), risk-based and context-aware authentication, biometric verification, and AI-powered systems. These techniques balance robust security with user experience to combat sophisticated cyber threats.
Why is multi-factor authentication important?
Multi-factor authentication is crucial because it significantly reduces the risk of unauthorized access by requiring users to provide multiple verification elements, such as passwords, biometric data, or hardware tokens. This multifaceted approach enhances security against account compromises.
How does risk-based authentication work?
Risk-based authentication evaluates various contextual factors during login attempts, such as user behavior, geolocation, and device information. This dynamic assessment allows organizations to adaptively enhance security measures based on perceived risk levels during access attempts.
What role does AI play in user authentication?
AI plays a significant role in user authentication by enabling sophisticated threat detection and adaptive security mechanisms. Machine learning algorithms can analyze user behaviors, detect anomalies, and continuously improve authentication processes, ensuring a more secure environment.
Secure Every Connection. Seamless Onboarding with Splash Access
IT and facility managers know that simply relying on basic passwords is no longer enough. The article highlights how threats are evolving and stresses the urgency of adopting adaptive multi-factor authentication and context-aware systems. If you worry about data breaches or struggle to manage guest access without slowing business, you are not alone. Many leaders face the same tension between airtight security and effortless network access.
Splash Access brings together biometric authentication, QR onboarding, and risk-based access controls into one cloud-driven platform purpose-built for organizations like yours. Make your network future-ready with enterprise-grade multi-factor authentication and seamless Meraki integration. Do not wait for an account breach to rethink your approach. Visit Splash Access now and see how you can protect your users and gain peace of mind with powerful, AI-enhanced authentication that scales as you grow.